Table of Contents
Wide Adoption Have Not Started


Crypto Debit and Credit Cards
Fiat Digital Wallet
Find other adoptions and leave a comment if you know more.
Centralized/Custodial Exchanges
Remittance Example
Exchange to StartMy home country is Indonesia where I have most of my identifications and accounts and most likely I will stay there often so for my case I will register for cryptocurrency exchanges in Indonesia such as Indodax, Tokocrypto, Upbit, Luno (input "S24B5E" in referral to get your bonus), Pintu (input "FAJAR199" in referral to get your bonus), Zipmex, Tokenomy. If you are staying in your home country then you can finish your starting phase up to this point but for me, I'm currently studying in Japan therefore, is a good choice and also an opportunity to register to exchanges in Japan. For now only registered in Coincheck, and BTCBOX (input "HNRCWSLFLF" in referral to get your bonus). Why should you start with the closest first? Because they are centralized or custodial which means you are giving your funds to them and trusting them that they will manage your fund properly. The moment you give them your funds, they can take it and use it as they wished, which is why trust is very important and is the weakness to the current system compared to the new decentralized system. There are many variables that builds trust such as being regulated, many users, good reviews, clean history, and among them is physically close to your distance where if anything happens to your funds, you can just visit their office. Example Usage GuideActually this post is for my friends and maybe potential future seminars that I will host to introduce cryptocurrency to new people. I will give an example guide of using one of the exchanges in my home country which is Indodax and one of the exchanges in my country of residence which is Coincheck. However, once you know how to use one of them, you mostly likely can use the rest with few difference because they may introduce different functions but the basics are:
Finally, the fees that you need to check whether there is or not:
You can check on their websites because they can change for example Indodax's fees: https://help.indodax.com/bagaimana-rincian-fee-di-indodax-com/ and Coincheck's fees: https://coincheck.com/info/fee. Simple Indodax GuideIndodax Registration

Indodax Verification


Indodax Deposit and Withdraw


I also made a video of depositing IDR from OVO digital wallet if you are interested:

Here I successfully withdrawn my IDR to my Bank Negara Indonesia (BNI) account. In Indodax, the IDR withdrawal is fast where for me took only an hour or two but the fees are high which is 1% and minimum 25k IDR.
Another example is that I withdraw using Luno (input "S24B5E" in referral to get your bonus). It's cheap with only 6.5k IDR but took almost 3 business days although they stated that it should only took 1 business day.

My example of directly withdrawing Raven Coin that I mined in MiningpoolHub.
Check Other Menus
Market



Simple Coincheck GuideCoincheck Registration
Coincheck Verification

Coincheck Deposit and Withdraw
I also made a video of depositing JPY from Japan Post Bank for foreigners in Japan:


I made an example of transferring coin from Coincheck to Indodax and also possible fees if remmitting JPY to IDR from Japan to Indonesia:
MarketIf you prefer my video explaination:



Check Other MenusMirrors
4 Comments
Air Swap InstantCall the following JavaScript: <script src="https://cdn.airswap.io/airswap-instant-widget.js"></script> Call Air Swap Instant: <button onclick="myAirSwapInstant()">AirSwapInstant</button> <script> function myAirSwapInstant(){ window.AirSwapInstant.render( { onClose: function () { console.info('Widget closed.') }, }, 'body', ) } </script> Air Swap TraderCall the following JavaScript: <script src="https://cdn.airswap.io/1.3.0/airswap-trader.js"></script> Call Air Swap Trader<button onclick="myAirSwapTrader()">AirSwapInstant</button> <script> function myAirSwapTrader(){ window.AirSwapTrader({ onCreate: (order, cid) => { console.log('Order created!') }, onClose: (transactionHash) => { console.log('Widget closed') }, }).render('body') } </script> Source: https://docs.airswap.io/take-liquidity/embed-airswap Add this to the head tag <link rel='stylesheet' href='https://widget.kyber.network/v0.7.5/widget.css'> Add this to the end of body tag. <script async src='https://widget.kyber.network/v0.7.5/widget.js'></script> This is the 'Pay with tokens' button, place it anywhere on your webpage. You can add multiple buttons into a same page <a href='https://widget.kyber.network/v0.7.5/?type=pay&mode=popup&title=Donate%20to%20Fajar%20Purnama&lang=en&receiveAddr=0xCf354A0012160bC5dAe441C49f0B2d7E4A4fFC96&receiveToken=KNC&receiveAmount=1&callback=https%3A%2F%2Fkyberpay-sample.knstats.com%2Fcallback¶mForwarding=true&commissionId=0xCf354A0012160bC5dAe441C49f0B2d7E4A4fFC96&theme=theme-dark' class='kyber-widget-button theme-dark theme-supported' name='KyberWidget - Powered by KyberNetwork' title='Pay with tokens' target='_blank'>Pay with tokens</a> This is the 'Swap tokens' button, place it anywhere on your webpage. You can add multiple buttons into a same page. <!-- This is the 'Swap tokens' button, place it anywhere on your webpage --> <!-- You can add multiple buttons into a same page --> <a href='https://widget.kyber.network/v0.7.5/?type=swap&mode=popup&title=Kyber%20Network%20Swap%20Widget&lang=en&callback=https%3A%2F%2Fkyberpay-sample.knstats.com%2Fcallback¶mForwarding=true&commissionId=0xCf354A0012160bC5dAe441C49f0B2d7E4A4fFC96&theme=theme-dark' class='kyber-widget-button theme-dark theme-supported' name='KyberWidget - Powered by KyberNetwork' title='Pay with tokens' target='_blank'>Swap tokens</a> This is the 'Buy token' button, place it anywhere on your webpage. You can add multiple buttons into a same page. <a href='https://widget.kyber.network/v0.7.5/?type=buy&mode=popup&title=Buy%20Something&lang=en&receiveToken=KNC&receiveAmount=1&callback=https%3A%2F%2Fkyberpay-sample.knstats.com%2Fcallback¶mForwarding=true&commissionId=0xCf354A0012160bC5dAe441C49f0B2d7E4A4fFC96&theme=theme-dark' class='kyber-widget-button theme-dark theme-supported' name='KyberWidget - Powered by KyberNetwork' title='Pay with tokens' target='_blank'>Buy token</a> Source: https://developer.kyber.network/docs/WidgetGenerator 
Bare MinimumAll wallets should have coin send and receive function. This section is for starters who have not used cryptocurrency wallet before. If you have, you may skip this section. Although I believe that I should never recommend anyone to only buy bitcoin and altcoins, I strongly recommend everyone to have cryptocurrency wallet. The most minimum of all to enter cryptocurrency is to have an interface to receive coins and that is a wallet. I believe that a future will come where many people will need bitcoin and altcoins and there's no safer way to get some other than having a wallet or at least a public/receiving address. In my experience, most of the people I have introduced bitcoin who did not have computer literacy background, have trouble even figuring out of how to receive coins. 
The other bare minimum function is to send coins. Nowadays the age of cryptocurrency adoption have not come so the send function is not used much. If cryptocurrency becomes widely adopted one day, the knowledge of how to carefully send is necessary with current system. The transaction is irreversible, one wrong character when inputing address will result in forever coin lost. Does Atomic Wallet have these foolproof functions?

Operating SystemsPeople use different operating systems so if Atomic Wallet only supports few operating systems, it will be difficult to refer. So, what does Atomic Wallet support:
Referral Program
Private Keys or Seed PhrasesThis is a very important thing that anyone who dives into cryptocurrency must know. Basically, not your keys, not your coins. If a 3rd party holds your private keys or seed phrases means they have full control over your coins. Like the current banking system, do you trust them or not? Is Atomic Wallet a third party online bank or your own bank?

Supported Coins and Tokens 

In Wallet Staking
In Wallet Exchange

Features Not Yet Available
Mirror
About being light weight or not, I'm not sure since everything is running well on my devices and I haven't tried on lower spec devices such Raspberry Pi and old smartphones. Leave a comment if you know more and I will update this post. NoteIf you just want to see the mouse tracking demonstration, it is available of most of my blogs that I can write JavaScript in, and the source code is on Github. The original article is copyright under © Springer Nature Switzerland AG, Part of Springer Nature:
This is Author's pre-print which is the submitted version or before the peer review process. The copyright was transferred from Fajar Purnama to Springer Science+Business Media, LLC, part of Springer Nature and stated in the copyright transfer that "Author(s) retain the right to make the pre-print available on their own personal, self-maintained website. Springer not only encourages pre-print sharing, but even allow to license it as creative commons, therefore I license this post as customized CC-BY-SA where you are also allowed to sell my contents but with a condition that you must mention that the free and open version is available here. In summary, the mention must contain the keyword "free" and "open" and the location such as the link to this content. As I am the author, I can say that there is significant difference between before and after peer review version. Springer is kind enough to allow sharing of the authors' accepted version (AAM) 12 months after publication which will be 6 March 2021. However, we can open it faster if you are interested. Springer offers open access/CC-BY at a price where for this article, it costs €2170, $2750 or £1,870. For example, anyone can freely republish my previous article because it is open access. You are able to donate in cryptocurrency (includes BAT and bittube), paypal, alipay, JavaScript mining, etc, and I will apply for open access once threshold is reached where I will store the donation in a crypto wallet and I will show the balance on a webpage. I do highly recommend to contact me before donating where you can find my social media links on my donation page but with technology today, I cannot stop you from donating so make sure to contact me so that I can list you on the donator list. Beware of scams, my recommendation is to contact me and book or delay your donation. Once enough people are interested, I will contact you back on the same exact window. If there's a comment section here, you can book your donation in the comment AbstractMouse tracking serves as an alternative to eye tracking in measuring the learning process in education because of its affordability. Moreover, mouse tracking does not require extra hardware, as in the case of eye tracking, because it is a feature in personal computers by default. Therefore, it is possible to implement mouse tracking in a massive open scale. However, mouse tracking has only been implemented in a laboratory setting to date, ostensibly because of the associated extremely high running costs. Nonetheless, there is no available data to support the claim of high resource costs, which has resulted in much speculation among implementers. In general, the implementation of mouse tracking in a non-laboratory environment is still rare. Therefore, the authors developed an application to investigate real-time mouse tracking online. It was implemented on the Moodle learning management system and tested on an online quiz session accessed abroad. Additionally, the application can handle tracking on mobile devices. In this work, the main resources that include CPU, network, RAM, and storage costs were measured when mouse tracking was used. These results can serve as a reference for network and server administrators during future implementation of this technique. It was determined that the characteristics of mouse activities were dynamic in that occasional surges and lulls were observed. If mouse tracking data are not aggregated and transmitted as a single data package, then mouse tracking can be implemented on a large scale. IntroductionWith the recent advances in technology, including the Internet, information can be searched and published with few restrictions. With the advancement in information communication technology (ICT), more activities are being conducted online. Individuals no longer spend hours staring at computer screens after work or class; instead, they often use their mobile devices to stay online irrespective of the time or their physical location. (Dentzel, 2013). Unlike in the past where individuals were limited to local newspapers, televisions, and textbooks, people can now easily search and choose the information they want using advanced search engines such as Bing, DuckDuckGo, Google, and Yahoo. In the case of social networking services (SNS) such as Facebook, Instagram, Line, and Twitter, individuals can get the latest news, interact with one another, open discussions, and share information. Users can enjoy entertainment such as viewing photographs, listening to music, and watching videos using services such as Dailymotion, Metacafe, and Youtube. In addition, video games are also available. Shopping is also facilitated by online merchants such as Aliexpress and Amazon, where individuals can order items and have them delivered. All of these online activities can be performed using a computer device connected to the Internet. Education has also benefitted from the Internet and courses can be delivered blended (Paturusi et al., 2012) or fully online (Wen and Rosé, 2014). A variety of learning and teaching activities can be performed outside the classroom, for example, the reading of learning material, discrete discussion in forums, submission of assignments, and the performance of exercises (Linawati et al., 2017). This greatly reduces the burden on both students and teachers. The number of higher education institutions that provides online education is increasing, and it is only a matter of time before primary and secondary schools (Sopu et al., 2016) follow this model. Implementing an online course is currently much easier than in the past because of the advent of learning management systems (LMS) where most processes are automated (Kakasevski et al., 2008) without the need for advanced knowledge on computers and web programming (Chourishi et al., 2011); only computer literacy is a prerequisite. The next step after implementing online courses is the implementation of massive open online courses (MOOC) (Drake et al., 2015). Unlike regular online courses, everyone can join MOOC, which is not limited to students of certain institutions. With the option of numerous online activities, many studies have become interested in analyzing these activities in an area known as online analytics. Online analytics records who, where, and when associated with online activities. The most popular metrics are total traffic, source traffic, bounce rate (the rate of people immediately leaving the page after visiting), and conversion rate (whether the page fulfills its purpose) (Bluehost, 2016). Whether it is a public website or an online course, the concept is almost the same. On a public website, the number of page views, comments, ratings, image views, videos played, and items bought are recorded. Based on page views only, a variety of analyses can be performed. A page view can predict a user’s demographic (Hu et al., 2007), characterize an audience in terms of preference for news, multimedia, games, or adult content (Kumar and Tomkins, 2010). It can also predict whether a user is at risk on visiting malicious websites (Canali et al., 2014). Page views also provide hints on how to improve a website’s design, for example moving popular webpage links to the header (Khan et al., 2018). There are already many web analytics software available such as Google Analytics, Open Web Analytics, Piwik, and Cloudflare (spa, 2019). In online courses, logins, learning materials viewed, discussions, assignments submissions, quizzes attempt, and grades are recorded (moo, 2016). They can reveal for example a student’s level of activity (Nandi et al., 2011), how difficult the quizzes are for students (Nakano et al., 2005; Usagawa et al., 2006), and even identify failing students (Fungai and Usagawa, 2016). Usually, these data are used to measure the learning performance of students (Wen and Rosé, 2014). Although those popular metrics can measure learning performance, there is a limit when it comes to measuring the actual learning process (Zushi et al., 2012). As such, the what, when, and where can be measured in detail, but not the how (Purnama et al., 2016a). To obtain more detailed measurements, it is necessary to record the time spent viewing a page (Li and Tsai, 2017). To obtain detailed information, the time spent viewing each section of a page can be recorded (Koh et al., 2018). One of the most common approaches is to divide a page into subpages (Lee et al., 2009) or to insert tracker codes into sections of the page (Purnama et al., 2016b). More powerful approaches involve eye-tracking (Pernice, 2017) and mouse tracking (Henrie et al., 2015; Koh et al., 2018), which can provide more information than just time spent viewing particular sections. Eye tracking is arguably one of the most accurate methods for recording the viewing activity of users, but the financial cost is very high, thereby confining the technology to lab environments (Lai et al., 2013). Although mouse tracking is not as accurate, the financial cost is low in comparison. No additional devices are needed to perform mouse tracking, which can be implemented by anyone who has a computer. Most people own computers and with the increasing availability of the Internet, it is possible to perform massive scale mouse tracking implementation (Huang et al., 2011). Therefore, mouse tracking can be implemented outside of the laboratory in places such as classrooms, online learning, and websites. Recently, web mouse tracking software such as Mouseflow, ClickTale, ClickHeat, and Sessioncam has emerged (NT, 2015). Unfortunately, another obstacle must be overcome before widespread implementation of mouse tracking can be achieved. This is related to the resource cost, especially for personal implementation. It is rumored that the resource cost for maintaining mouse tracking (eye tracking as well) is notoriously high, and therefore classified as Big Data (Sin and Muthu, 2015). However, the rumors were not confirmed. Furthermore, mouse tracking resource cost was never discussed in detail. Leiva and Huang (2015) state that a mouse swipe from left to right can generate hundreds of cursor coordinates and a mouse activity over a minute can generate 1 MB (megabyte) of data. That is the only information related to mouse tracking resource cost that was presented in their article. Discussions on these matters are very few, which has been unhelpful to implementers. Therefore, this work investigates the popular resource costs of mouse tracking including a computer processing unit (CPU), data rate, random access memory (RAM), and storage. A real-time online mouse tracking application was developed that can be implemented on any website. In this case, it was demonstrated on a quiz session on Moodle LMS. The source code is available on Github (Authors, 2019a). The implementation and resource measurement took place for three events: solo measurements in a laboratory, local testing by five people of a quiz session in a laboratory, and an overseas quiz session by students of classroom size in Mongolia, accessing a server in Japan. This article is divided into six chapters. The first chapter is the introduction that includes background information on online activities and popular analytics, mouse tracking, and the problem of mouse tracking implementation as previously described. The second chapter is the literature review in which the results of several interesting studies in the field of eye tracking and mouse tracking are presented. Mainly, this chapter shows that there are promising results, which have generated interest and excitement, in these fields. The last part of this chapter discusses the state-of-the-art of this work. The third chapter is the system overview that discusses the real-time online mouse tracking application, developed as a part of this work, and mainly considers its operation and features. The fourth chapter is the experiment and implementation that explains the hardware and tools used, subjects, and the procedures of the experiment and their implementation. The fifth chapter presents the results and discussion on the mouse tracking data that was collected, sample analysis, and the resource costs from both calculated and profiled measurements. The sixth chapter is the conclusion, which summarizes the main findings. Literature ReviewEye TrackingRayner (1998) reviewed many articles regarding eye movements spanning from 1971–1998 and claimed that eye tracking technologies existed since then. The most fundamental aspect of eye movements are fixation and saccade, where fixation is the process of fixing the gaze to a certain region of interest (ROI), and saccade is the process of moving the gaze to another ROI. However, it is up to the examiner to interpret eye movements, for example, eye movements can provide information about the user’s attention, interest, and state of mind. Eye tracking has been researched in the field of pattern recognition whether in a non-digital environment (Holmqvist and Wartenberg, 2005; Holsanova et al., 2006) or digital environment (Hyönä et al., 2002; Liu, 2005; Duggan and Payne, 2011; Jarodzka et al., 2017), search engine result page (SERP) (Rodden and Fu, 2007; Rodden et al., 2008; Huang et al., 2011, 2012), web evaluation and usability (Ehmke and Wilson, 2007; Buscher et al., 2009; Tzafilkou and Protogeros, 2017; Hsu et al., 2018), and visual search (Rayner, 2009; Dragunova et al., 2017). In the category of learning, Lai et al. (2013) reviewed eye movement research in seven themes including pattern of information processing, effects of instructional design, reexamination of existing theories, individual differences, effects of learning strategies, patterns of decision making, and conceptual development. They concluded that the eye-tracking method provides a promising channel for educational researchers to connect learning outcomes to cognitive processes. Many educational researchers gained interest in the application of eye tracking in the process of learning and teaching, especially in online learning, which can make up for the lack of emotional connection between students and teachers (Cantoni et al., 2012). For example, eye tracking can capture signs of comprehension difficulties, cognitive stress, or tiredness of students during online learning, which a good teacher is able to perform during face-to-face learning. In e-learning, eye tracking has been integrated into the online framework where the eye tracking hardware captures eye movement on the client, transmits the eye movement data to the server, then processes the data for direct analysis or to implement interactivity. Finally, the data are kept in storage.
Other than being integrated into the online learning framework, eye tracking is often utilized without adaptability and interactivity, simply as a tool to analyze specific characteristics of the learners and to perform post actions based on this analysis (Rakoczi and Pohl, 2012; Lupu and Ungureanu, 2013). Examples of utilizations include obtaining the cognitive (Eger, 2018) and emotional state of the users (Cantoni et al., 2012), evaluation of instructional design (Jarodzka and Brand-Gruwel, 2017; Yang et al., 2018) and user interface design (UID) (Ramakrisnan et al., 2012; Chivu et al., 2018), pattern recognition (Alhasan et al., 2018; Parikh and Kalva, 2018), strategic patterns (Tsai et al., 2012; Busjahn et al., 2014), etc. Until now, eye tracking has yet to be implemented on a large scale because of hardware limitations. Almost all eye tracking articles cited herein are based on experiments in laboratory environments where separate and usually expensive eye tracking hardware is utilized. Most of these articles express confidence in the eventual reduction in cost and affordability of eye tracking hardware and the expectation that eye tracking will be implemented on a large scale in the future. In recent years, few researchers have attempted to fulfill these expectations, for example, Sungkur et al. (2016) and Zheng and Usagawa (2018) developed eye tracking in web cameras. As almost all modern laptops are equipped with a web camera, and most people including students own laptops, eye tracking in a web camera is a key aspect in the quest for large-scale implementation. Mouse TrackingAlthough most researchers prefer eye-tracking data, many mouse tracking articles have noted that mouse tracking is a viable alternative because eye tracking technology is too expensive and inconvenient (Cooke, 2006). There are investigators who have attempted to correlate mouse tracking to eye tracking by utilizing exploratory studies (Rodden et al., 2008), correlation analysis (Chen et al., 2001; Rodden et al., 2008; Voßkühler et al., 2008; Liebling and Dumais, 2014; Demšar and Çöltekin, 2017), or prediction (Guo and Agichtein, 2010; Johnson et al., 2012; Huang et al., 2012; Navalpakkam and Churchill, 2012) to demonstrate the inaccuracy involved in correlation mouse tracking data to eye tracking data. In contrast, there is also active research that treats mouse tracking data independently (Navalpakkam and Churchill, 2012). There are also other rare studies that attempt to direct the eye gaze to the mouse cursor by restricting the user’s field of vision, thereby coupling the mouse tracking data with the eye tracking data (Tarasewich et al., 2005; Lagun and Agichtein, 2011; Maruya et al., 2015; Kim et al., 2017). Similar to eye tracking, mouse tracking is also conducted in the area of pattern recognition, search engine result page (SERP) (Rodden and Fu, 2007; Rodden et al., 2008; Guo and Agichtein, 2008; Huang et al., 2011, 2012; Lagun et al., 2014; Arapakis and Leiva, 2016), web evaluation and usability (Arroyo et al., 2006; Navalpakkam and Churchill, 2012; Manson et al., 2012), and education. In the field of education, recent articles emphasize the need to record the time spent on a learning activity to obtain the user’s behavior patterns (Li and Tsai, 2017). Koh et al. (2018) emphasize the need to record the time spent on a particular section of a learning activity because the time spent on an entire page does not reflect the actual learning time given that the time spent on different sections varies. The authors further stated that mouse trajectories and scrolling can be used to determine the time spent on a particular section, although the capability of mouse tracking is more than simply being able to determine the time spent on a particular section. Mouse tracking can be used record the trajectories, velocities, and many other variables of the mouse’s cursor that can be used to measure many things including cognitive load (Rheem et al., 2018). However, the data generated by mouse tracking can be overwhelming to examine, although this is no longer a major problem because there are many data mining and visualization applications that can be used to extract meaningful information from the data of the users (Poon et al., 2017). The earliest article on mouse tracking implementation was presented by Mueller and Lockerd (2001), whereas in e-learning, the earliest article was presented around the year 2012.
As shown in the preceding, there are many interesting works on mouse tracking; however, very few have investigated the implementation and resource costs associated with the process, which has caused implementers to doubt the feasibility of large-scale implementation. Huang et al. (2011) conducted a massive scale mouse tracking on Microsoft’s Bing search engine. By reducing the amount of mouse trajectories recorded their massive scale experiment succeeded. However, they only discussed the data analysis afterward and neglected to consider the resource costs. Leiva and Huang (2015) and Martín-Albo et al. (2016) addressed the issue but their discussion quickly shifted to the solution, which is primarily based on compression methods. To date, there are no articles, except this, that consider the resource costs of mouse tracking implementation. Real-time Online Mouse Tracking System OverviewFrameworkThe mouse tracking application developed by the authors was designed to run online and in real-time. Online means that the mouse tracking is run remotely via the Internet where the client runs the mouse tracking application when browsing a webpage and the associated data is sent to the server. Real-time means that the mouse tracking data is continuously sent by the client to the server during the mouse tracking process. Overall, this can be seen in the real-time online mouse tracking framework on Fig. 1. 
The mouse tracking process is illustrated on Fig. 1. Firstly, the client requests the webpage from the server. Secondly, the server sends the webpage mainly in Hypertext Markup Language (HTML) and Cascading Style Sheets (CSS) embedded with the mouse tracking code written in client-side programming language. The client-side programming language used in this work is jQuery, which is a JavaScript (JS) library designed to simplify HTML Document Object Model (DOM) tree traversal and manipulation, as well as event handling, CSS animation, and Asynchronous JS and XML (Ajax) (jsf, 2019). Thirdly, the client’s browser views the retrieved webpage (HTML and CSS). Fourthly, the client’s browser executes the mouse tracking code. The clients actually have full control over the mouse tracking process because the programming is client-side based. However, they are usually unaware of this because the mouse tracking runs in the background. They would have to thoroughly inspect the background area to control the mouse tracking process. However, most clients do not attempt to perform this task. This is the reason why mouse tracking is considered non-intrusive. Fifthly, the mouse tracking code contains post methods to transmit the data to the server. The author designed the mouse tracking code to transmit data on each event (clicks, moves, scrolls, etc.) immediately (real-time). Sixthly, the server using server-side programming language receives the post data and connects to the database. In this work, the server-side programming language used is Hypertext Preprocessor (PHP) because Moodle and most other LMS are written in PHP. Finally, the mouse tracking data is stored on the database in form of Structured Query Language (SQL). ApplicationThe mouse tracking application developed as part of this work is a standalone application that can be implemented either on the server or on the client. In the case of the former, the mouse tracking code is incorporated into the webpage. A webpage mainly contains HTML, CSS, and JS. A more direct approach is to inject the mouse tracking code in the JS code. Another approach is to create a plugin for a certain content management system (CMS) or LMS. In this work, a Moodle mouse tracking plugin was developed, which can be in the form of an admin plugin, theme plugin, or a block plugin shown as shown in Fig. 2. A theme plugin usually applies to entire Moodle pages managed by the administrator while a block plugin applies to selected pages usually managed by managers and teachers. 
The mouse tracking Moodle plugin was implemented on the authors’ laboratory server, which can be accessed on https://md.hicc.cs.kumamoto-u.ac.jp. The authors planned to publish the Moodle plugin on Moodle’s website in the future. To implement the application on the client, the mouse tracking code is incorporated into the browser’s code. This can be achieved by direct insertion or plugin installation. Fig. 3 shows a mouse tracking browser extension installed on Google’s Chrome Browser. The authors plan to publish the extension in Chrome stores and other online stores. 
Implementation on a server is more efficient because the mouse tracking code is only installed on the server, whereas implementation on the client requires installation on each client. However, server implementation limits the mouse tracking process to the server’s website only. The authors were able to identify users as they visited or left the website but were unable to perform tracking once the users left the website. In comparison, client implementation facilitates the recording of every detail of the browser activity of users, including mouse tracking on all visited websites. FeaturesIn this section, the main features of the real-time online mouse tracking application are reviewed in detail. The guide for writing the code is available on jQuery’s website (jsf, 2019). Tracking is divided into the main event logging and other information loggings. A simple keyboard logging was also implemented. For mobile devices, a mouse is rarely used, therefore tracking of scrolls, touches, and zooms is preferred. Fig. 4 shows a demonstration of the loggings that are available online (Authors, 2019a). 
Event Loggings

Other Loggings
Other Features
Experiment and ImplementationThe real-time online mouse tracking application was installed on the author’s Moodle server. Three mouse tracking experiments were performed during which the clients participated in a ten-question quiz session on the server. The resource costs were then measured. The data rate of the network was measured using a tool called Wireshark. The default values for the CPU, RAM, and storage monitoring are available from the server’s operating system (OS) which is Ubuntu 18.04 LTS server. The server is equipped with an Intel(R) Core(TM) i7-6800K CPU @ 3.40GHz (with SSE4.2) CPU, 32 GB of DDR4 RAM, 10 TB of hard drive, and an allocated 2 MBps network. P2P Experiment
The first experiment was point-to-point (P2P) as illustrated in Fig. 6 where one client accessed the server directly without using the Internet. In this experiment, a laptop was directly connected to the server on an isolated P2P network to obtain clean data. The empirical data rate of one event (single click) was measured. As clean data were obtained, it was possible to derive a theoretical mouse tracking data rate. The other resource costs were not measured because the authors did not possess the necessary hardware, software, and knowledge to measure such small events. Local Experiment
The second experiment was a local experiment illustrated in Fig. 7 where five clients accessed the server through the Internet. This experiment was conducted inside the author’s laboratory. Five lab members including the main author tested the mouse tracking application and answered 10 questions during the quiz session. A resource costs profile of the five users was generated. There were no limits to the number of events per second that the clients were allowed to produce. Overseas Implementation
The third experiment was an overseas implementation illustrated on Fig. 8 where 44 clients in Mongolia accessed the server in Japan. Unlike the previous experiment, this was a real implementation where students from the School of Engineering and Applied Science, National University of Mongolia participated in a real quiz session on the server in the Human Interface Cyber Communication Laboratory, Kumamoto University. In this case, there was also no limitation in terms of events per second on the clients. Apart from determining the resource costs profile for the real quiz session, useful mouse tracking data was obtained. Although this work discusses the mouse tracking data and demonstrates some simple analysis, further analyses are out of the scope of this investigation. Result and DiscussionTheoretical Calculation from P2P Empirical Data
Table 1 shows the resource cost of the authors’ real-time online mouse tracking application for one event on the server, for a variety of information. This data applies to the P2P experiment in which the client performed one click on the Moodle server where mouse tracking was activated. As more information was included in the event, the data rate increased. The data rate revealed an increase of approximately 12 bytes when new information was added. This behavior is expected because an increase in the amount of information results in an increase in the post data size. For example, in Table 1 there was a significant increase in the data rate when the variable “date” and “content_url” were included because they contain more characters compared to other variables. The authors also attempt to measuring CPU and RAM activity but the change was negligibly small. Although the result is limited to this application only, similar results are expected for other existing applications. 
The addition of new data does not appear to significantly increase the data rate; however, this addition will be consequential as the number of users increases, especially when they perform many activities. The rate of mouse tracking activities is measured in events per second or frequency in hertz (Hz). Although the frequency of mouse movement and scrolling is high, usually, the rate does not exceed 70 events per second or 70 Hz (Rheem et al., 2018). Based on the empirical data obtained from Table 1, it is possible to estimate the data rate of the soon to be implemented mouse tracking. The first step in this process is to determine the number of events generated by users per second. Then the data rate is identified in Fig. 9 and multiplied by the number of users. The results revealed that it is possible for 1 MB of data to be generated from mouse activity in one minute (Leiva and Huang, 2015). From Fig. 9, when a user constantly generates five events per second (5 Hz), the data generated can reach 1 MB in approximately one minute. As previously stated, the real-time online mouse tracking application has a feature to limit the maximum number of events per second generated by a user. This can be set after allocating the network bandwidth of the mouse tracking process. Assuming that data are recorded for all available variables in mouse tracking if there are 22 users, and the network allocated to mouse tracking is 2 megabytes per second (MBps), the mouse tracking application should be limited to 25 events per seconds. However, this calculation is not realistic and is only relevant for measuring the worst-case scenario, whereby smooth implementation and not optimal resource usage is intended. This is because the events generated per second by users are dynamic and not static. For example, there are instances when the mouse cursor is not moved as the user stops scrolling to read. Likewise, there are instances when users move the mouse cursor and scroll to search for information. There are also occasions when users drag and drop objects during interactive activities. Consequently, users do not generate a fixed number of events per second. Profile Measurement from Local Experiment
To obtain more realistic data and to perform reliable calculation, profile measurements should be acquired. The main question that is considered in profile measurement is “how often do users move their mouse and scroll?” The profile measurement used in this work is resource monitoring during local mouse tracking processes by five users followed by statistical analysis on the time series data. Although the data required is the average events per second during the mouse tracking processes, it is more convenient to immediately measure the average resource costs. 


Unlike the P2P experiments, the local experiment measures not only the mouse tracking but also all the other processes, which includes accessing the Moodle page and answering 10 questions. During this experiment, the CPU percentage Fig. 10, the RAM usage Fig. 11, and the data rate Fig. 12 were rarely zero, indicating that idle activity was uncommon. For the local experiment with five users, the CPU percentage usage was an average of 10%, the RAM usage was an average of 1.7 GB, and the data rate was an average of 51 kB. This indicates that there was a reserve capacity for more users. It should be noted that the initial CPU percentage and RAM usage by the OS were 0% and 1.4 GB, respectively. An interesting result is shown in Fig. 12 for the data rate. During the quiz session at approximately 17:02:40-17:14:20 (11 minutes and 40 seconds, or 700 seconds), a table size of 6.1 MB with approximately 16287 rows (equivalent to 16287 events) and 17 columns were generated (note that the number of columns is less than the number of introduced variables in Table 1 because during this time, tracking for mobile device had not been developed. In addition, the total data transmission may not be equal to the size of the stored data on the database because of other factors such as the transmission methods, unoptimized application, and other factors apart from mouse tracking such as data transmitted when loading Moodle pages). Interestingly, the average events per second (16287 events divided by 700 seconds) was 23 or 23 Hz. If this data is plotted on Fig. 9, a result 78 kBps is obtained which is not far from the actual measurement of 51 kBps in Table 2. Can a single mouse swipe produce hundreds of mouse coordinates (Leiva and Huang, 2015)? The answer is “yes,” is we examine the spikes in Fig. 12. The highest spike occurred between 17:07:28-17:07:29 when 98 queries per second were received by the database. If plotted in Fig. 9, the result of 335 kBps is obtained which is close to the actual measurement where the maximum data rate from Table 2 is 312 kBps (unfortunately, name and email identification was not available at the time. Therefore, the identity of the users and the number of them who performed a large number of events is unknown). This shows that the speculation seems to be justified in the case where users are able to generate a high number of events per second momentarily. In other words, more than one user can perform many activities; mainly, simultaneous mouse moves and scrolls. The upper spikes are very large, as Table 2 indicates that the difference between median and maximum is large compared to the difference between median and minimum. Moreover, the spikes indicate that a very high level of activities only occurs momentarily and not constantly. Network and server administrators observed that mouse activities potentially generate a large amount of data. However, there was concern that this high level of activity is constant. The presented results clearly demonstrate that high-level mouse activity is mostly temporary. Overseas Implementation between Mongolia and JapanMouse Tracking Data and Sample Analysis
The authors were able to obtain mouse tracking data from 44 students in the School of Engineering and Applied Science, National University of Mongolia, for an online quiz session on the server in the Human Interface Cyber Communication Laboratory, Kumamoto University. Fig. 13 shows a screenshot of the mouse tracking data in form of a table. The table size is approximately 145 MB, containing 393585 rows and 22 columns. Are the rumors that mouse tracking produces a notoriously large amount of data true? The answer to this question is “yes.” A half year Moodle log data with a similar number of students was only approximately 300 kB, while the mouse tracking data represented in Fig. 13 was 145 MB after 3 hours and 30 minutes. The mouse tracking data contains so much information that a separate report is required to discuss the characteristics of the data and the types of possible analysis. There are many different types of analysis and discussions on mouse tracking data and several examples were reviewed earlier. In this report, sample visualization based on heatmaps and the trails of the mouse tracking data is presented, as shown in Fig. 14. As expected, left clicks occurred more often for selection of the questions. However, there were also left clicks associated with some of the questions and the visualization shows that the left clicks were dragged. This can be interpreted as highlighting the questions by the students. Middle clicks occurred most frequently for question four; however, the reason for this occurrence is not clear. Right clicks were most common on the top of the page, where some students probably decided to explore the available features. As expected, there were numerous trails such that it seemed that there were too much to visualize all at once. The heatmap indicates that most of the students placed the mouse cursor on the questions and choices. There were also few students who placed the mouse cursor outside the questions. Probably, these were individuals who preferred to keep the mouse cursor away from the text while reading. Further analyses are outside the scope of this work. Resource Costs of the Mouse Tracking Process


Similar to the local mouse tracking experiment with five users, the resource costs were also measured, allowing us to determine whether large-scale implementation is possible or not. Although 44 students attempted the quiz, the session was divided into two sessions and each session contained only 22 students. The students were informed that the first session would start at 12:00, followed by a break at approximately 14:00. The second session started a few minutes later and finishes at 15:30. As such, the entire process took 3 hours and 30 minutes (12600 seconds). The three Figures Fig. 15, Fig. 16, and Fig. 17 seems relevant to the informed schedule where a decrease in the graph was observed at 14:00 for a few minutes. The number of events generated during this time (12600 s) was 393585. The average number of events per second was 31 (393585 divided by 12600) or 31 Hz. When 31 Hz is plotted in Fig. 9, the result of 115 kB is obtained, which is close to the measured average data rate of 105 kB in Table 2. Is large-scale mouse tracking implementation possible? This is possible if resource usage is balanced and distributed. Implementing real-time mouse tracking is a better choice than implementing non-real-time tracking. For example, if mouse tracking is first accumulated and subsequently submitted all at once, this will cause a bottleneck at the server. Fig. 15, Fig. 16, and Fig. 17 would not show constant usage but would show idle activities at the beginning, which would become constantly high in the middle. This is arguably an inefficient use of resource. Real-time implementation helps to evenly distribute the transmission of the mouse tracking data. Compared to the local mouse tracking experiment with the five users, the resource costs are expected to increase because more users (22) were involved in this implementation, but there were more unexpected findings. The unexpected aspect is that the standard deviation is very high. As such, not only are there many positive spikes, but there are also many negative spikes, which further indicates that the number of events per second generated by the users is very dynamic. It should be noted that there was no limitation on the number of events per second that the students were allowed to generate. Based on Table 1 and Fig. 9, the data rate should increase in excess of 5 MBps for the worst-case scenario where 22 students simultaneously generate 70 events per second. However, this scenario never occurred as shown in Fig. 17, indicating high dynamics, and the very low probability of the worst-case scenario. In Table 2, not only does the standard deviation increase indicating high dynamics, the distance between the median and maximum also increases, as represented by the taller spikes. The highest spike occurred at 14:28:40 when 228 events were submitted to the server and surprisingly, this was attributed to only two users. This occurrence either contradicts the assumption of the authors that a user can generate up to 70 events per second or there was a delay in transmission, and the submitted events were incorrectly aggregated. When 228 events per second are plotted in Fig. 9, the result 849 kBps is obtained, which is close to the actual measurement in Table 2, where the maximum data rate during this implementation was 837 kBps. Conclusion and Future WorkThe first conclusion is that the online mouse tracking application was successfully implemented. The overseas quiz that was session monitored with real-time mouse tracking at the National University of Mongolia to Kumamoto University was successfully conducted and at present, mouse tracking is still running on the server. The mouse tracking data containing mouse clicks, mouse movements, and mouse scrolls was obtained, but the analysis of this data will be challenging because of the large size. Additionally, this demonstrates the possibility of tracking on a mobile device using scroll, touch, and zoom events. Are the rumors concerning high resource cost in mouse tracking true? Can a single swipe generate hundreds of mouse coordinates? Does mouse tracking over a minute generate in excess of a megabyte of data? Based on the result of this investigation, the answer to these questions is “yes.” In that case, is mouse tracking implementable on a large scale? The answer is also “yes.” One server with its specification highlighted in the Experiment and Implementation section was able to handle a classroom of users, and resource monitoring showed that there was much reserve capacity. Other institutions or corporations should have no difficulty in implementing mouse tracking because they typically have big data centers (large number of networks and servers, and distributed resources). For example, a corporation such as Google should not encounter difficulties, although this might be different for technologically challenged entities. The second conclusion is that mouse tracking is implementable if resource usage is distributed. In this work, the mouse tracking data were transferred in real-time to evenly distributed resource usage, instead of aggregating the data and transmitting them together, which may cause bottlenecks. Unfortunately, the nature of mouse tracking is such that it is difficult to predict. As such, it is challenging to determine resource allocation. The data acquired as part of this work showed the high dynamic characteristic of mouse activities, as reflected in the high standard deviations observed during monitoring of resource usage. When 22 students attempted the quizzes, the resource usage peaks were very high, but only temporarily. This was identified as spikes. Both upper spikes and lower spikes were observed, where upper spikes indicate momentary high-level activity and lower spikes indicate the opposite. If the amount of available resource is limited, then the resource cost of mouse tracking can be reduced. The mouse tracking application developed in this work can limit the number of events per second or frequency. Additionally, it can exclude unnecessary data. Moreover, even prior to this mouse tracking resource usage investigation, research on the compression of mouse tracking data already existed. This opens many paths for future work. Although real-time implementation assisted in the distribution of resource usage, the characteristics of the resource usage data showed how mouse tracking can potentially destabilize the system. The use of load balancing techniques can help stabilize the implementation. To achieve the minimum system requirement for mouse tracking, more experiments with different machine specification needs to be conducted. In addition, resource measurement on the client-side needs should be conducted to achieve the minimum system requirement for the client. Even though the developed mouse tracking application was able to limit activity level recording, the settings are still manually inputted. Adaptive settings are required for optimal usage. Although it was useful to conduct overseas implementation, more users and longer implementations are required to further evaluate the viability of real-time online mouse tracking. AcknowledgementsThe authors are very grateful to Muhammad Bagus Andra, Hamidullah Sokout, Irwansyah, and members of the School of Engineering and Applied Science, National University of Mongolia, for participating in the experiment. The authors would also like to thank Masayoshi Aritsugi, Hendarmawan, Hamidullah Sokout, Alhafiz Akbar Maulana, and Sari Dewi for inspiring this research topic. A special thanks to Muhammad Bagus Andra and Ni Nyoman Sri Indrawati for suggesting some interesting ideas. The authors would also like to thank Fahd Ouassarni for providing suggestions with respect to compressing the mouse tracking application codes. Finally, the authors would like to thank Alvin Fungai for initiating this research and for his assistance in proofreading. FundingPart of this work was supported by JSPS KAKENHI Grant-in-Aid for Scientific Research 19H1225100 and 15H02795. Conflict of interestsThe authors declare that they have no conflict of interest. Availability of Data and MaterialsThe datasets generated and/or analyzed during the current study are available in the Mendeley repository titled ’Data for: Implementation of Real-Time Online Mouse Tracking Case Study in a Small Online Quiz’. Reference
Mirror
Chapter 3 Findings In Japan3.1 Environment and City ManagementI found the city's management well organized. I've seen the business district has its own block. 
I've also seen the residential district and farms seperated. 

Overall the towns are clean. 
On 27th June 2013 from 09:30 – 11:00, we visited a recycling based town development Oki Town (Oki Town sustainable centre “Kururun”) and have a lecture of waste management there. Here the wastes are divided into 25 varieties. 
Today at this town 97% of its waste are recycled which means there is only 3% rubbish and the rest can be use for something beneficial. For example fertilizer, electricity from biogas, diesel from kitchen waste. It's also thanks to local town's folk support to relize this. In the future they're aiming for zero waste town. 
I found that Fukuoka is also rich in agriculture. On 27th June 2013 from 16:00 – 17:00 we have lecture of agriculture at Asakura City. They're currently focusing on creating healthy and tasty snacks made from fruits and vegetables. Their reasons for this it's because youths today eats more snacks (like chips) and less fruit. So they like to create healthy chips made from fruits and vegetables. 
3.2 Culture and PeopleMy first impression of the people when coming to Japan was they're strict with time. There's no tolerance of the word late in Japan. Everything is punctual. What I examine of how they can be punctual, it's because of subway train. Logically a subway train is clear channel transportation. Therefore the time of a subway train arrives is predictable and accurate. 
Even though they advance their technology but they still preserve their culture. On 25th June 2013 from 14:30 – 16:30 we went to Ohari Park to experience Noh Play ourselves. This play was founded around 700 years ago on the age of the Samurai. I asked whether the audience needed to understand Japanese in order to enjoy this play. The answered, it's played in classical Japanese even native Japanese people find it hard to understand. Even though there is lack in understanding this play can still be enjoyed just witnessing the performance and costumes, similar to watching Operah. 
From overall the Japanese people I have met, they're open, they really want to know of other peoples background and culture. The service that I witness there is very surprising. Every store I went to provides excellent customer service. The store clerks will always smile and says “irasshaimase” which is for welcoming someone whenever someone came. Most of the clerks have bright face when facing their clients. Other than that they also greet like “Ohaiyougozaimasu” which is Good morning. In the end they always thank their customer “arigatougozaimasu” which means thank you. Back to environment management, the people always keep their environment clean and tidy. They always throw their rubbish on the bin and arrange their surroundings well. On 27th June 2013 from 17:00 – 21:00 I have a home visit to Tanaguchi family. The entire family provides excellent hospitality even though we have trouble communicating because I could only speak Japanese a little. They're open people and likes to know how things are in my country. 
3.3 TechnologyMy first impression of the technology in Japan was advance. My group J is a science and technology group. Most of our programs are explorations of technologies in Japan. There are two that had been mention above which are subway train and recycling factory in Oki Town. The everyday technology I experienced was automatic toilet seat. 
The first program of technologies was on 26th June 2013 by NEXT Systems, Co., Ltd which was about stories behind its research and development, motion control system (Kinect in medical field, etc.) hands-on experience of Augmented Reality System, Kinect in fashion try-on, and Head Mount 3D Display. After that was demo of the technology. The first demo was AR of pamphlet and condominium. This technology works on android system by installing the application then connecting to the AR's network. Here I asked whether it needs its own connection or not. They answered they provided their on connection or it can be connected to the Internet. I also asked whether the current network capacity (most people called it bandwidth) is enough for today and future if all citizens are using this technology. They replied that technology is growing, today's current technology is enough but it's still growing, so it will be alright in the future. On my experience the android reads the 2D image then converts it to 3D or more detailed images. The second demo was virtual fashion demonstration where the person stands in front of the mirror and select virtual clothes to try on. The ideal technology is the same as trying clothes in changing room but virtually. So instead of wasting much energy on trying clothes in changing room, it's more energy efficient to use this virtual fashion mirror. This is also based on Kinect. The third demo was Kinect on mechanical of acceleration of cars. Kinect is an input device without any controller. Gestures lead to intuitive control. The picture is in 3D, the ideal technology is examining an object by touching except here is virtual. 


The second program of technologies was lectures of hydrogen energy project, organic photonics and electronics R&D base, and ruby contents related policy measures also promoting of digital contents industry utilizing programming language ruby by Fukuoka Prefectural Government. 
About the lecture of Hydrogen Energy is basically a fuel cell that generates electricity through the chemical reaction in which hydrogen and oxygen react to produce water and electricity. They said the energy produce is comparable to other electrical generator. The greatest advantage of this Hydrogen strategy is CO2 free. It doesn't produce CO2, so their future plan is CO2 free electrical power plants replacing those that generate high pollution. The next one was about organic EL display which EL stands for electroluminescence. Its main purpose is energy efficiency, since the material itself emits light so it saves the effort of emitting light, so it uses less energy. I asked on this session of how it compares to LCD. They have surprising answers which first of course it's much more efficient, second it's same cost to LCD, third it has same lifespan, and finally a shocking answer it has better performance than LCD (usually those with higher efficiency has lower performance). The next lecture it's about Ruby and digital industry content. Since time is limited they only introduce, and said they're recruiting undergraduates every year. The third program was about Oki Town Sustainable Centre “Kururun”, Recycling based town development which had already been explained in section 3.2. The fourth program was a company visit to Toyota Motor Kyushu. 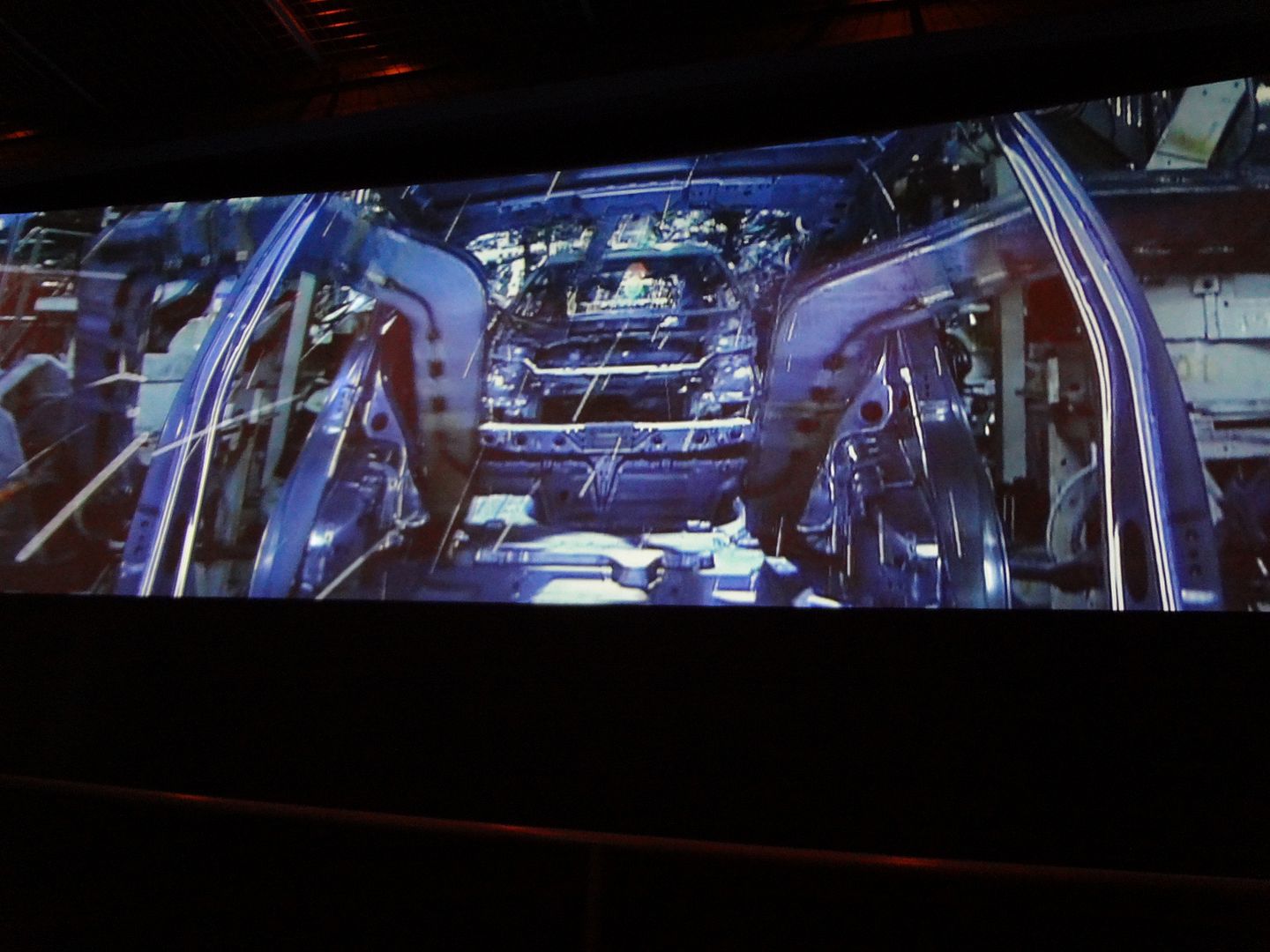
To be honest it was too much for me to comprehend and we're forbid to take photos, but what I captured was they work with excellent system. We took tour on a real field of how cars are produced from zero until made. Their workers are humans and robots. What I saw, parts were carried by robots, and some simpler assembling was also done by robots. Other jobs and complicated assembling were done by humans. Their work was very systematic. Each phase of assembling are done by different people, with each phase has its time limit. If a worker encounters problems which cannot be solved within the time limit, the worker rings the bell and the flow will be stopped and others will come to help. After each phase of assembling there's an inspection and all data are recorded. The fourth program was about Agricultural produce in Asakura Technological development of Agri-Processing, already written on section 3.2. The last program regarding on technology was a visit to Kyutech (Kyushu Institute of Technology). We were divided into 2 groups 1 to go the Mechanical Engineering Laboratory. I chose to go to Laboratory of Spacecraft Environmental Interaction Engineering. I captured that on that laboratory they research on Spacecraft Environmental Interaction through artificial Space they created in tubes. In those tubes are artificial Space base on real Space. They conduct many kinds of experiments there. 
Chapter 4 Contributions And Future Plans Of This Program4.1 Mission of This ProgramDuring the program there were few lectures that explained to us the mission of this program. First was program orientation on 23rd June 2013 from 14:00 – 17:00 at Hotel Nikko Narita. Second was lecture by ASEAN-Japan Center on 24th June 2013 from 10:00 – 11:30 at National Olympics Memorial Youth Center, Tokyo. Third was lecture by Fukuoka Prefectural Government of outline of Fukuoka Prefecture and exchange with ASEAN on 26th June 2013 from 14:00 – 17:00 at Fukuoka. Last one was workshop report presentation on 29th June 2013 from 16:00 – 17:00 at Symphonia E, 3F, TKP, Garden City Chiba (we did our workshop the day before). Overall the programs metioned above I derived that the mission of this program is to prepare for ASEAN integration in 3 pillars (stated in chapter 1) on 2015 and Japan wants to join in. With each group’s participants are from 10 different countries of ASEAN, we are to establish links between ASEAN countries with the first step befriend with participants in our group. The program also told us to establish links between ASEAN and Japan. We are to carry on ASEAN – Japan Centre’s will which is to promote export from ASEAN to Japan, to accelerate the flow of investment between ASEAN and Japan including the transfer of skills and technology, and to vitalize tourist traffic between ASEAN and Japan. 4.2 Currently Possible ApplicationsI have befriended with all participants in my group, also with some others outside my group. Even up to today we’re still in contact almost daily through social media. 
What I privately captured from this program is a mission to link my friends and everyone else in my home country to those links that I have established during this program. Since my backgrounds are in Electrical Engineering and ICT (Information Communication Technology) I would like to do this task using methods base on my backgrounds. I’d like to promote and I have already started of ASEAN and Japan through websites to first my friends. Since I just started I have promoted these websites below to around 10 of my friends at my home country. I planned to promote them to everyone I know. For Facebook I’ll ask my friends to like, for Twitter to follow, and for web pages I’ll ask to bookmark.
As I stated above I have befriends with many people on this program from both ASEAN countries and Japan. It’d be better if I don’t keep it to myself so I’d like to introduce them to friends in Indonesia (ASEAN-Japanese friends to Indonesian friends). At least I should introduce but I’ll also ask them to introduce themselves and interract with the friends I met on this program (Indonesian friends to ASEAN-Japanese friends). I’d like to do this through ICT (Information Communication Technology). The beginning step is through social media such as Facebook and Twitter. I planned to show them the friends I made through this program. Then through posts I planned that they would introduce themeselves. The picture below shows that I never though my friends would be daring, it’s great though. 
Next it would be nice that they could befriend at take the relationship to the next level throught chats. Finally, the last step I have in mind is they would interract daily through video conference, through Skype, facebook video call, yahoo messenger video call, etc. Today video call is the closest telecommunication to face-face conversation. That’s how far I could go as bridge between my friends in Indonesia and ASEAN-Japanese friends. I can only go as far as using free services because of economic limitation. Other than electricity, the hardware and software itself, and some paid internet services, accessing websites, social media, VOIP (Voice Over IP), and video calls are free. 

I will also share my experience by uploading my report on my blog https://0fajarpurnama0.github.io/bachelor http://blog.unud.ac.id/fajarpurnama (obselete) and other things such as photos, although all the photos I have uploaded on Facebook. I will volunteerly link or upload informations base on this program. Experiences such as the NOH play that I experienced, vist of NEXT Systems, Co., Ltd, lectures of Hydrogen Strategy, lectures of EL, lectures of Ruby and Digital Industry, visit of Recycling Center in Oki Town “Kururun”, visit of Toyota Motor Kyushu, lecture of agriculture in Asakura, home visit with Tanaguchi Family, visit of Kyutech, and the mission of this program from overall lectures and programs 
4.3 Ideas Not Currently ApplicableThis section is ideas that today I cannot do which will remain for now as ideas. Still it’s some ideas that may prove beneficial but I alone for now could no accomplish due to limitation of economy and power. My first idea is to establish a curriculum in education of establishing links between ASEAN countries and ASEAN to Japan. Why I stated this because just by providing facilities such as socialmedias and websites will not maximize the benefit of these facilities. There are lots of people who will not use these facilities unless these facilities are socialized, even more unless these people are told to. So I recommend that there will be a curriculum. There will be more socialization of establishing links between ASEAN countries and ASEAN to Japan, there will be lectures, and there will be task for students to access websites regarding to establishing links between ASEAN countries and ASEAN to Japan and making friends with people from outside home countries to socialmedias. My second idea is to have more joint lectures between different regions and different countries via video conference, more seminars and more workshops through video conference. So I suggest there will be more video conferences between regions and countries. My third idea is to promote more information regarding to ASEAN and Japan through local medias which are radio and television. My fourth idea is to teach the young generations to be openminded. Openminded is the key for relationships between different people to succeed. My fifth idea is an R&D (Research and Development) on face to face technologies, whether it’s an affordable technology that makes long range telecommunication has the same quality as face to face communication or build a global affordable transportation so people can travel to other countries daily (people can afford to go to different countries everyday). 4.4 Future Benefits of These PlansIf these plans are relized then maximum acceleration of economic, exchange, and tourism flow can be achieved. Daily relationship will widen greatly, we not only interract with among our people but we will interract with other people from different background everyday. Real international school will be relized. For example like my primary school in Australia called Daceyville Public School. Back then my friends are not only natives Australian, but I have friends from Korea, China, Phillipin, Iran, India, and many others from all over the world. If each School has students from Indonesia, Japan, Philipin, Malaysia, Brunei Darusalam, Vietnam, Thailand, Laos, Myanmar, and Cambodja then there will be no more challenge of integration. In other words we succeeded. Growth on prosperity will be accelerated. It will be an even more fun world to live in. Other nations will follow us and sees us as an example.
Mirror
Using real-time online preprocessed mouse tracking for lower storage and transmission costs2/6/2020 NoteThe original article was granted open access licensed under creative commons (CC-BY) where you are free to copy, reuse, modify, distribute, commercial, etc, but required to give full citation:
Althought it is already fully available online, I would like to rewrite it in .html and share to as many platform as possible. Who knows if the original site goes down? Also, I have a circumstance to read it all over again and why not rewrite it at the same time to make it more fun. Eventhough the original is licensed CC-BY but the rewritten version I will license as customized CC-BY-SA where you are also allowed to sell my contents but with a condition that you must mention that the free and open version is available here. In summary, the mention must contain the keyword "free" and "open" and the location such as the link to this content. AbstractPageview is the most popular webpage analytic metric in all sectors including blogs, business, e-commerce, education, entertainment, research, social media, and technology. To perform deeper analysis, additional methods are required such as mouse tracking, which can help researchers understand online user behavior on a single webpage. However, the geometrical data generated by mouse tracking are extremely large, and qualify as big data. A single swipe on a webpage from left to right can generate a megabyte (MB) of data. Fortunately, the geometrical data of each x and y point of the mouse trail are not always needed. Sometimes, analysts only need the heat map of a certain area or perhaps just a summary of the number of activities that occurred on a webpage. Therefore, recording all geometrical data is sometimes unnecessary. This work introduces preprocessing during real-time and online mouse tracking sessions. The preprocessing that is introduced converts the geometrical data from each x and y point to a region-of-interest concentration, in other words only heat map areas that the analyzer is interested in. Ultimately, the approach used here is able to greatly reduce the storage and transmission cost of real-time online mouse tracking. IntroductionWe are living in the age of information where information and communication technologies are becoming mainstream [1]. Computers and the Internet have become inseparable from our daily lives. It is now possible to do many things without the need to travel and wait; examples include, long-distance communication through online text, voice and video calls, social interaction via social media, online learning, ecommerce or online shopping, and many forms of entertainments such as online music, online videos, and online games. Most importantly, the Internet has become the primary source of information around the world. We are living in the age of information where information and communication technologies are becoming mainstream [1]. Computers and the Internet have become inseparable from our daily lives. It is now possible to do many things without the need to travel and wait; examples include, long-distance communication through online text, voice and video calls, social interaction via social media, online learning, ecommerce or online shopping, and many forms of entertainments such as online music, online videos, and online games. Most importantly, the Internet has become the primary source of information around the world. We are living in the age of information where information and communication technologies are becoming mainstream [1]. Computers and the Internet have become inseparable from our daily lives. It is now possible to do many things without the need to travel and wait; examples include, long-distance communication through online text, voice and video calls, social interaction via social media, online learning, ecommerce or online shopping, and many forms of entertainments such as online music, online videos, and online games. Most importantly, the Internet has become the primary source of information around the world. Although eye tracking remains a tool for the laboratory, an alternative method has been invented, mouse tracking [7]. Instead of eye movements, mouse tracking tracks mouse movements and other helpful events. The fundamental strategy of mouse tracking is the recording of mouse clicks, mouse movements, and scrolls. Eye and mouse tracking have been implemented in the fields of education [8, 9], reading patterns [10], search engines [11], visual navigation [12], web evaluation and usability [13, 14]. Mouse tracking can be treated either independently [15] or as a correlation to eye tracking [16] in other words, as replacement. The biggest problem with default mouse tracking (as well as eye tracking) is the huge volume of data generated, which can be categorized as big data [17, 18]. This high volume is due to the use of geometrical data where each event that occurs on each point of the webpage is recorded. If the distance between left and right is 1000 pixels, then a swipe from left to right will generate 1000 rows of tables. However, analyst may not need all of the mouse tracking data that is generated. Therefore, this paper proposes preprocessing the data based on the analyst’s needs. The preprocessing in this case determines the region of interest in other words; which area the tracking should capture rather than capturing each point of interest. Furthermore, the preprocessing is conducted not only online, but also in real-time mouse tracking session. Related WorkImplementations of eye and mouse trackingThe use of eye [19] and mouse [20] tracking began in the early 20th century, and since then, there have already been many laboratory experiments conducted using these technologies. Today, there are many attempted implementations of eye and mouse tracking, but it is unclear how widespread and long-running they are. For eye tracking, there is no chance of implementation outside laboratory unless one of two requirements is met: (1) affordable and mainstream hardware [6] or (2) optimal usage of web cameras [21, 22] on laptops and/or cameras on smartphones. By contrast, widespread implementation of mouse tracking is already possible because the required hardware is available by default in all computers and smartphones, but the problem is the generation of big data (the same is true of eye tracking as well). The following are selected attempts at implementation eye tracking:
The following are selected attempts at implementation mouse tracking:
Some commercial and open source software programs are as follows:
Mouse tracking in web developmentThe core of mouse tracking in web development is document object model (DOM) which is an application programming interface (API) for Hyper Text Markup Language (HTML) and Extensible Markup Language (XML). It defines the logical structure of documents and the way a document is accessed and manipulated. Supposed a simple HTML page with the codes on Table 1, the DOM structure can be represented on Fig. 1. With the Document Object Model, programmers can build documents, navigate their structure, and add, modify, or delete elements and content. Anything found in an HTML or XML document can be accessed, changed, deleted, or added using the Document Object Model, with a few exceptions. DOM is designed to be used with any programming language. Currently, it provides language bindings for Java and ECMAScript (an industry-standard scripting language based on JavaScript and JScript) [36]. Table 1 A web page code in simple HTML that contains html, head, title, body, p, and footer tags <html> <head> <title>Simple Webpage</title> </head> <body> <p>Hello World!</p> </body> <footer> <p>CC</p> </footer> </html> 
The implementation of mouse tracking is based on DOM events, specifically mouse, touch, and user interface (UI) events which are actions that occurs as a result of the user’s mouse actions or as result of state change of the user interface or elements of a DOM tree [37]. Our previous work [31] uses jQuery to access the DOM API and receives information that are related to mouse, touch, and UI events. They can be stored into default dynamic variables or in an ArrayBuffer for enhanced performance. The list of events are as following:
The information is then processed by adding important labels such as the date of the received information and duration by calculating the difference between the current and previous received events. Finally the information is either stored locally or sent to a server using hyper text transfer protocol (HTTP) post method. Traditionally, the information is transmitted all at once at the end of the session, but in our study [31], we found that it is better to transmit them in real-time without delay. The difference between offline, regular online, and real-time online mouse tracking is shown in Fig. 2. 
Default eye and mouse tracking generates big dataAlthough eye and mouse tracking are not yet mainstream, rumors spread that due to large amounts of data generated, they could not be widely implemented other than at big corporations such as Google and Microsoft, which have gigantic data centers. University network and server administrators are hesitant to implement tracking technologies because they not only generate massive amounts of data, but also eye and mouse tracking are not replacements for existing systems but rather additions. Huang et al. [11] performed a mouse tracking experiment on Bing’s search engine and immediately reduced the sampling rate because the data were too large. Leiva and Huang [38] believed that a swipe could generate a megabyte of data and the authors further investigated and proved that rumor to be true. While a half-year of Moodle log data with approximately 40 students is only approximately 300 kilobytes (kB) [39], mouse tracking data and other event data generated by approximately 22 students reaches approximately 100 megabytes (MB) in only 2 h [31], and that figure will double if eye tracking is included. Imagine how much data would be produced by a university with a large number of students if mouse tracking were running on its website for years. According to an article by Adekitan et al. [40], Nigerian University Internet traffic can reach terabytes (TB) in a week and is regarded as big data. The authors’ previous mouse tracking session [31] also reaches the same level of Internet traffic if over 100 students are present. Other than volume, mouse tracking met the other 5Vs criteria of big data [17]: velocity, the amount of data generated especially in real-time which is explained in further sections, veracity; meaning that data loss may often occur due to limited connectivity, which can lead to inconsistent data; variety, which is discussed in further sections and previous work [31]; and value, which is discussed in the next paragraph. It would be wise to start investing in eye and mouse tracking just as big companies today are investing in big data [41], as the data generated by eye and mouse tracking are valuable. By analyzing big data, interesting information can be derived that gives us the knowledge needed to make optimal decisions [42]. Just as companies study customers’ data to find opportunities to increase their revenues [43], traders analyze historical trading data and current sentiments to find optimal positions [44], researchers study optimal prevention, diagnosis, and treatments in Medicare [45], and planners monitor smart cities [46], researchers can use eye and mouse tracking to identify online viewers’ attention, behavior, their evaluation of web contents, etc. Reducing eye and mouse tracking dataDuring high-intensity activities, a user may generate an average of 70 or 70 events per second [47], meaning that 70 rows per second will be generated on a table. The traditional way of reducing the size of these tracking data is by reducing the sampling rate [11]. Furthermore, the sampling rate should be adaptive and not static. In other words, snapshots should only be taken when an event occurs such as when the mouse cursor moves or a click occurs, and snapshots should not be taken during idle sessions. Performing transmission in real-time helps distribute the transmission burden across time, avoiding bottlenecks. In other words, the tracking data are immediately transmitted to the server at each event occurrence rather than transmitting the mouse tracking data all at once at the end of the session. Compression methods can also be utilized as demonstrated in Leiva and Huang’s work [38], but their transmission method is still likely not real-time and is suspected to transmit the compressed tracking data all at once in the end of each session. On the other hand, the preprocessing technique presented in this paper is designed to work in real-time. Not only does it reduce the data cost but also distributes the transmission burden across the time domain. The cause of the enormous data generation is the geometrical data or tracking of each location where the events occur, in other words the x and y coordinates. Tracking these coordinates provides rich data but sometimes all of that data is not needed. For example, Rodrigues et al. [28] only analyzed the amount of key up, key down, mouse down, mouse up, mouse wheel, and mouse movement to measure students’ stress, and Li et al. [48] only needed the time spent on each page. In such cases, the geometrical data can be omitted. At other times, geometrical data are needed; however, it is not each precise x and y point that is needed but rather each area of the page (multiple points) [49]. Preprocessing is common in any data analysis to derive useful data prior to transmission and storage of the collected data. However, the preprocessing presented in this work is performed on the client before transmission and storage to reduce the server’s burden. Unlike typical preprocessing which is performed to filter redundant data, the preprocessing in this work is specifically based on the demands of the administrators or analyzers; in this case, preprocessing omits the geometrical data or groups them to represent certain areas. This study is a complete work of one the author’s previous works [50]. Method and simulationSystem overview
The overall system is the same as in the authors’ previous work [31] with the concept discussed in "Mouse tracking in web development" section. In this section, the implementation of the concept to system is discussed. As shown on Fig. 3, mouse and other event tracking are performed on the client. The tracking codes can be injected internally, for example, as a browser plugin, or externally, for example, where the codes are retrieved alongside the webpage content [HTML and cascading style sheets (CSS)]. Then, the client sends the tracking the data to the server to be stored. The code itself for this work is written in jQuery, which is a simpler coding format of JavaScript for DOM manipulation. The external code can be written as a plugin if desired; for example, the authors wrote a Moodle plugin. The server side can be in any programming language, but in this work, PHP was used, and the database used MySQL. The codes are available on GitHub [32]. Each web framework may developed their own bindings to access the DOM API. However, the most fundamental implementation is still injecting the mouse tracking code into the script section no matter which web framework is used, which is the default option if the web framework did not developed their own bindings. Below is a list of few web frameworks:
Three techniques of mouse tracking
For convenience, the techniques of mouse tracking are divided into three types, as shown in Table 2. They are called default mouse tracking, whole page tracking, and ROI tracking. The default mouse tracking precisely records the geometrical data of the event occurrence such as the horizontal x and vertical y of left clicks, right clicks, middle clicks, mouse movements, scrolls, zooms, and if desired keyboard types. The duration between each event is also measured. Whole page tracking omits the geometrical data and summarizes the number of left clicks, right clicks, middle clicks, mouse movements, scrolls, zooms, and if desired keyboard types that occurred on the webpage. In other words, the amount of activity is measured but not where or when it occurs, and only the total amount of time that the user spends on a webpage is recorded. The most complicated task is ROI tracking, which is a gray area between default mouse tracking and whole page tracking. ROI tracking defines the areas of a webpage to be tracked, for example how many left clicks, right clicks, middle clicks, mouse movements, scrolls, zooms, and keyboard types occurred and how long they occurred on a header, menu, content, footer, etc. This method is ideal because it meets the analyst’s requirements and reduces unnecessary resource costs, but the drawback is the heavy labor required to manually define the areas of each webpage. Automatic area definition is possible to certain degree. One way is by attaching “mouseenter” DOM event listener to every element and using “offset” DOM HTML to return the position of the element. Offset DOM HTML returns the left and top element distance from the outermost of the webpage, and by using “width” and “height” DOM HTML to calculate the element’s size, it is possible to find the bottom and right as well. However, the limitation is that it cannot perform smart labelling where it can only extract attributes, texts, and values of the element. An illustration comparing the three types of mouse tracking is shown in Fig. 4. 
Whole page vs region of interest vs default mouse tracking illustration. The left scroll illustrates whole page tracking that summarizes the number of events occurring on the whole page; the middle scroll illustrates ROI tracking that summarizes the number of events occurring in defined areas, and the right scroll illustrates default mouse tracking that records every event and the precise point where it occurs, forming a trajectory 
The flowchart for each implementation of real-time and online mouse tracking is shown in Fig. 5. For default mouse tracking, the information on the event is transmitted to the database each time an event occurrs. For example, when a click occurs, the client immediately transmits the information on where and when it occurs. For whole page tracking, the information is summarized as the number of events that occurred, and they are transmitted to the server when the client closes the webpage. The size of the transmitted data is only slightly larger than that of transmitting single click data when using default mouse tracking. Last, for ROI tracking, the information on the webpage area is summarized and transmitted after the mouse cursor leaves the area, and the process repeats on each movement between areas until the webpage is closed. SimulationThe three mouse tracking method are tested on the client and server. Since the author lacks subjects to perform an implementation, a simulation based on previous mouse tracking data was conducted on the server. The mouse tracking data contain mouse tracking records from two quiz sessions in Moodle. They were conducted on the 3rd of January 2019 between approximately 12:00 and 14:30 Japan standard time. There are 2 sessions, with each session lasting approximately an hour and including 22 students (44 total students participating) from the School of Engineering and Applied Sciences, National University of Mongolia accessing the Moodle server at the Human Interface and Cyber Communication Laboratory, Kumamoto University. The data were preprocessed to exclude nonstudents and webpages other than the quiz page data. In other words, the simulation is purely a mouse tracking data transmission, which excludes most of the process, such as accessing the server and navigating the whole Moodle page. This approach shows lower resource consumption than the previous work [31]. 
The setup can be seen in Fig. 6 where a laptop functioning as a client is peer to peer connected to a personal computer functioning as a server. The mouse tracking data are converted into page tracking and ROI tracking data based on Table 2. Three sessions were conducted: the first session was the sending of mouse tracking data to the server, the second session was the sending of page tracking data to the server, and the third session was the sending of ROI tracking data to the server. Since the mouse tracking data contain time interval information between the sending of each event, it is possible to capture the scenario almost exactly. During these sessions, the data rate is observed, and the central processing unit (CPU) and random access memory (RAM) usages are measured on the server. Figure 6 shows that one laptop serves as a client to send the data to the server which is a personal computer. The client is an MSI Laptop with i7-7820 HK 2.9 gigahertz (GHz) x8 32 gigabyte (GB) RAM while the server is an i7-6850 HK 3.6 GHz x12 32 GB RAM personal computer and the peer to peer connection is a 10 megabyte per second (MBps) network. For the client testing, the author performs the quiz session recorded by mouse recording software GhostMouse in order to replay the exact mouse events for the three mouse tracking types and for different browsers. The testing time are short around a minute due to the limited profiling time of the browsers. The performance which is only the JavaScript total running time of four different browsers are measured:
Result and discussion
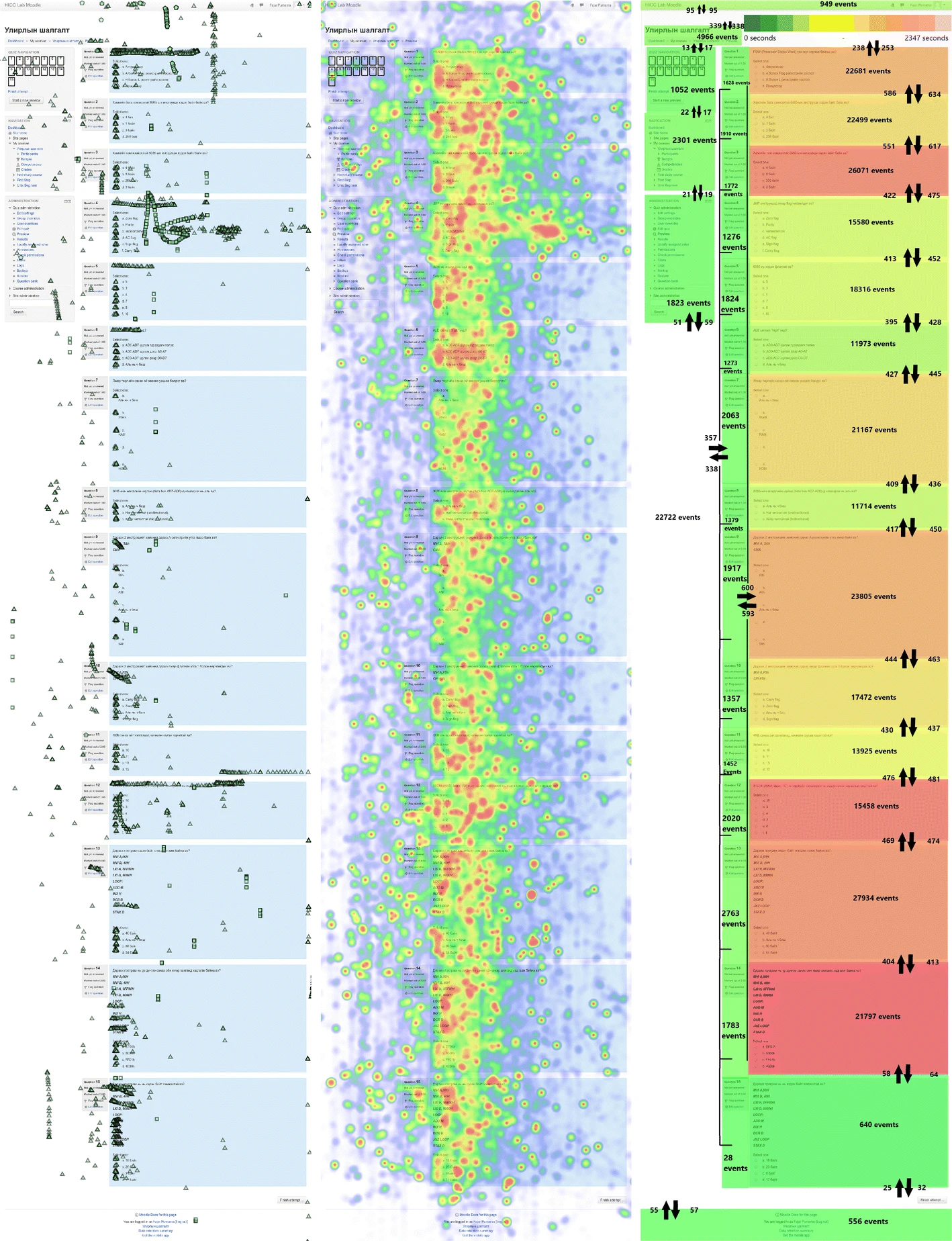




Default mouse trackingIt is well known that the advantage of default mouse tracking is the detailed and precise data it generates. An example is shown in Table 3. The exact x and y points of the locations of event occurrences, such as left clicks, right clicks, middle clicks, mouse movements, scrolls, zooms, and keyboard types, are recorded, including when and for how long each event occurs. Those geometrical data (x,y) make it possible to reproduce the mouse trajectory shown in Fig. 7, and adding the time information enables the trajectory’s replay. The rumored disadvantage is the huge transmission and storage cost, and this seems to be true judging from Figs. 8, 9 and 10. For the 22 students in each session, the transmission resource cost statistics are shown in Table 4. The average data rate was 28 kilobytes per second (kBps) and was able to peak to 228 kBps. For the two sessions totalling 44 students, the data size was approximately 100 MB and Table 3 has 286511 rows. The CPU usage was hightly consumptive as well, while the RAM usage was not as consumptive. Even worse, mouse tracking is not a replacement for the existing logging method but rather an addition; in other words, it is expected to add an additional burden to the existing system if mouse tracking is implemented. These data were generated from a 2 1/2 h mouse tracking session; thus, imagine how much resource mouse tracking would consume if it were run on a university scale with thousands of students for 24 h daily. On the client the side, this method also shows the highest total JavaScript running in Fig. 11 among the other methods. It is suspected due to the large amount of HTTP Post to the server. Webpage summarized mouse trackingBy omitting the geometrical data (x,y) and summarizing the numbers of events that occurred, the data became as small as possible, as shown in Figs. 8, 9, 10 (although they can be further reduced slightly by compression and removal of unnecessary characters and variables). The table was reduced to one row per webpage visit; in this case, Table 3 with 286511 rows was reduced to 26 rows, as shown in Table 5. As shown in Table 4, the data size was reduced from 100 MB to 16 kB. The average data rate was reduced from 28 kBps to 10 Bps. Although there is still RAM usage, CPU usage is slightly visible. Among the three mouse tracking methods mentioned in this work, this technique is the most advantageous in terms of resource cost. On the client the side, this method also shows the lowest total JavaScript running in Fig. 11 among the other methods. It is suspected due to the few amount of HTTP Post to the server. However, the disadvantage compared to the three mouse tracking techniques is that it provides the poorest information that makes it impossible to create any visualizations, as shown in Fig. 7. The information tells only how many events (such as left clicks, right clicks, middle clicks, mouse movements, scrolls, zooms, and keyboard types) occurred and the length of time that the user spends on the webpage. Nevertheless, the information is richer than traditional logs, as shown in Table 5. Region of interest mouse trackingThis technique is the best of the three, as the desired information is based on the analyst’s preferences, and there are lower resource costs than in the default mouse tracking shown in Figs. 8, 11. Analysts chooses the areas to be analyzed. In this case, the authors defined the following areas for the quiz session: header, title, menu, footer, and each question section. It can be seen in Fig. 7 that it is possible to create heatmaps of high activity areas, although it is not possible to create precise mouse trajectories as default mouse tracking, but it is possible to capture amounts of movement between areas. The duration is also based on each area. The data size is 5.4 MB with 19062 rows shown in Table 6. As shown in Table 4, the average data rate is 2.28 kBps and the average CPU and RAM usage are 0.87% and 1.85 MB which are lower than in default mouse tracking. Based on the algorithm of this method, the resource cost should be based on the number of defined areas, where the more areas, the larger the resource cost (note that default mouse tracking cost the largest because the webpage has been divided into the smallest possible areas, which are the x and y points of a webpage). This technique is the best of the three, as the desired information is based on the analyst’s preferences, and there are lower resource costs than in the default mouse tracking shown in Figs. 8, 11. Analysts chooses the areas to be analyzed. In this case, the authors defined the following areas for the quiz session: header, title, menu, footer, and each question section. It can be seen in Fig. 7 that it is possible to create heatmaps of high activity areas, although it is not possible to create precise mouse trajectories as default mouse tracking, but it is possible to capture amounts of movement between areas. The duration is also based on each area. The data size is 5.4 MB with 19062 rows shown in Table 6. As shown in Table 4, the average data rate is 2.28 kBps and the average CPU and RAM usage are 0.87% and 1.85 MB which are lower than in default mouse tracking. Based on the algorithm of this method, the resource cost should be based on the number of defined areas, where the more areas, the larger the resource cost (note that default mouse tracking cost the largest because the webpage has been divided into the smallest possible areas, which are the x and y points of a webpage). Conclusion and future workPreprocessing mouse tracking data during real-time and online sessions helps reduce the storage and transmission costs and unexpectedly the JavaScript total running time on the client’s browser as well. The techniques presented in this work are whole page tracking and ROI tracking. Although the amount of reduced data is very dependent, there are fixed theories. The fixed theories are as follows: whole page tracking reduces the mouse tracking data into one row of tables per webpage visit, and ROI tracking reduces the data into one row of tables per area visit. Selecting the right technique can help reduce the storage and transmission costs while still obtaining the necessary data. Although this concept works perfectly, but there are still problems with execution. Whole page tracking transmits the data only when the user leaves the page, and if the problems lie with the browser, there is currently no way to tell the user to wait before the transmission process finishes. There will definitely be cases where data are not fully transmitted. The problem for ROI tracking are that it cannot perform smart area definition and labelling. Normally, they are performed by humans. Therefore, one solution is to develop an artificial intelligence for this matter in the future. Availability of data and materialsThe datasets generated and/or analyzed during the current study are available in the Mendeley repository titled ’Data for: Implementation of Real-Time Online Mouse Tracking Case Study in a Small Online Quiz’ in ’Pre-processed Mouse Tracking Data’ directory [61]: Tables 3, 5, 6 data are available in file mouse_tracking_mongolia_anonymous.ods [62]. Figures 8, 9, 10 and Table 4 are based on files: cpurammousetracking.txt [63], cpurampagetracking.txt [64], cpuramroitracking.txt [65], mousetrackingsimulationpcapng [66], pagetrackingsimulationpcapng [67], roitrackingsimulationpcapng [68]. Abbreviations
References
AcknowledgementsThe authors would like to express their deepest gratitude to Otgontsetseg Sukhbaatar, Lodoiravsal Choimaa, and their students for participating in the mouse tracking quiz session. This manuscript has been proofread by Springer Nature Author Services. FundingPart of this work was supported by JSPS KAKENHI Grant-in-Aid for Scientific Research 19K1225100 and 15H02795. Author informationFajar Purnama and Tsuyoshi Usagawa are contributed equally to this work AffiliationsGraduate School of Science and Technology, Kumamoto University, 2 Chome-39-1, Kurokami, Chuo Ward, Kumamoto, 860-8555, Japan Fajar Purnama & Tsuyoshi Usagawa ContributionsBoth the authors have participated since the beginning of the work. The main author wrote the manuscript, and the co-author revised the manuscript. Both authors read and approved the final manuscript. Authors’ informationFP is currently a doctoral student at Graduate School of Science and Technology, Kumamoto University. His research area is in the field of educational technology. TU joined Kumamoto University in 1983 right after he received an M.E. degree from Tohoku University. In 1988, he received a Dr. Eng. from Tohoku University. Since 2004 he has been a professor, and he is a member of the IEEE, ASA, ASJ, INCE/J, JSET, and JSAI. He is interested in e-learning contents and systems, and acoustic signal processing. Corresponding authorCorrespondence to Fajar Purnama. Ethics declarationsCompeting interestsThe authors declare that they have no competing interests. Additional informationPublisher's NoteSpringer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
Archives
August 2022
Categories
All
source code
old source code Get any amount of 0FP0EXP tokens to stop automatic JavaScript Mining or get 10 0FP0EXP tokens to remove this completely. get 30 0FP0EXP Token to remove this paypal donation. get 20 0FP0EXP Token to remove my personal ADS. Get 50 0FP0EXP Token to remove my NFTS advertisements! |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||


 RSS Feed
RSS Feed

